Are browser-stored passwords secure? | Kaspersky official blog
Credit to Author: Natalya Zakuskina| Date: Tue, 15 Aug 2023 07:00:03 +0000
Browser-stored passwords save you from having to re-enter them each time, which is a real time-saver. But how safe is it? This post explores three reasons you shouldn’t store passwords in your browser, and why you should use a much more secure storage method: a password manager.
1. Password stealers
The core problem with storing passwords in browsers is that they sacrifice security for usability. This holds true for at least the three most popular browsers: Google Chrome, Mozilla Firefox, and Microsoft Edge, all of which store user passwords in a highly insecure way.
The reason is that all browsers store passwords in a very predictable place, in a folder whose path is no secret to anyone. And although the passwords themselves are encrypted, the encryption key is stored close by and readily accessible. Armed with this key, an attacker can decrypt and steal passwords. A farcical situation: the door appears to be securely locked, but the key is under the doormat, and the whole world knows it.
In fact, browsers use this state of affairs to compete with each other: to make it easier for users to switch, they often offer to import all saved data from the old browser, including stored passwords.
Any guesses who else is using this feature? That’s right. There is an entire class of malware (appropriately called password stealers) dedicated to credential theft. This malware sifts through folders known to contain browser-stored passwords, finds the key under the doormat, then decrypts the passwords and uploads the loot to the cybercriminals’ server. Later, these passwords are usually databased and sold in bulk on the dark web to other crooks who use them to hijack accounts (narrow specialization has long been the norm in the cybercriminal world).
To understand how easy it is to steal passwords stored in a browser, we recommend watching a demo video that clearly shows how to quickly extract passwords from Chrome, Firefox, and Edge using nothing more than a Python script.
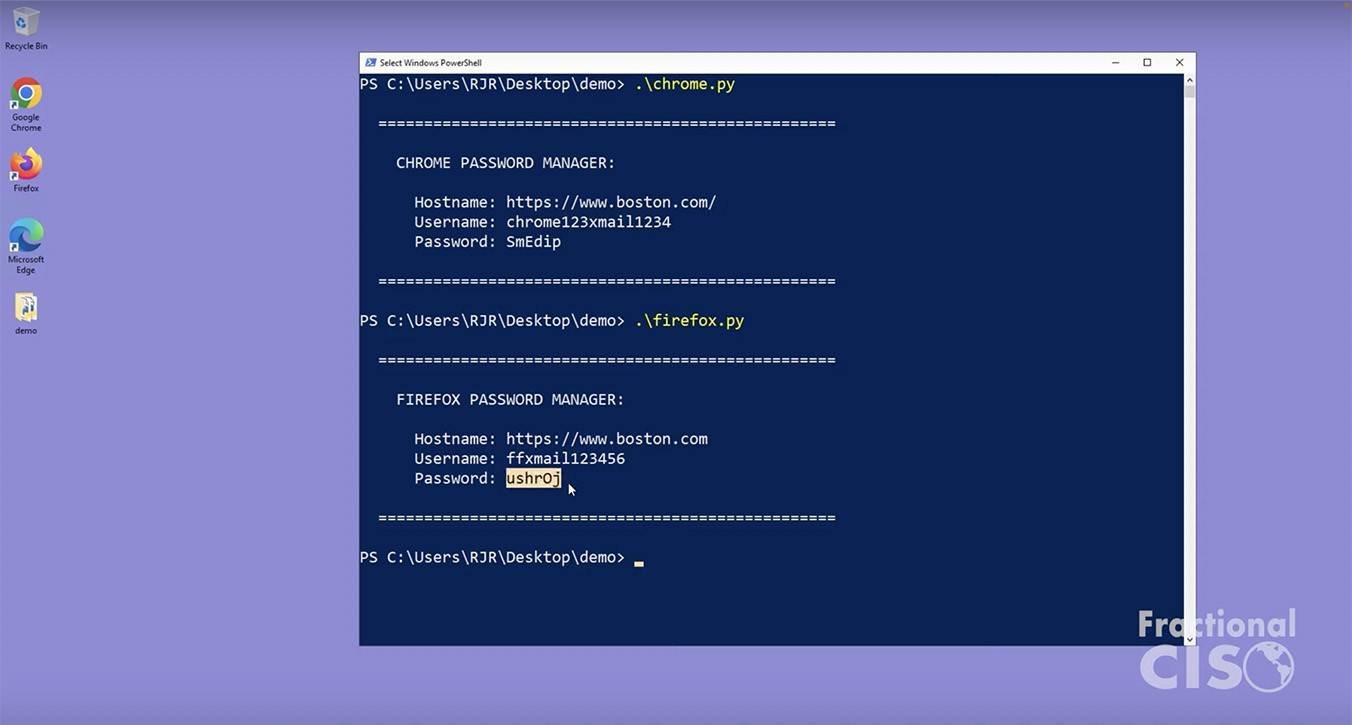
Demonstration of how to extract passwords stored in Google Chrome, Mozilla Firefox, and Microsoft Edge. (Source)
2. Physical access to the computer
It’s not just specially trained malware that can get up to this sort of mischief, but anyone with physical access to your computer. And no sophisticated hacking skills are required – scripts for exfiltrating browser-stored passwords are readily available online. All that is required is to run them.
Even an overly curious relative or work colleague could do this if you leave your computer unlocked. Or a hacker visiting your office on a scouting mission. Basically, anyone. The important point is that all your passwords stored in the browser will end up in potentially hostile hands.
And even if the intruder doesn’t have the right script to extract passwords from the browser-saved file, they can scour the settings for the list of sites for which passwords are stored, and then log in to one of them to read your correspondence, for example, or find out other secrets about you.
