June Patch Tuesday squares up with 49 patches
Credit to Author: Angela Gunn| Date: Wed, 12 Jun 2024 01:21:01 +0000
June’s Patch Tuesday set eases Windows admins gently into summer, as Microsoft on Tuesday released 49 patches touching 7 product families. Windows as usual takes the lion’s share of patches with 34. The rest relate to Azure, 365 Apps for Enterprise, Dynamics 365, Office, Visual Studio, and SharePoint.
At patch time, none of the issues addressed are known to be under exploit in the wild. That said, eleven vulnerabilities in Windows are by the company’s estimation more likely to be exploited in the next 30 days; one of those is the month’s sole critical-severity issue, which we’ll discuss at some length below. Six of this month’s issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on seven patches related to the Edge browser, one related to GitHub, one fascinating item from MITRE that affects not just Windows but much of the internet, and two from Adobe. We don’t include advisories in the CVE counts and graphics below, but we provide information on all of them in an appendix at the end of the article, and we will dig into the MITRE advisory below. We are as usual including at the end of this post three other appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total Microsoft CVEs: 49
- Total Edge / Chrome advisory issues covered in update: 7
- Total non-Edge Microsoft advisory issues covered in update: 2
- Total Adobe issues covered in update: 2
- Publicly disclosed: 0*
- Exploited: 0
- Severity
- Critical: 1
- Important: 48
- Impact:
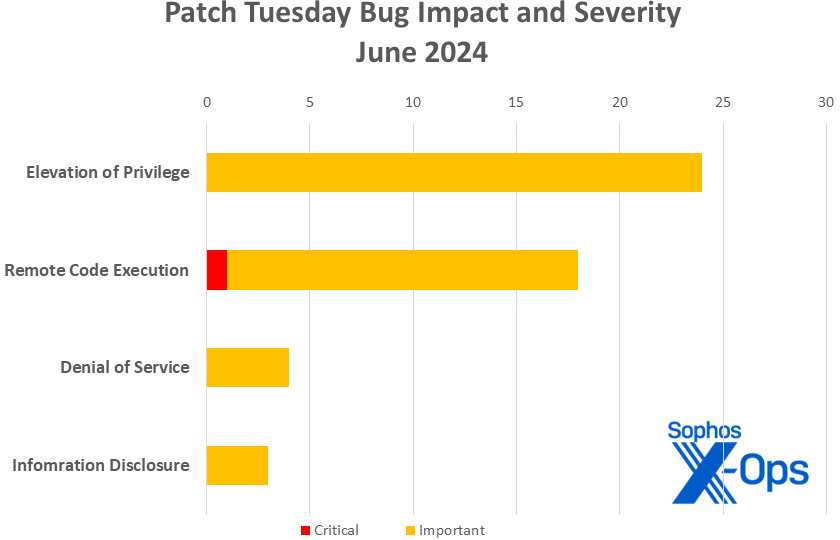
- Elevation of Privilege: 24
- Remote Code Execution: 18
- Denial of Service: 4
- Information Disclosure: 3
* One advisory-only CVE is publicly disclosed; see below
Figure 1: Just four categories of vulnerability are represented in June’s Patch Tuesday batch
Products
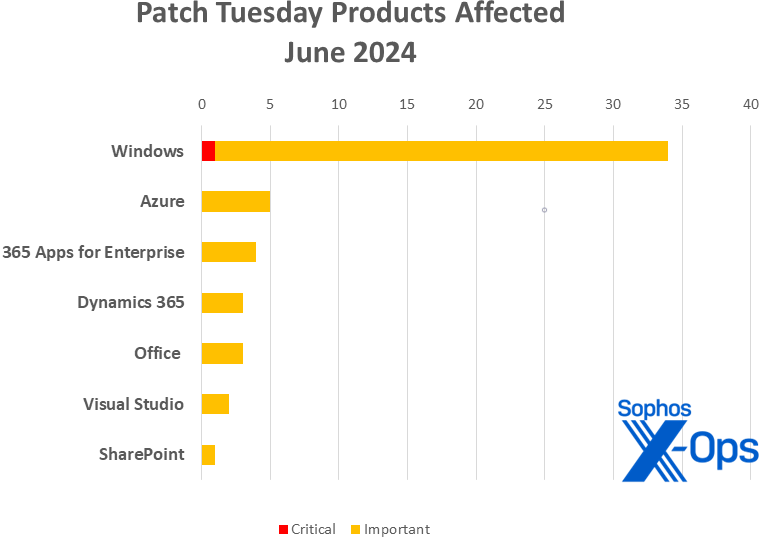
- Windows: 34
- Azure: 5
- 365 Apps for Enterprise: 4 (including one shared with Office)
- Dynamics 365: 3
- Office: 3 (shared with 365 Apps for Enterprise)
- Visual Studio: 2
- SharePoint: 1
Figure 2: Windows accounts for two-thirds of June’s patches, as well as the sole Critical-level issue
Notable June updates
In addition to the issues discussed above, a few specific items merit attention.
