Hijacking online accounts through voicemail
Credit to Author: Alex Drozhzhin| Date: Fri, 17 Aug 2018 15:50:43 +0000
When it comes to online accounts, voicemail is a major security hole. Here’s why.
Read moreCredit to Author: Alex Drozhzhin| Date: Fri, 17 Aug 2018 15:50:43 +0000
When it comes to online accounts, voicemail is a major security hole. Here’s why.
Read moreCredit to Author: Pieter Arntz| Date: Wed, 09 May 2018 16:30:32 +0000
 | |
| Cheap hosting deals offering free certificates have made the green padlock a less convincing sign of security. Here’s what to look for to ensure a website is safe to visit. Categories: Tags: cacertificatesextended validationgreen padlockHTTPSPayPalphishingSSLTLS |
The post HTTPS: why the green padlock is not enough appeared first on Malwarebytes Labs.
Read moreCredit to Author: Malwarebytes Labs| Date: Mon, 04 Dec 2017 18:30:33 +0000
 | |
| A compilation of notable security news and blog posts from Monday, November 27 to Sunday, December 3, including smart toys, another security breach, ransomware, and things to ponder when shopping for gifts this Christmas season. Categories: Tags: a week in securityconferencecryptocurrencyinsider threatsPayPalphishingprivacyransomwarerecaprevenge pornsmart toysTerror EKweekly blog roundupwhatsapp |
The post A week in security (November 27 – December 03) appeared first on Malwarebytes Labs.
Read moreCredit to Author: Christopher Boyd| Date: Fri, 01 Dec 2017 19:35:26 +0000
 | |
| We take a look at a batch of fake PayPal emails asking potential victims to visit a so-called resolution center to address unverified transactions. Categories: Tags: emailfakemailPayPalphishphishingscam |
The post PayPal phish asks to verify transactions—don’t do it appeared first on Malwarebytes Labs.
Read more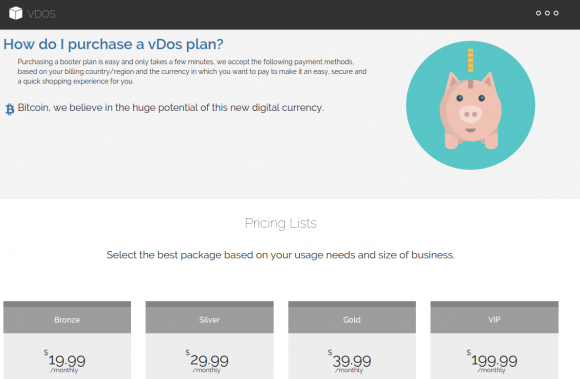
Credit to Author: BrianKrebs| Date: Tue, 06 Jun 2017 12:12:47 +0000
A new report proves the value of following the money in the fight against dodgy cybercrime services known as “booters” or “stressers” — virtual hired muscle that can be rented to knock nearly any website offline. Last fall, two 18-year-old Israeli men were arrested for allegedly running a vDOS, perhaps the most successful booter service of all time. The pair were detained within hours of being named in a story on this blog as the co-proprietors of the service (this site would later suffer a three-day outage as a result of an attack that was alleged to have been purchased in retribution for my reporting on vDOS). That initial vDOS story was based on data shared by an anonymous source who had hacked vDOS and obtained its private user and attack database. The story showed how the service made approximately $600,000 over just two of the four years it was in operation. Most of those profits came in the form of credit card payments via PayPal. But prior to vDOS’s takedown in September 2016, the service was already under siege thanks to work done by a group of academic researchers who teamed up with PayPal to identify and close accounts that vDOS and other booter services were using to process customer payments. The researchers found that their interventions cut profits in half for the popular booter service, and helped reduce the number of attacks coming out of it by at least 40 percent.
Read more
Credit to Author: BrianKrebs| Date: Fri, 21 Apr 2017 19:29:36 +0000
Last month Yours Truly got snookered by a too-good-to-be-true online scam in which some dirtball hijacked an Amazon merchant’s account and used it to pimp steeply discounted electronics that he never intended to sell. Amazon refunded my money, and the legitimate seller never did figure out how his account was hacked. But such attacks are becoming more prevalent of late as crooks increasingly turn to online crimeware services that make it a cakewalk to cash out stolen passwords.
Read more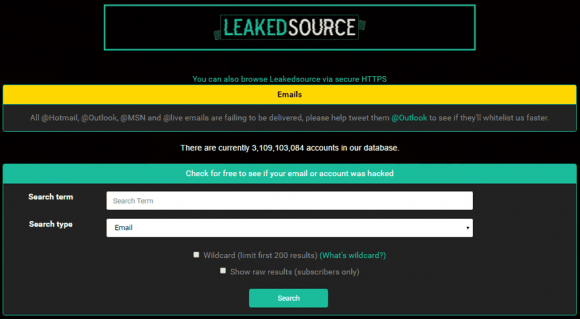
Credit to Author: BrianKrebs| Date: Wed, 15 Feb 2017 18:03:06 +0000
Late last month, multiple news outlets reported that unspecified law enforcement officials had seized the servers for Leakedsource.com, perhaps the largest online collection of usernames and passwords leaked or stolen in some of the worst data breaches — including billions of credentials for accounts at top sites like LinkedIn, Myspace, and Yahoo. In a development that may turn out to be deeply ironic, it seems that the real-life identity of Leakedsource’s principal owner may have been exposed by many of the same stolen databases he’s been peddling.
Read more