The world’s most popular browser (Google Chrome, in case you didn’t know) doesn’t even have a basic mechanism to prevent such actions. And while the Firefox developers were good enough to let users protect saved passwords with a primary password, they left this option disabled by default. The primary password must be explicitly enabled and configured, and it is unlikely that many Firefox users even know about it.
3. Browser account hijacking
The following problem is common to all browsers that allow users, for their convenience, to create an account to synchronize browsers on different devices. This means that bookmarks, browser sessions, extensions, settings, as well as saved passwords are all synchronized and stored in the cloud. And if a hacker gets inside your browser account, all they have to do is log in on another computer using the same account. Then all your accounts whose passwords are stored in the browser – from social networks to online banks – are there for the taking.
Why a password manager beats a browser
Like browsers, Kaspersky Password Manager remembers your credentials and lets you auto-populate them when logging in to websites. But unlike browser developers, we don’t compromise on security. In our password manager, the primary password is used by default and cannot be disabled – all your saved passwords are protected at all times. So even if someone gains physical access to your computer, they will not be able to simply log in to sites using the credentials stored in the manager. To do that, they would need the primary password, which no one but you knows (unless you stuck it to your screen on a sticky note).
Another advantage of Kaspersky Password Manager is, of course, that all passwords are stored only in encrypted form. And, crucially, we don’t keep the decryption key “under a doormat”. The encryption key is generated on the fly using the AES-256 algorithm on the basis of the primary password, which allows us not to store it at all. Anywhere. Ever. So even if a stealer manages to get onto your computer, it won’t be able to steal anything – all your passwords are securely encrypted. Incidentally, if you use Kaspersky Password Manager as part of Kaspersky Premium, we won’t even let the malware in.
One last thing. Naturally, we use the cloud to synchronize passwords between devices – all your passwords are linked to your My Kaspersky account. But even if an intruder were to somehow gain access to this account, your passwords stored in Kaspersky Password Manager would still be perfectly safe. That’s because in the cloud they are stored exclusively in encrypted form, and the decryption key is generated on the basis of the primary password, which only you know and without which attackers are toothless.
We’ve also recently updated Kaspersky Password Manager to support the Opera and Opera GX browsers, which continue to win over new users. That means we now support all the most popular browsers: Chrome (and Chromium-based browsers), Safari, Firefox, Edge, and Opera.