Microsoft patches bug that could have allowed an attacker to revert your computer back to an older, vulnerable version
Microsoft has released a patch for a bug for a “downgrade attack” that was recently revealed by researchers at security conferences Black Hat and Def Con.
What does that mean in layman terms?
You: Let me check whether my system is fully updated
Windows: Sure, all’s well
Attacker: *Chuckles and deploys an attack against a vulnerability for which you could have been patched long ago*
With a downgrade attack, the victim may have done all they can to keep their computer and software up to date, but an attacker can force it to revert to an older, vulnerable version and then use a known bug to infect your device.
With this particular attack, the researcher built a tool called “Windows Downdate” that takes over Windows Updates to turn a completely patched Windows system into a system which is exploitable by thousands of vulnerabilities from the past.
Microsoft has now patched the two vulnerabilities in Windows (CVE-2024-38202 and CVE-2024-21302) that the researcher used to create Windows Downdate. To manually check whether you have received this update:
- Click Settings in the Start menu
- Click Windows Update
- Select Update History
You should see this entry (KB5041585 successfully installed) for Windows 11:
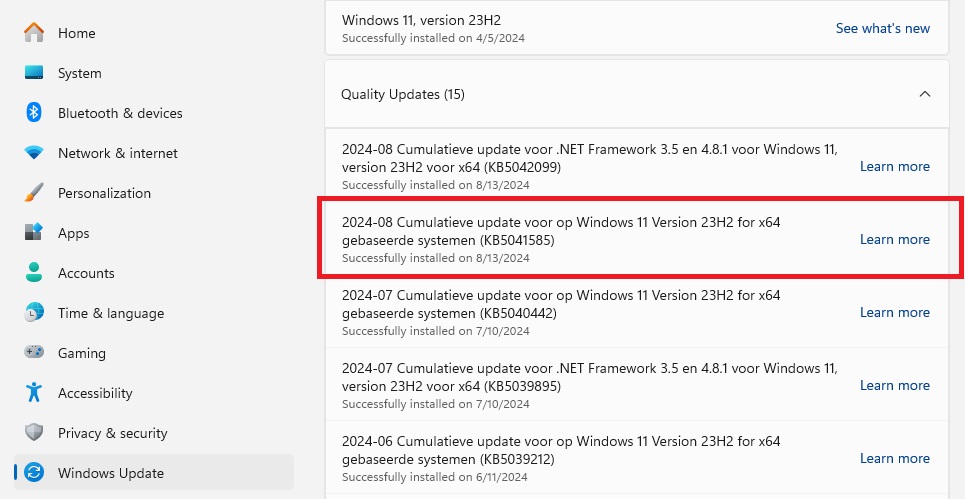
If you don’t see this, you can start the update by clicking the Check for updates button from the Windows Update menu, or download the relevant update from the Microsoft Update Catalog.
For Windows 10 systems the method is the same, but the KB number is KB5041580 and the update catalog can be found by following this link.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
https://blog.malwarebytes.com/feed/