How dangerous are Threema vulnerabilities? | Kaspersky official blog

Credit to Author: Stan Kaminsky| Date: Fri, 13 Jan 2023 13:25:51 +0000
Brief analysis of vulnerabilities in Threema and practical tips for Threema users
Read more
Credit to Author: Stan Kaminsky| Date: Fri, 13 Jan 2023 13:25:51 +0000
Brief analysis of vulnerabilities in Threema and practical tips for Threema users
Read more
Credit to Author: Stan Kaminsky| Date: Mon, 09 Jan 2023 17:21:20 +0000
How quantum computers will affect encryption, and when you should start preparing yourself.
Read more
Just days after announcing the close of its consumer-oriented Wickr Me encrypted messaging service, Amazon Web Services (AWS), at its annual re:Invent conference on Monday, said that it was making the enterprise version of the app generally available.
Dubbed simply AWS Wickr, the service was first announced in July and has been in preview till now.
The enterprise version of the messaging service, designed to allow enterprise users to securely collaborate via text, voice and video, along with file and screen sharing, is expected to help enterprises meet auditing and regulatory requirements such as e-discovery and US Freedom of Information Act (FOIA) requests, the company said in a statement.
Credit to Author: Tejaswini Sandapolla| Date: Tue, 18 Oct 2022 06:45:52 +0000
 Emotet is usually delivered by SPAM campaigns containing document files. This self-propagating Trojan is a downloader malware that…
Emotet is usually delivered by SPAM campaigns containing document files. This self-propagating Trojan is a downloader malware that…
The post A DEEP DIVE INTO NEW 64 BIT EMOTET MODULES appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.
Read moreCategories: Explained Categories: News Tags: Steganography Tags: encryption Tags: least significant bits Tags: rgb Tags: masking Tags: palette-based Tags: lossy Tags: compression Tags: cropping Steganography is the prime example of hiding something in plain sight. We look at the basics, some methods, and the hurdles of hiding messages in images. |
The post Explained: Steganography appeared first on Malwarebytes Labs.
Read moreCredit to Author: Christopher Boyd| Date: Wed, 03 Aug 2022 08:01:00 +0000
We give you some tips as you gear up to return to school or college to ward off theft, and limit the impact should the worst happen.
The post How to protect yourself and your kids against device theft appeared first on Malwarebytes Labs.
Read moreCredit to Author: Mrigank Tyagi| Date: Fri, 29 Jul 2022 12:13:02 +0000
 PowerShell was originally intended as a task automation and configuration management program for system administrators. However, it…
PowerShell was originally intended as a task automation and configuration management program for system administrators. However, it…
The post PowerShell: An Attacker’s Paradise appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.
Read more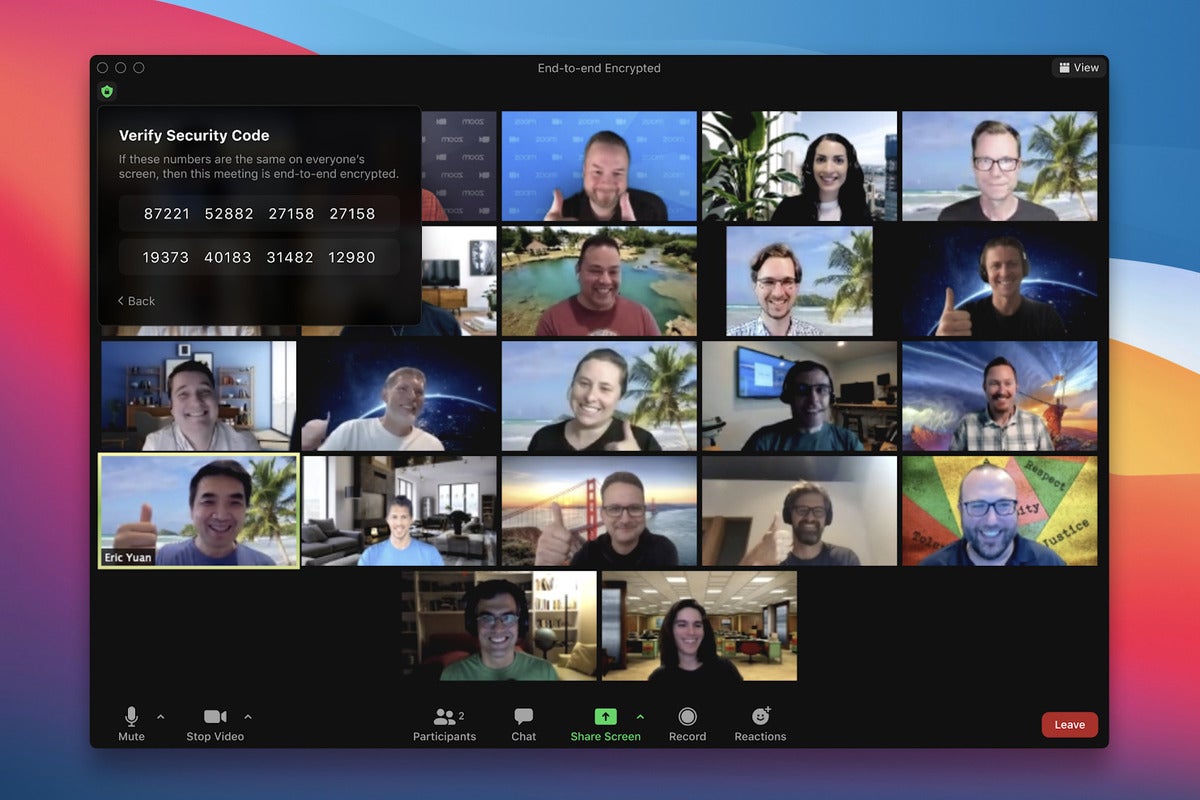
Credit to Author: Charlotte Trueman| Date: Fri, 22 Jul 2022 03:44:00 -0700
Zoom has announced it is expanding end-to-end encryption (E2EE) capabilities to Zoom Phone, with breakout rooms to be given the same level of encryption in the near future.
Zoom Phone customers now have the option to upgrade to E2EE during one-on-one Zoom Phone calls between users on the same Zoom account that occur via the Zoom client.
During a call, when users select “More” they will see an option to change the session to an end-to-end encrypted phone call. When enabled, Zoom encrypts the call by using cryptographic keys known only to the devices of the caller and receiver. Users will also have the option to verify E2EE status by providing a unique security code to one another.