Govt. Cybersecurity Contractor Hit in W-2 Phishing Scam

Credit to Author: BrianKrebs| Date: Fri, 17 Mar 2017 22:02:02 +0000
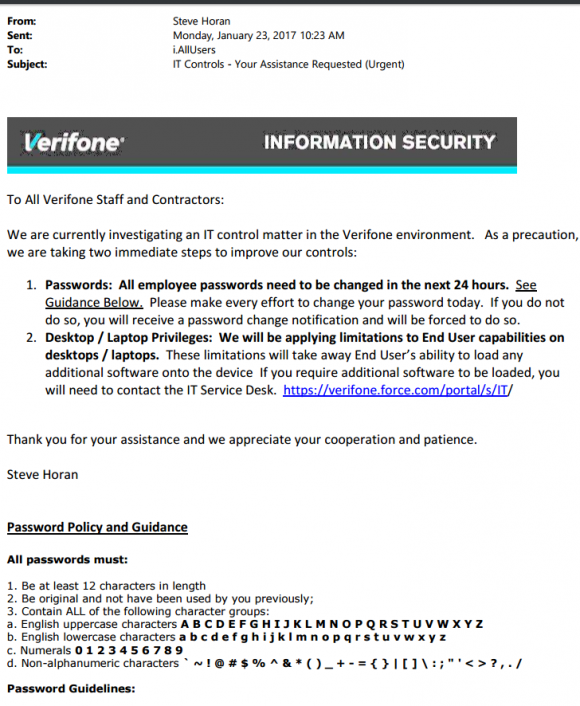
Just a friendly reminder that phishing scams which spoof the boss and request W-2 tax data on employees are intensifying as tax time nears. The latest victim shows that even cybersecurity experts can fall prey to these increasingly sophisticated attacks. On Thursday, March 16, the CEO of Defense Point Security, LLP — a Virginia company that bills itself as “the choice provider of cyber security services to the federal government” — told all employees that their W-2 tax data was handed directly to fraudsters after someone inside the company got caught in a phisher’s net.
Read More