Scanning for Flaws, Scoring for Security
Credit to Author: BrianKrebs| Date: Wed, 12 Dec 2018 19:25:14 +0000
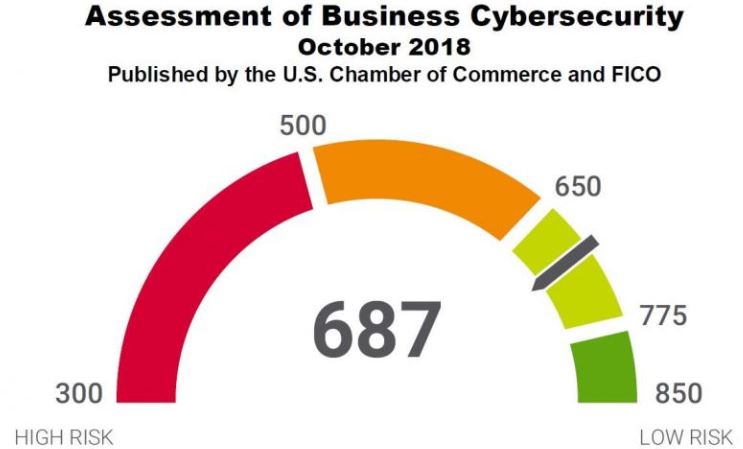
Is it fair to judge an organization’s information security posture simply by looking at its Internet-facing assets for weaknesses commonly sought after and exploited by attackers, such as outdated software or accidentally exposed data and devices? Fair or not, a number of nascent efforts are using just such an approach to derive security scores for companies and entire industries. What’s remarkable is how many organizations don’t make an effort to view their public online assets as the rest of the world sees them — until it’s too late.
Read more