Why Phishers Love New TLDs Like .shop, .top and .xyz
Credit to Author: BrianKrebs| Date: Tue, 03 Dec 2024 13:27:31 +0000
Phishing attacks increased nearly 40 percent in the year ending August 2024, with much of that growth concentrated at a small number of new generic top-level domains (gTLDs) — such as .shop, .top, .xyz — that attract scammers with rock-bottom prices and no meaningful registration requirements, new research finds. Meanwhile, the nonprofit entity that oversees the domain name industry is moving forward with plans to introduce a slew of new gTLDs.

Image: Shutterstock.
A study on phishing data released by Interisle Consulting finds that new gTLDs introduced in the last few years command just 11 percent of the market for new domains, but accounted for roughly 37 percent of cybercrime domains reported between September 2023 and August 2024.
Interisle sources data about cybercrime domains from anti-spam organizations, including the Anti-Phishing Working Group (APWG), the Coalition Against Unsolicited Commercial Email (CAUCE), and the Messaging, Malware, and Mobile Anti-Abuse Working Group (M3AAWG).
The study finds that while .com and .net domains made up approximately half of all domains registered in the past year (more than all of the other TLDs combined) they accounted for just over 40 percent of all cybercrime domains. Interisle says an almost equal share — 37 percent — of cybercrime domains were registered through new gTLDs.
Spammers and scammers gravitate toward domains in the new gTLDs because these registrars tend to offer cheap or free registration with little to no account or identity verification requirements. For example, among the gTLDs with the highest cybercrime domain scores in this year’s study, nine offered registration fees for less than $1, and nearly two dozen offered fees of less than $2.00. By comparison, the cheapest price identified for a .com domain was $5.91.
Currently, there are around 2,500 registrars authorized to sell domains by the Internet Corporation for Assigned Names and Numbers (ICANN), the California nonprofit that oversees the domain industry.
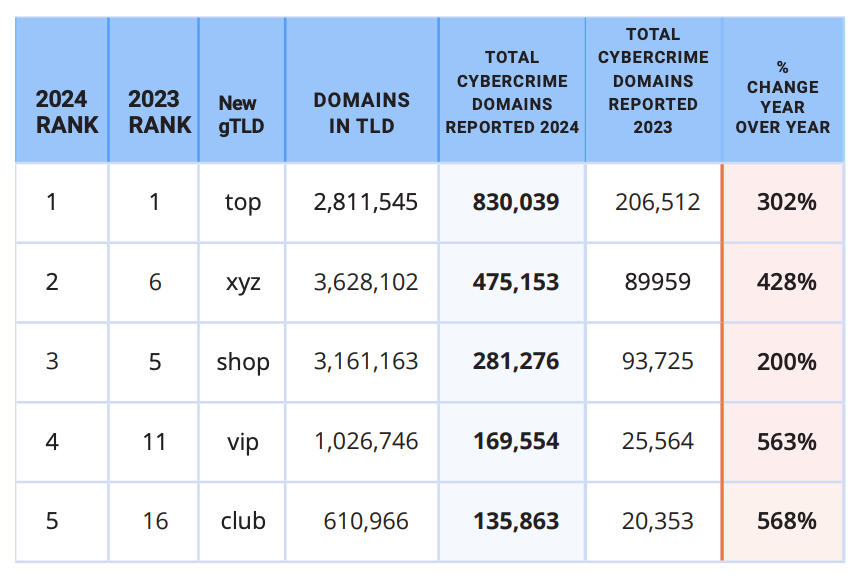
The top 5 new gTLDs, ranked by cybercrime domains reported. Image: Interisle Cybercrime Supply Chain 2014.
Incredibly, despite years of these reports showing phishers heavily abusing new gTLDs, ICANN is shuffling forward on a plan to introduce even more of them. ICANN’s proposed next round envisions accepting applications for new gTLDs in 2026.
John Levine is author of the book “The Internet for Dummies” and president of CAUCE. Levine said adding more TLDs without a much stricter registration policy will likely further expand an already plentiful greenfield for cybercriminals.
“The problem is that ICANN can’t make up their mind whether they are the neutral nonprofit regulator or just the domain speculator trade association,” Levine told KrebsOnSecurity. “But they act a lot more like the latter.”
Levine said the vast majority of new gTLDs have a few thousand domains — a far cry from the number of registrations they would need just to cover the up-front costs of operating a new gTLD (~$180,000-$300,000). New gTLD registrars can quickly attract customers by selling domains cheaply to customers who buy domains in bulk, but that tends to be a losing strategy.
“Selling to criminals and spammers turns out to be lousy business,” Levine said. “You can charge whatever you want on the first year, but you have to charge list price on domain renewals. And criminals and spammers never renew. So if it sounds like the economics makes no sense it’s because the economics makes no sense.”
In virtually all previous spam reports, Interisle found the top brands referenced in phishing attacks were the largest technology companies, including Apple, Facebook, Google and PayPal. But this past year, Interisle found the U.S. Postal Service was by far the most-phished entity, with more than four times the number of phishing domains as the second most-frequent target (Apple).
At least some of that increase is likely from a prolific cybercriminal using the nickname Chenlun, who has been selling phishing kits targeting domestic postal services in the United States and at least a dozen other countries.
Interisle says an increasing number of phishers are eschewing domain registrations altogether, and instead taking advantage of subdomain providers like blogspot.com, pages.dev, and weebly.com. The report notes that cyberattacks hosted at subdomain provider services can be tough to mitigate, because only the subdomain provider can disable malicious accounts or take down malicious web pages.
“Any action upstream, such as blocking the second-level domain, would have an impact across the provider’s whole customer base,” the report observes.
Interisle tracked more than 1.18 million instances of subdomains used for phishing in the past year (a 114 percent increase), and found more than half of those were subdomains at blogspot.com and other services operated by Google.
“Many of these services allow the creation of large numbers of accounts at one time, which is highly exploited by criminals,” the report concludes. “Subdomain providers should limit the number of subdomains (user accounts) a customer can create at one time and suspend automated, high-volume automated account sign-ups – especially using free services.”