Second vulnerability in Spring Cloud casts shadow on popular Java framework

Credit to Author: gallagherseanm| Date: Thu, 31 Mar 2022 00:28:07 +0000
SophosLabs IPS signature available to detect and block issue under exploit
Read more
Credit to Author: gallagherseanm| Date: Thu, 31 Mar 2022 00:28:07 +0000
SophosLabs IPS signature available to detect and block issue under exploit
Read more
Credit to Author: stephenlawton| Date: Wed, 30 Mar 2022 15:16:53 +0000
Encryption, protected cloud servers vital to secure backups
Read more
Credit to Author: Scott Carey| Date: Thu, 03 Mar 2022 03:12:00 -0800
Splunk has named Gary Steele as its new CEO, three months after the surprise resignation of longtime CEO Doug Merritt.
“The board is focused on identifying a leader with a proven track record of scaling operations and growing multi-billion-dollar enterprises,” Merritt said in a statement at the time.
We now know that leader is Gary Steele, who was the founding CEO of software-as-a-service (SaaS) security vendor Proofpoint, a company he led for nearly 20 years. During that time, Steele navigated both an IPO in 2012 and a private equity buyout from Thoma Bravo last year. He will start on April 11, when he will also take a seat on Splunk’s board.

Credit to Author: Rich Beckett| Date: Mon, 31 Jan 2022 15:00:54 +0000
At Sophos, we’re committed to helping organizations secure essential resources and we’re proud to be recognized for the continued expansion of our cloud security portfolio. As a global leader in cloud security, we’ve been recognized by CRN®, a brand of The Channel Company, in its annual list of the Coolest Cloud Companies. This list honors […]
Read moreCredit to Author: Dan Macharia| Date: Thu, 12 Mar 2020 16:53:43 +0000
 | |
| Times are quickly changing and many teams are scrambling to embrace a shift to remote work. How will security protocols change? Time to move from on-prem to RemoteSec. Categories: Tags: cloud infrastructurecloud securitycloud servicesremote securityremote workremote workersremote workingremotesectelecommutingV2 Cloudworkforce |
The post RemoteSec: achieving on-prem security levels with cloud-based remote teams appeared first on Malwarebytes Labs.
Read moreCredit to Author: Trend Micro| Date: Tue, 10 Mar 2020 23:35:40 +0000

Containers provide a list of benefits to organizations that use them. They’re light, flexible, add consistency across the environment and operate in isolation. However, security concerns prevent some organizations from employing containers. This is despite containers having an extra layer of security built in – they don’t run directly on the host OS. To make…
The post Smart Check Validated for New Bottlerocket OS appeared first on .
Read moreCredit to Author: Chris Taylor| Date: Tue, 10 Mar 2020 17:27:10 +0000

On March 3, 2020, the cyber division of Federal Bureau of Investigation (FBI) issued a private industry notification calling out Business Email Compromise (BEC) scams through exploitation of cloud-based email services. Microsoft Office 365 and Google G Suite, the two largest cloud-based email services, are targeted by cyber criminals based on FBI complaint information since…
The post Trend Micro Cloud App Security Blocked 12.7 Million High-Risk Email Threats in 2019 – in addition to those detected by cloud email services’ built-in security appeared first on .
Read more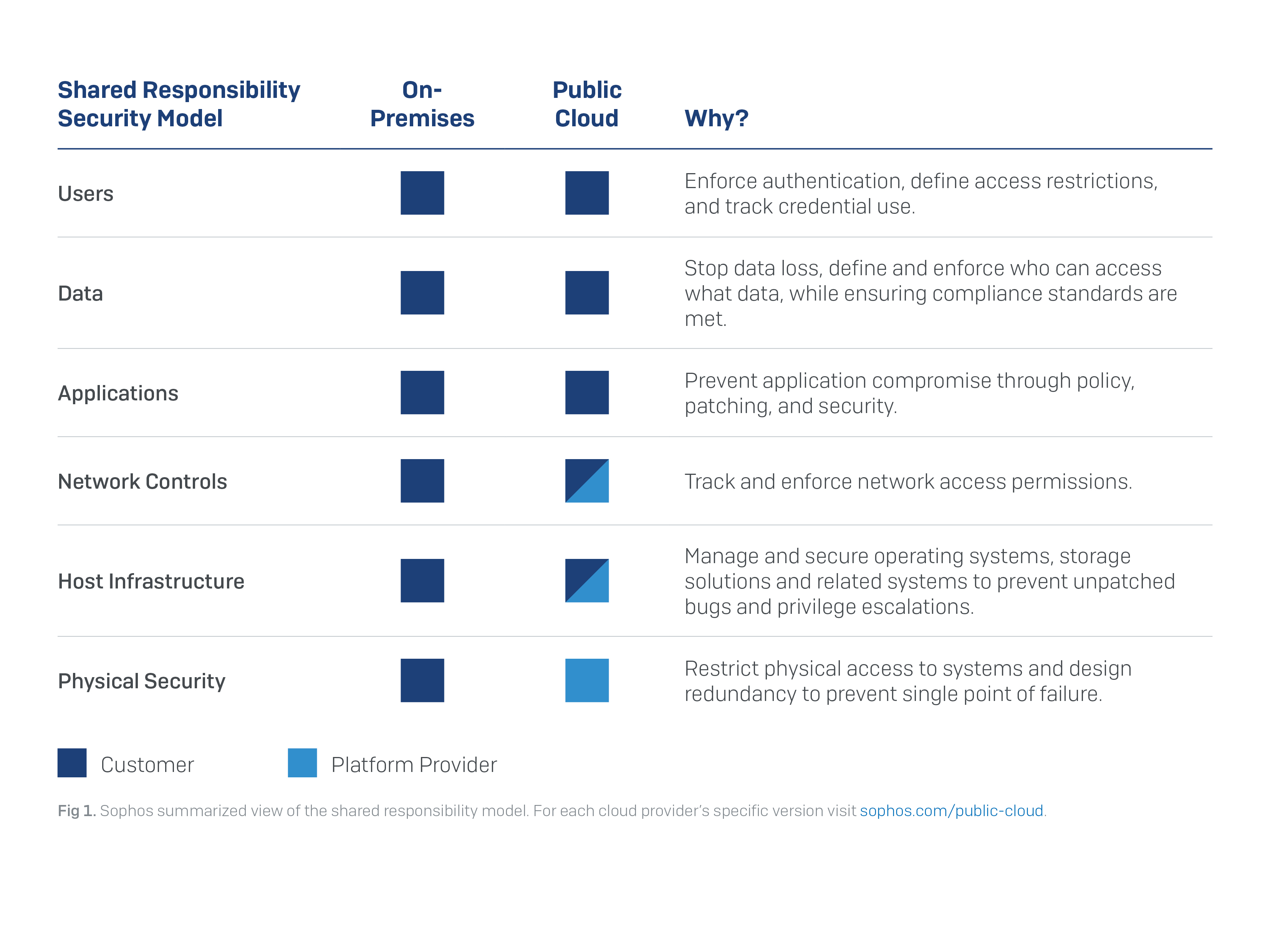
Credit to Author: Sally Adam| Date: Fri, 21 Feb 2020 11:59:35 +0000
The recent MGM Resort hotels cloud server data breach highlights the need to secure sensitive data held in the public cloud.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/ifst-NkTXmQ” height=”1″ width=”1″ alt=””/>
Read more