U.K. Hospitals Hit in Widespread Ransomware Attack
Credit to Author: BrianKrebs| Date: Fri, 12 May 2017 16:54:01 +0000
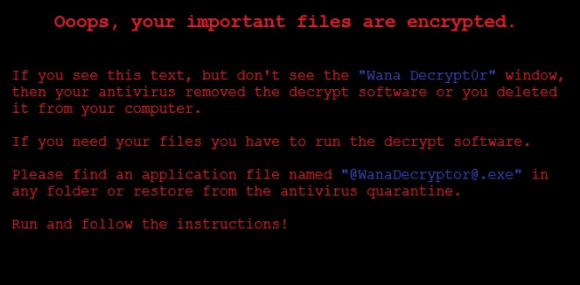
At least 16 hospitals in the United Kingdom are being forced to divert emergency patients today after computer systems there were infected with ransomware, a type of malicious software that encrypts a victim’s documents, images, music and other files unless the victim pays for a key to unlock them. It remains unclear exactly how this ransomware strain is being disseminated and why it appears to have spread so quickly, but there are indications the malware may be spreading to vulnerable systems through a security hole in Windows that was recently patched by Microsoft.
Read More