Blowing the Whistle on Bad Attribution
Credit to Author: BrianKrebs| Date: Fri, 18 Aug 2017 04:29:51 +0000
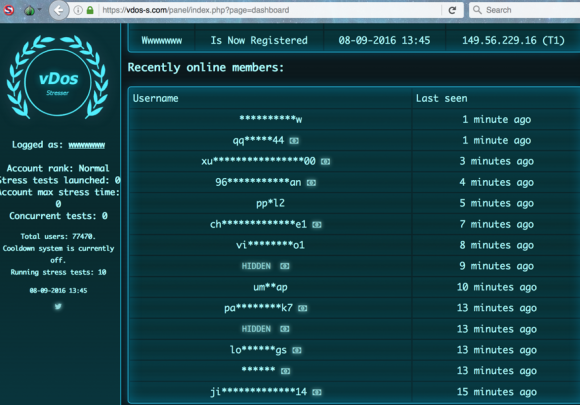
The New York Times this week published a fascinating story about a young programmer in Ukraine who’d turned himself in to the local police. The Times says the man did so after one of his software tools was identified by the U.S. government as part of the arsenal used by Russian hackers suspected of hacking into the Democratic National Committee (DNC) last year. It’s a good read, as long as you can ignore that the premise of the piece is completely wrong.
Read more