UK fines TikTok $15.8 million for GDPR violation of children's privacy

Chinese-owned social media sensation TikTok has been fined almost $16 million for violating provisions of the UK’s General Data Protection Regulation.

Chinese-owned social media sensation TikTok has been fined almost $16 million for violating provisions of the UK’s General Data Protection Regulation.
It feels as if practically everyone has been using Open AI’s ChatGPT since the generative AI hit prime time. But many enterprise professionals may be embracing the technology without considering the risk of these large language models (LLMs).
That’s why we need an Apple approach to Generative AI.
ChatGPT seems to be a do-everything tool, capable of answering questions, finessing prose, generating suggestions, creating reports, and more. Developers have used the tool to help them write or improve their code and some companies (such as Microsoft) are weaving this machine intelligence into existing products, web browsers, and applications.
![]()
The UK's Information Commission’s Office reminds organizations that data protection laws still apply to unfiltered data used to train large language models.

The Chinese government is instituting a cybersecurity review of US-based memory chip maker Micron’s products being sold in the country, in the latest move in the ongoing semiconductor trade dispute that pits China against the US and its allies.
The rupture between China and the West over semiconductors is causing chip supply chain disruptions that threaten many of the fastest-growing parts of the technology sector – mainly AI and cloud technology. The chip war is also putting global enterprises in the crosshairs, as auto manufacturing and a host of other sectors are increasingly dependent on the availability of advanced silicon for growth.
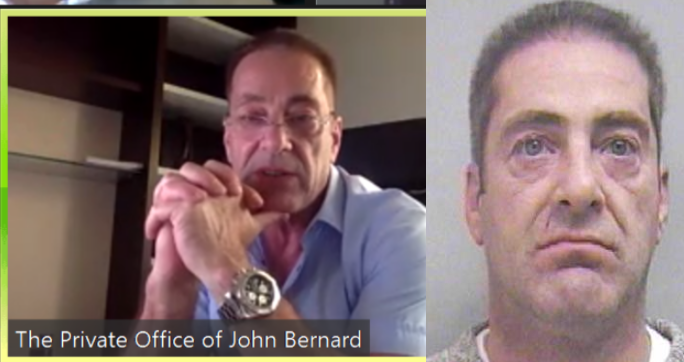
Credit to Author: BrianKrebs| Date: Mon, 03 Apr 2023 16:13:42 +0000
John Clifton Davies, a 60-year-old con man from the United Kingdom who fled the country in 2015 before being sentenced to 12 years in prison for fraud, has enjoyed a successful life abroad swindling technology startups by pretending to be a billionaire investor. Davies’ newest invention appears to be “CodesToYou,” which purports to be a “full cycle software development company” based in the U.K.
Read more
Ransomware.
It’s one word that can strike a chill in anyone from a corporate C-suite to a home user. It’s sometimes hard to get a feel for the overall ransomware industry (and yes, it’s now an industry). But based on anecdotal reviews of forums and social media, it appears as though attacks against individuals are slowing. I no longer see people report they’ve been hit by ransomware on their PCs.
But it may be that attackers have realized that going after “one-off” targets isn’t the best business plan. In fact, in a recent Microsoft Secure online seminar (registration required), Jessica Payne and Geoff McDonald discuss how ransomware is now a big business, offered as a service by those who sell access to compromised networks to others.
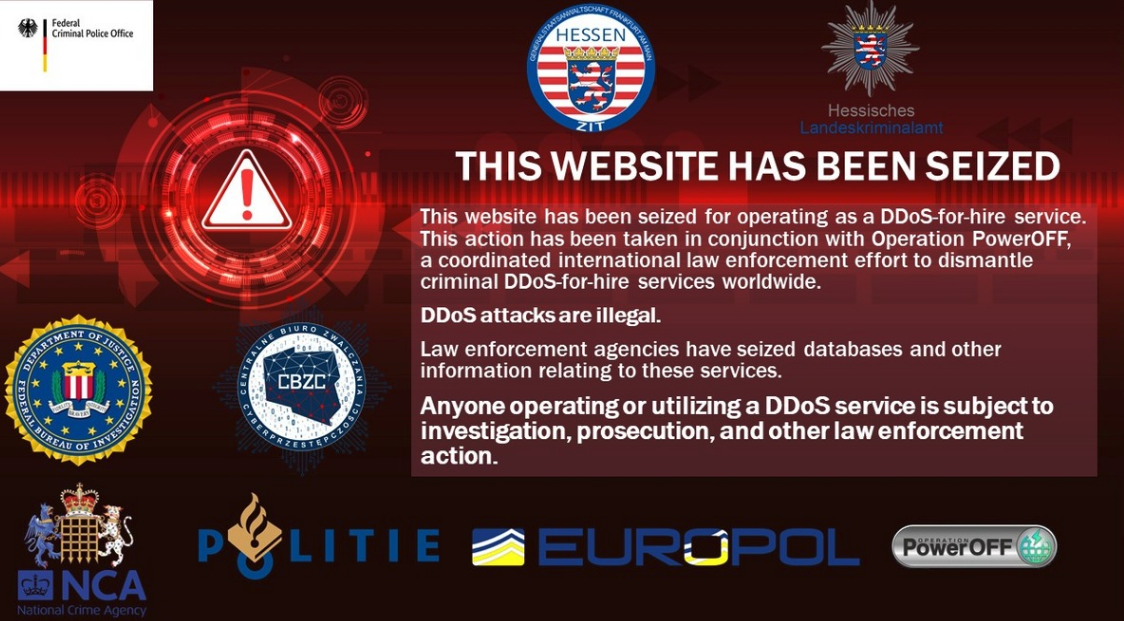
Credit to Author: BrianKrebs| Date: Fri, 31 Mar 2023 18:35:15 +0000
Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web service that catered to cybercriminals operating DDoS-for-hire services. Fly Hosting first advertised on cybercrime forums in November 2022, saying it was a Germany-based hosting firm that was open for business to anyone looking for a reliable place to host malware, botnet controllers, or DDoS-for-hire infrastructure.
Read more
Apple’s decision to support MAC Address Randomization across its platforms may provide some degree of protection against a newly-identified Wi-Fi flaw researchers say could let attackers hijack network traffic. iOS, Linux, and Android devices may be vulnerable.
The researchers have identified a fundamental flaw in the design of the IEEE 802.11 Wi-Fi standard attackers could exploit to trick access points (Wi-Fi base stations) into leaking information. The researchers do not claim the vulnerability is being actively exploited, but warn that it might enable the interception of network traffic.