Turning Off Wi-Fi and Bluetooth in iOS 11’s Control Center Doesn’t Actually Turn Off Wi-Fi or Bluetooth

Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 20 Sep 2017 17:07:50 +0000
And it’s a feature, not a bug.
Read more
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 20 Sep 2017 17:07:50 +0000
And it’s a feature, not a bug.
Read more
Credit to Author: Jörg Schindler| Date: Tue, 22 Aug 2017 08:35:42 +0000
Das aktuelle Apple Betriebssystem für Mobiltelefone, Tablets und smarte Uhren iOS 10 ist nun fast ein Jahr alt und wenn man die zeitliche Abfolge der bisherigen großen Updates zugrunde legt, wird das iOS 11 Update vermutlich bald zur Verfügung stehen. Grund genug, nicht nur Gadgets und überarbeitete Usability anzusehen, sondern insbesondere die Security und Privacy […]<img alt=”” border=”0″ src=”https://pixel.wp.com/b.gif?host=news.sophos.com&blog=834173&post=42276&subd=sophos&ref=&feed=1″ width=”1″ height=”1″ /><img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/5Hz4x7cS_S8″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Jonny Evans| Date: Wed, 13 Sep 2017 07:36:00 -0700
The iPhone X replaces the Home button and Touch ID with gesture controls and Face ID, sophisticated facial recognition software that learns to recognize your face and lets you use your device only after it has confirmed it is you. It is a new technology — here’s what we know about it so far:
This is how Apple’s chief marketer, Phil Schiller put it: “With the iPhone X, your iPhone is locked until you look at it and it recognizes you. Nothing has ever been more simple, natural, and effortless. This is the future of how we’ll unlock our smartphones and protect our sensitive information.”
To read this article in full or to leave a comment, please click here

Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Tue, 12 Sep 2017 13:00:00 +0000
Security researchers reveal several new bugs that allowed hackers to hack into cellphones and computers simply because they had Bluetooth on.
Read more
Credit to Author: Lucas Mearian| Date: Tue, 05 Sep 2017 21:04:00 -0700
Enterprise mobility management (EMM) software vendor MobileIron today announced its Apple release, aimed at the growing need for enterprises to provide IT managers with more robust management and security features for Macs.
While Windows and even Chrome-based laptops are already included in EMM consoles, macOS hardware has traditionally been treated as an outlier in the office, according to Nick McGuire, vice president of Enterprise Research at CCS Insight.
While MobileIron’s software suite already supported macOS for basic functions, including device configuration, millennials entering the workforce favor Apple’s line of laptops – driving the need for a unified endpoint management strategy that includes security and bulk licensing, according to Ojas Rege, MobileIron’s chief strategy officer.
To read this article in full or to leave a comment, please click here
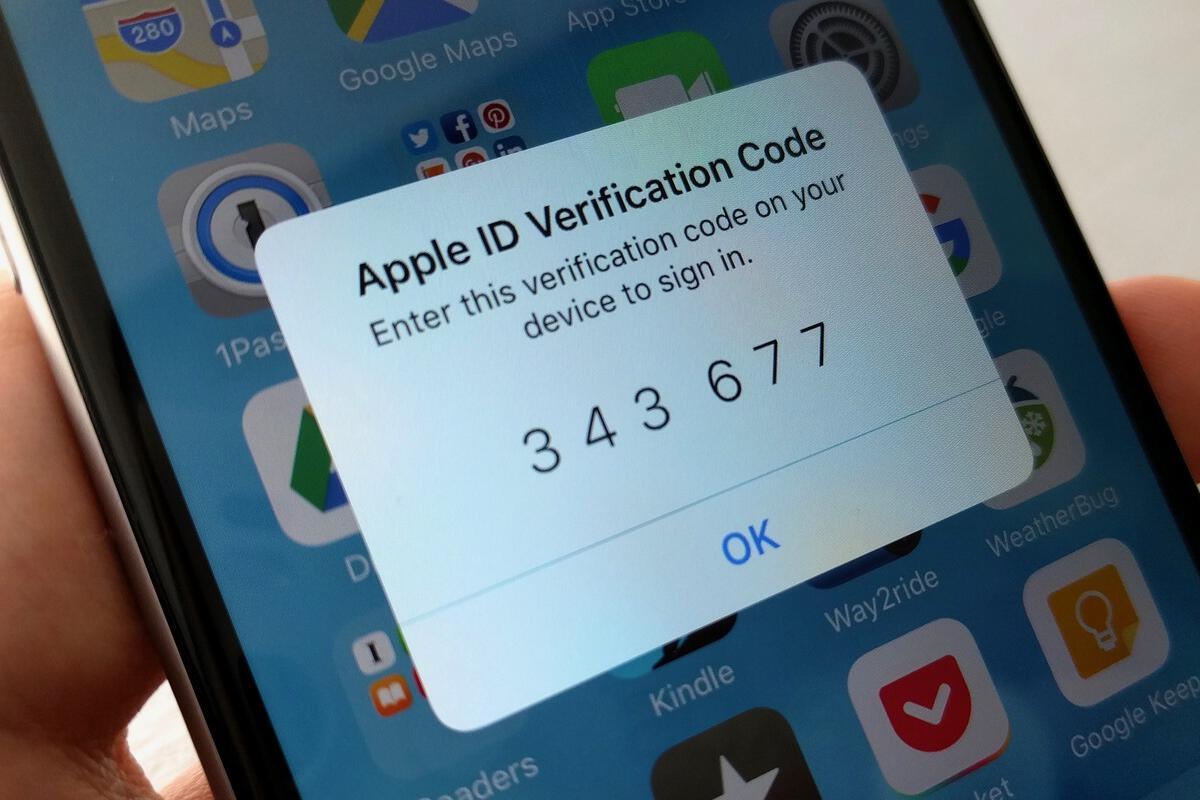
Credit to Author: Michael deAgonia| Date: Fri, 18 Aug 2017 03:11:00 -0700
Given that so many of the details of our digital lives are either with us (on our smartphones) or easily accessible (via the web), you should be doing everything you can to protect that information and data. On iPhones and iPads, data is largely kept in a vault, sealed behind strong encryption and (hopefully) a strong password. Even if the device is lost or stolen, chances are good that encryption will keep data safe. (That vault is secure enough to frustrate even the FBI.)
Although iOS devices are designed and built to be secure, data is also stored and accessible online. With security breaches occurring routinely, your data is vulnerable to anyone in the world with an internet connection and a halfway decent browser. If a breach occurs and thieves gain access to your email and password, they can easily reset any account linked to that email, change the password, and lock you out of your own data.
To read this article in full or to leave a comment, please click here

Apple's iOS has long had the reputation of being more secure than Android, but that may not necessarily be the case. Here's how to evaluate each side's claims about mobile security.

Get the details on Microsoft's new Azure Stack, why cyberattacks never seem to end, the fate of Apple's Touch ID and why QWERTY keyboards are now tech relics.