How and why you need HomeKit-secured smart homes
Credit to Author: Jonny Evans| Date: Thu, 27 Feb 2020 04:40:00 -0800
Once upon a time the Internet was amazing, enabling niche interests and connecting people. Apple’s iMac was the epitome of the era, while the iPhone became the prophet of change.
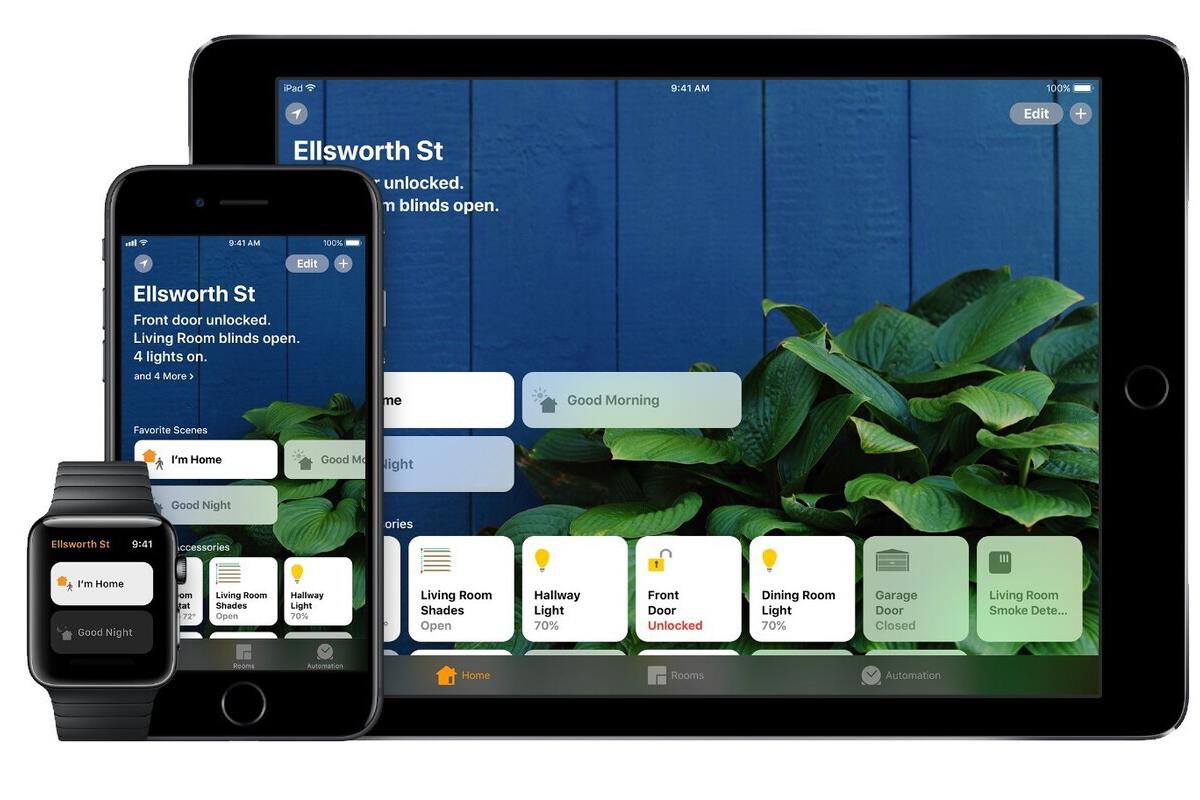
What is HomeKit-secured and why should you use it?
These days hackers break into home networks using our routers and smart home devices, which is why everyone must learn how to use HomeKit-secured routers to keep their connected homes safe.
Apple announced HomeKit-secured routers at WWDC 2019. The first few devices to support the tech recently began to reach market, including options from Linksys and (now) Amazon’s Eero routers.