VB2019 paper: Static analysis methods for detection of Microsoft Office exploits
Though the typical malware attack in 2020 arrives by email and is executed via the enabling of Office macros, some attacks exploit (patched) vulnerabilities in Office that allow for the execution of malicious code when someone merely opens the file.
In a paper presented at VB2019 in London, McAfee researcher Chintan Shah presented methods for detecting such Office exploits using static analysis. The tool he wrote detected 80 to 100 per cent of Office exploits that have been used in targeted attacks in the wild.
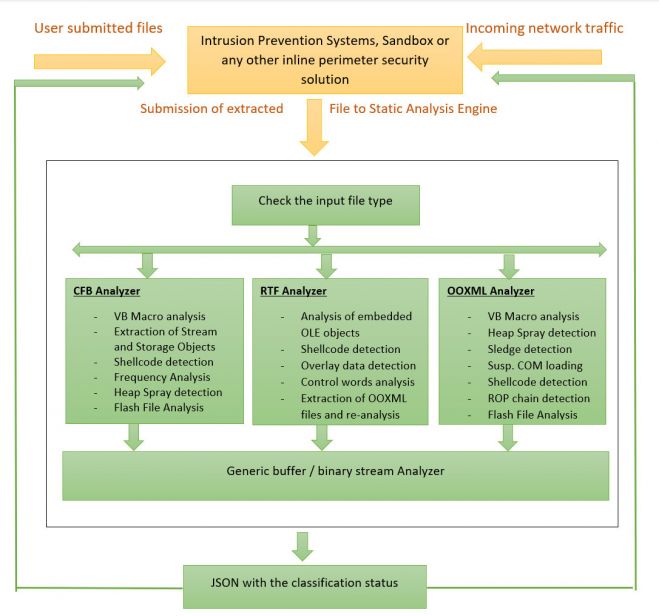 Implementation of the static analysis engine.
Implementation of the static analysis engine.
Today we publish Chintan’s paper in both HTML and PDF format as well as the recording of his VB2019 presentation.
Have you carried out research that furthers our understanding of the threat landscape? Have you discovered a technique that helps in the analysis of malware? The Call for Papers for VB2020 in Dublin is open! Submit your abstract before 15 March for a chance to make it onto the programme of one of the most international threat intelligence conferences.
outertext
https://www.virusbulletin.com/rss