CVE-2024-30080 – Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
Microsoft has marked 11 CVEs this month as more likely to be exploited within 30 days of Patch Tuesday; this critical-severity RCE – the month’s only critical-class issue — should be considered top of the class. It affects both clients and servers that have enabled the Windows message-queuing service. With that switched on and listening (default port is 1801), an attacker could send a maliciously crafted MSMQ packet to the server and gain RCE. (Yes, Sophos has a detection for this; please see the table immediately below Figure 3.)
CVE-2023-50868 – MITRE: CVE-2023-50868 NSEC3 closest encloser proof can exhaust CPU
This is an advisory-only CVE, issued by MITRE and of concern to the industry at large, not only Microsoft. It covers a publicly disclosed issue with DNSSEC and how it proves the non-existence of a specified zone. (Unfamiliar with the details of DNSSEC, or perplexed as to how an NSEC record can prove a negative? The DNS Institute has a delightfully readable story that explains it.) The bug in question is an important-severity denial-of-service issue; it’s not thought to be under exploit in the wild, but it’s DNS and therefore worth your time.
CVE-2024-37325 – Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability
There is only one vulnerability this month that Microsoft considers critical in severity (CVE-2024-30800, above), but for those who go by CVSS scores, this Azure EoP merits a look – but only if you’re running a version of Linux/Ubuntu Data Science Virtual Machines (DSVM) prior to 24.05.24. If that’s your situation, this 9.8 CVSS bug requires neither privileges nor user interaction; all the attacker need do is send a specially crafted request to the target machine to gain access to authorized users’ credentials. Affected users should read up on the details and get moving.
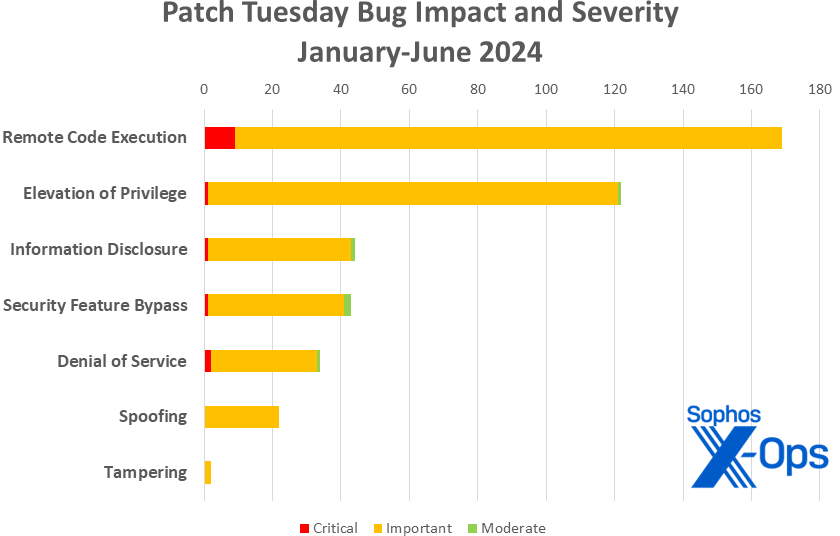
Figure 3: As we round the curve on calendar year 2024, Information Disclosure vulns pull slightly ahead of Security Feature Bypass issues, but RCE continues to lead the pack
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of June patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (24 CVEs)
| Important severity | |
| CVE-2024-29060 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-30064 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30066 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-30067 | WinLogon Elevation of Privilege Vulnerability |
| CVE-2024-30068 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30076 | Windows Container Manager Service Elevation of Privilege Vulnerability |
| CVE-2024-30082 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30090 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30093 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-30099 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-35248 | Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-35253 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-35254 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-35255 | Azure Identity Libraries and Microsoft Authentication Library Elevation of Privilege Vulnerability |
| CVE-2024-35265 | Windows Perception Service Elevation of Privilege Vulnerability |
| CVE-2024-37325 | Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability |
Remote Code Execution (18 CVEs)
| Critical severity | |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-30052 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-30062 | Windows Standards-Based Storage Management Service Remote Code Execution Vulnerability |
| CVE-2024-30063 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-30072 | Microsoft Event Trace Log File Parsing Remote Code Execution Vulnerability |
| CVE-2024-30074 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30075 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30077 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-30078 | Windows WiFi Driver Remote Code Execution Vulnerability |
| CVE-2024-30094 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30095 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30097 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-30100 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2024-30101 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30102 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30103 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-30104 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-35249 | Microsoft Dynamics Business Central Remote Code Execution Vulnerability |
Denial of Service (4 CVEs)
| Important severity | |
| CVE-2024-30065 | Windows Themes Denial of Service Vulnerability |
| CVE-2024-30070 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30083 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-35252 | Azure Storage Movement Client Library Denial of Service Vulnerability |
Information Disclosure (3 CVEs)
| Important severity | |
| CVE-2024-30069 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30096 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-35263 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
Appendix B: Exploitability
This is a list of the June CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE. This month does not address any vulnerabilities already under exploit.
