How to delete your Twitter account (and back up your tweets)
Credit to Author: Alex Perekalin| Date: Mon, 10 Dec 2018 10:00:07 +0000
Ready to delete your Twitter account? Here’s how. But you’d better back up your tweets first.
Read moreCredit to Author: Alex Perekalin| Date: Mon, 10 Dec 2018 10:00:07 +0000
Ready to delete your Twitter account? Here’s how. But you’d better back up your tweets first.
Read moreCredit to Author: Jeffrey Esposito| Date: Thu, 15 Nov 2018 13:25:16 +0000
In this edition of the Kaspersky Lab podcast, we discuss a targeted cryptocurrency scam, Canadian weed database breached, bio chips, and the current state of spam and phishing.
Read moreCredit to Author: Alex Perekalin| Date: Tue, 13 Nov 2018 17:02:06 +0000
Twitter cryptocurrency scams are becoming more and more advanced and convincing, with scammers using new techniques and some heavy artillery.
Read more
Credit to Author: Naked Security| Date: Mon, 22 Oct 2018 16:32:06 +0000
¿Eres uno de los muchos usuarios de Twitter que has recibido un mensaje extraño como el siguiente? Does anyone know what this twitter notification could possibly mean? https://t.co/iY6hQNLOgy— Nigella Lawson (@Nigella_Lawson) October 16, 2018 Los mensajes consistían en una larga cadena de lo que parecían números y letras aleatorios. Se trataba de algo tan misterioso […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/oO7OYGiwQCE” height=”1″ width=”1″ alt=””/>
Read moreCredit to Author: Malwarebytes Labs| Date: Mon, 22 Oct 2018 16:23:14 +0000
 | |
| A roundup of the security news from October 15–21, including how to build your own security camera, the FIDO standard, Twitter information operations, and our Q3 CTNT report. Categories: Tags: a week in securityCTNT reportfacebookfidograndcrabgreyenergyoceansaltpentagonsecurity camerastwitter |
The post A week in security (October 15 – 21) appeared first on Malwarebytes Labs.
Read moreCredit to Author: Christopher Boyd| Date: Thu, 18 Oct 2018 15:00:00 +0000
 | |
| New information released by Twitter sheds fresh light on the various professional troll campaigns deployed alongside the 2016 presidential elections. Categories: Tags: 2016 US electionsdatasetselection tamperingfake storiesiranrussiaRussian Facebook adsSocial Engineeringtwitter |
The post Information operations on Twitter: new data released on election tampering appeared first on Malwarebytes Labs.
Read moreCredit to Author: Kayla Matthews| Date: Thu, 11 Oct 2018 15:00:00 +0000
 | |
| As we dive headfirst into National Cyber Security Awareness Month, it seems only fitting to discuss ways to stay on top of cybersecurity news. But what if following along makes you feel a little overwhelmed? Try these six methods of information-gathering to brush up on your cybersecurity know-how without losing your mind. Categories: Tags: cybersecuritycybersecurity awarenessnational cybersecurity awareness monthNCSAMsecurity professionalssocial mediatwitter |
The post 6 ways to keep up with cybersecurity without going crazy appeared first on Malwarebytes Labs.
Read more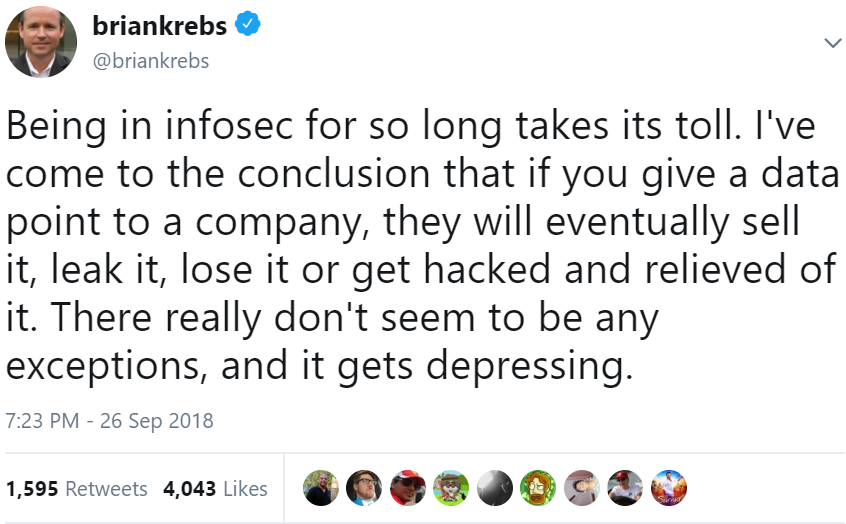
Credit to Author: BrianKrebs| Date: Tue, 02 Oct 2018 23:42:24 +0000
A ridiculous number of companies are exposing some or all of their proprietary and customer data by putting it in the cloud without any kind of authentication needed to read, alter or destroy it. When cybercriminals are the first to discover these missteps, usually the outcome is a demand for money in return for the stolen data. But when these screw-ups are unearthed by security professionals seeking to make a name for themselves, the resulting publicity often can leave the breached organization wishing they’d instead been quietly extorted by anonymous crooks.
Read more