VirusBulletin
VB2019 paper: Attribution is in the object: using RTF object dimensions to track APT phishing weaponizers
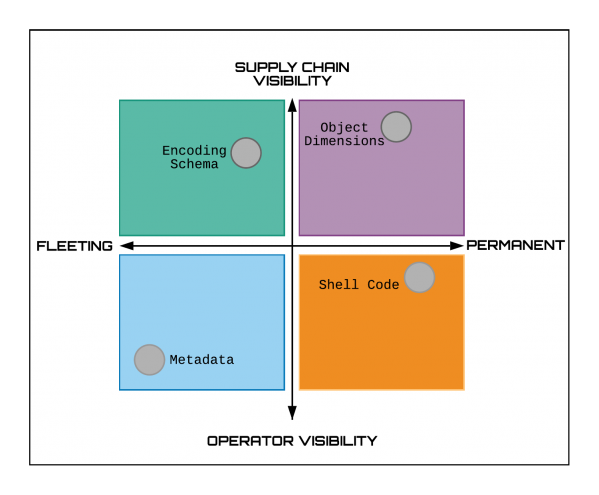
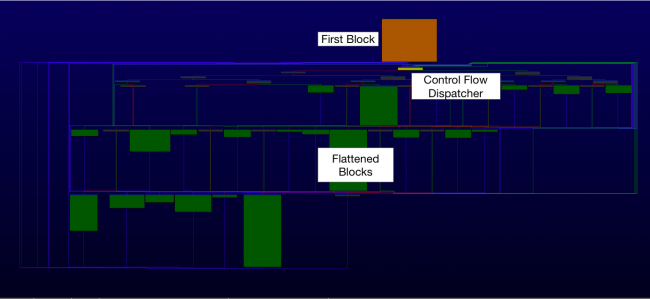
At VB2019 in London Michael Raggi (Proofpoint) and Ghareeb Saad (Anomali) presented a paper on the ‘Royal Road’ exploit builder (or weaponizer) and how the properties of RTF files can be used to track weaponizers and their users. Today we publish both their paper and the recording of their presentation.