| Exploitation more likely within the next 30 days | |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-30082 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30099 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
Appendix C: Products Affected
This is a list of June’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (34 CVEs)
| Critical severity | |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-30062 | Windows Standards-Based Storage Management Service Remote Code Execution Vulnerability |
| CVE-2024-30063 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-30064 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30065 | Windows Themes Denial of Service Vulnerability |
| CVE-2024-30066 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-30067 | WinLogon Elevation of Privilege Vulnerability |
| CVE-2024-30068 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30069 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30070 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30072 | Microsoft Event Trace Log File Parsing Remote Code Execution Vulnerability |
| CVE-2024-30074 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30075 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30076 | Windows Container Manager Service Elevation of Privilege Vulnerability |
| CVE-2024-30077 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-30078 | Windows WiFi Driver Remote Code Execution Vulnerability |
| CVE-2024-30082 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30083 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30090 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30093 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-30094 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30095 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30096 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-30097 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-30099 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-35265 | Windows Perception Service Elevation of Privilege Vulnerability |
Azure (5 CVEs)
| Important severity | |
| CVE-2024-35252 | Azure Storage Movement Client Library Denial of Service Vulnerability |
| CVE-2024-35253 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-35254 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-35255 | Azure Identity Libraries and Microsoft Authentication Library Elevation of Privilege Vulnerability |
| CVE-2024-37325 | Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability |
365 Apps for Enterprise (4 CVEs)
| Important severity | |
| CVE-2024-30101 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30102 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30103 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-30104 | Microsoft Office Remote Code Execution Vulnerability |
Dynamics 365 (3 CVEs)
| Important severity | |
| CVE-2024-35248 | Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability |
| CVE-2024-35249 | Microsoft Dynamics Business Central Remote Code Execution Vulnerability |
| CVE-2024-35263 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
Office (3 CVE)
| Important severity | |
| CVE-2024-30101 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30103 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-30104 | Microsoft Office Remote Code Execution Vulnerability |
Visual Studio (2 CVE)
| Important severity | |
| CVE-2024-29060 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-30052 | Visual Studio Remote Code Execution Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2024-30100 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the June Microsoft release, sorted by product.
Relevant to Edge / Chromium (7 CVEs)
| CVE-2024-5493 | Chromium: CVE-2024-5493 Heap buffer overflow in WebRTC |
| CVE-2024-5494 | Chromium: CVE-2024-5494 Use after free in Dawn |
| CVE-2024-5495 | Chromium: CVE-2024-5495 Use after free in Dawn |
| CVE-2024-5496 | Chromium: CVE-2024-5496 Use after free in Media Session |
| CVE-2024-5497 | Chromium: CVE-2024-5497 Out of bounds memory access in Keyboard Inputs |
| CVE-2024-5498 | Chromium: CVE-2024-5498 Use after free in Presentation API |
| CVE-2024-5499 | Chromium: CVE-2024-5499 Out of bounds write in Streams API |
Relevant to GitHub (1 CVE)
| CVE-2024-29187 | GitHub: CVE-2024-29187 WiX Burn-based bundles are vulnerable to binary hijack when run as SYSTEM |
Relevant to Visual Studio (non-Microsoft CVE issuer) (1 CVE)
| CVE-2023-50868 | MITRE: CVE-2023-50868 NSEC3 closest encloser proof can exhaust CPU |
Relevant to Adobe (non-Microsoft release) (2 CVEs)
| APSB24-41 | CVE-2024-34112 | Improper Access Control (CWE-284) |
| APSB24-41 | CVE-2024-34113 | Weak Cryptography for Passwords (CWE-261) |