The DeepSeek controversy: Authorities ask where does the data come from and how safe is it?
The sudden rise of DeepSeek has raised questions of data origin, data destination, and the security of the new AI model.
Read MoreRSS Reader for Computer Security Articles
The sudden rise of DeepSeek has raised questions of data origin, data destination, and the security of the new AI model.
Read More
Credit to Author: Andrew Brandt| Date: Tue, 09 Jul 2024 18:05:32 +0000
Microsoft fixes 138 bugs in Windows and other products this month
Read More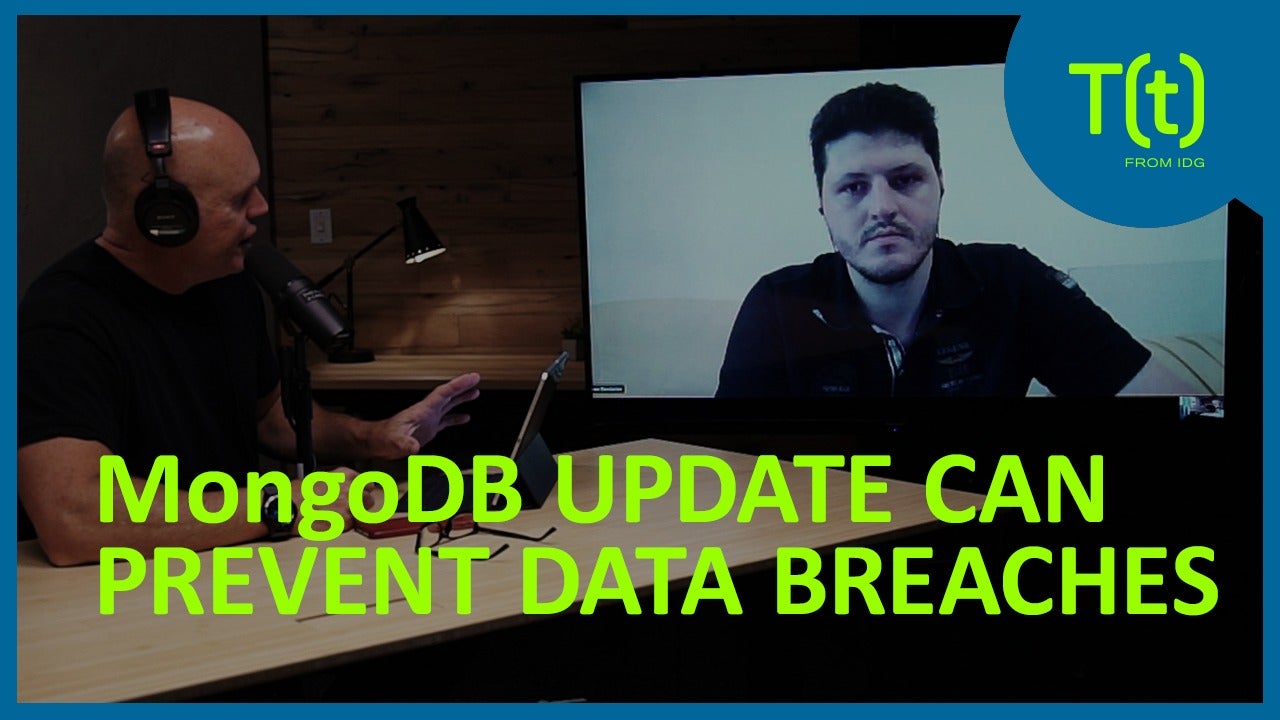
CSO senior writer Lucian Constantin and Computerworld Executive Editor Ken Mingis talk database security and how MongoDB's new field-level encryption takes security to the next level.
Credit to Author: Andrew Brandt| Date: Fri, 24 May 2019 12:00:29 +0000
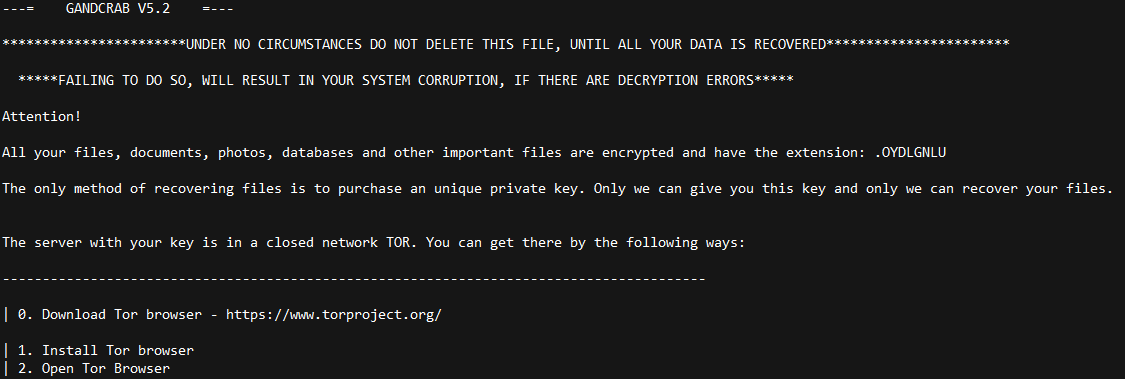
Someone is attacking internet-facing Windows database servers with GandCrab ransomware<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/Cjmfa68wtrI” height=”1″ width=”1″ alt=””/>
Read MoreCredit to Author: Christopher Boyd| Date: Wed, 01 May 2019 15:51:12 +0000
 | |
| A large database accessible online containing a huge amount of records has been found by researchers. The question is: who does it belong to, and what is it for? Categories: Tags: databaseexposedprivacyrecords |
The post Mysterious database exposed personal information of 80 million US households appeared first on Malwarebytes Labs.
Read MoreCredit to Author: Christopher Boyd| Date: Wed, 27 Mar 2019 16:00:00 +0000
 | |
| An app called Family Locator exposed the personal information and locations of 280,000 users in real time, including children. How did this happen? And how can app developers avoid it in the future? Categories: Tags: databaseexposedfamilylocationMongoDB |
The post Location data leaks from family tracking app database appeared first on Malwarebytes Labs.
Read MoreCredit to Author: Ghanshyam More| Date: Fri, 14 Dec 2018 11:58:50 +0000
On the back of an upswing in Ransomware activity, we decided to carry out an in-depth analysis of Ghost Ransomware. Interesting fact about this malware is that it uses multiple components to encrypt user files. Technical Analysis : Main malware executable (Ghost.exe) is compiled using the DotNet Framework. The infection…
Read MoreCredit to Author: Lily Hay Newman| Date: Wed, 29 Mar 2017 14:00:49 +0000

The root of so many high-profile data leaks are the insecure databases that underpin the internet. The post If You Want to Stop Big Data Breaches, Start With Databases appeared first on WIRED.
Read More