Enough attribution to count
Credit to Author: Chester Wisniewski| Date: Tue, 08 Aug 2023 10:01:37 +0000
Naming and shaming the bad guys can be gratifying, but for practical protection, Threat Activity Clusters are the way
Read more
Credit to Author: Chester Wisniewski| Date: Tue, 08 Aug 2023 10:01:37 +0000
Naming and shaming the bad guys can be gratifying, but for practical protection, Threat Activity Clusters are the way
Read more
Credit to Author: Andrew Brandt| Date: Tue, 08 Aug 2023 10:00:11 +0000
A collection of very specific behaviors, observed by Sophos X-Ops incident response analysts in the lead-up to four separate ransomware attacks in the first quarter of 2023, indicates an unexpected connection between the attacks. In the parlance of the Managed Detection and Response (MDR) team, the peculiarly similar details constitute a threat activity cluster that […]
Read moreCredit to Author: gallagherseanm| Date: Mon, 07 Aug 2023 11:00:45 +0000
AI Village talk highlights how generative can be used to automate the creation of fraud campaigns, generating hundreds of fraudulent sites.
Read more
Credit to Author: Jagadeesh Chandraiah| Date: Wed, 02 Aug 2023 10:00:40 +0000
CryptoRom” fake crypto-trading mobile apps pushed through AI-assisted romance scam, using ChatGPT to lure targets.
Read more
Credit to Author: Doug Aamoth| Date: Tue, 01 Aug 2023 13:00:17 +0000
New insights into how ransomware impacts this sector, including the frequency, root causes of attacks, and data recovery costs.
Read more
Credit to Author: gallagherseanm| Date: Mon, 31 Jul 2023 10:00:38 +0000
The new SEC cybersecurity rules significantly enhance disclosure requirements, emphasize the board’s role in risk management, and introduce a stringent four-day reporting timeline, necessitating that public companies bolster their cybersecurity strategies, improve incident response processes, and ensure robust communication plans are in place.
Read more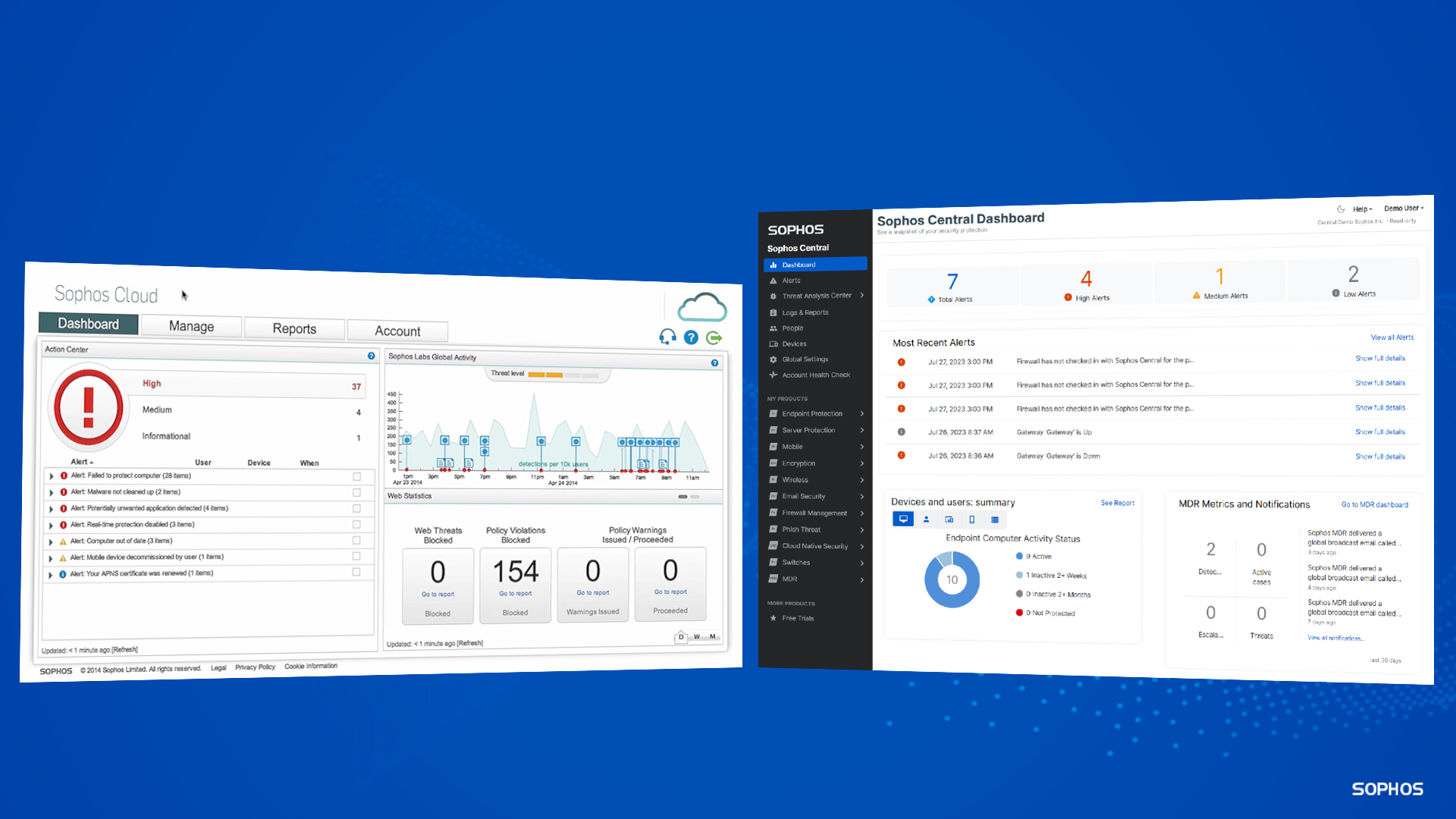
Credit to Author: Sally Adam| Date: Sat, 29 Jul 2023 07:25:32 +0000
The world’s most trusted cybersecurity platform now secures more than 25 million devices
Read more
Credit to Author: Pankaj Kohli| Date: Thu, 27 Jul 2023 10:00:44 +0000
Sophos X-Ops researchers discover a cluster of credential-harvesting apps targeting Iranian bank customers
Read more