Transatlantic Cable podcast, episode 91
Credit to Author: Jeffrey Esposito| Date: Wed, 08 May 2019 09:18:12 +0000
Dave and Jeff talk about Avengers: Endgame scams, trust in social networks, the new royal baby, and more.
Read moreCredit to Author: Jeffrey Esposito| Date: Wed, 08 May 2019 09:18:12 +0000
Dave and Jeff talk about Avengers: Endgame scams, trust in social networks, the new royal baby, and more.
Read moreCredit to Author: Marina Mash| Date: Tue, 07 May 2019 13:13:11 +0000
This phishing campaign is so convincing that even savvy YouTubers may be duped into giving crooks control of their accounts.
Read more
Credit to Author: Sophos Italia| Date: Wed, 17 Apr 2019 05:18:13 +0000
Ecco come utilizzare il proprio telefono Android come chiave di sicurezza<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/qoRBJ1NgYv4″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Sophos Italia| Date: Wed, 17 Apr 2019 05:18:13 +0000
Ecco come utilizzare il proprio telefono Android come chiave di sicurezza<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/qoRBJ1NgYv4″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Sophos Italia| Date: Wed, 17 Apr 2019 05:18:13 +0000
Ecco come utilizzare il proprio telefono Android come chiave di sicurezza<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/qoRBJ1NgYv4″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Lucas Mearian| Date: Mon, 15 Apr 2019 03:00:00 -0700
In two separate announcements last week, Google and Linux’s Hyperledger project launched tools aimed at enabling secure identity management for enterprises via mobile and other devices.
Google unveiled five upgrades to its BeyondCorp cloud enterprise security service that enables identity and access management for employees, corporate partners, and customers.
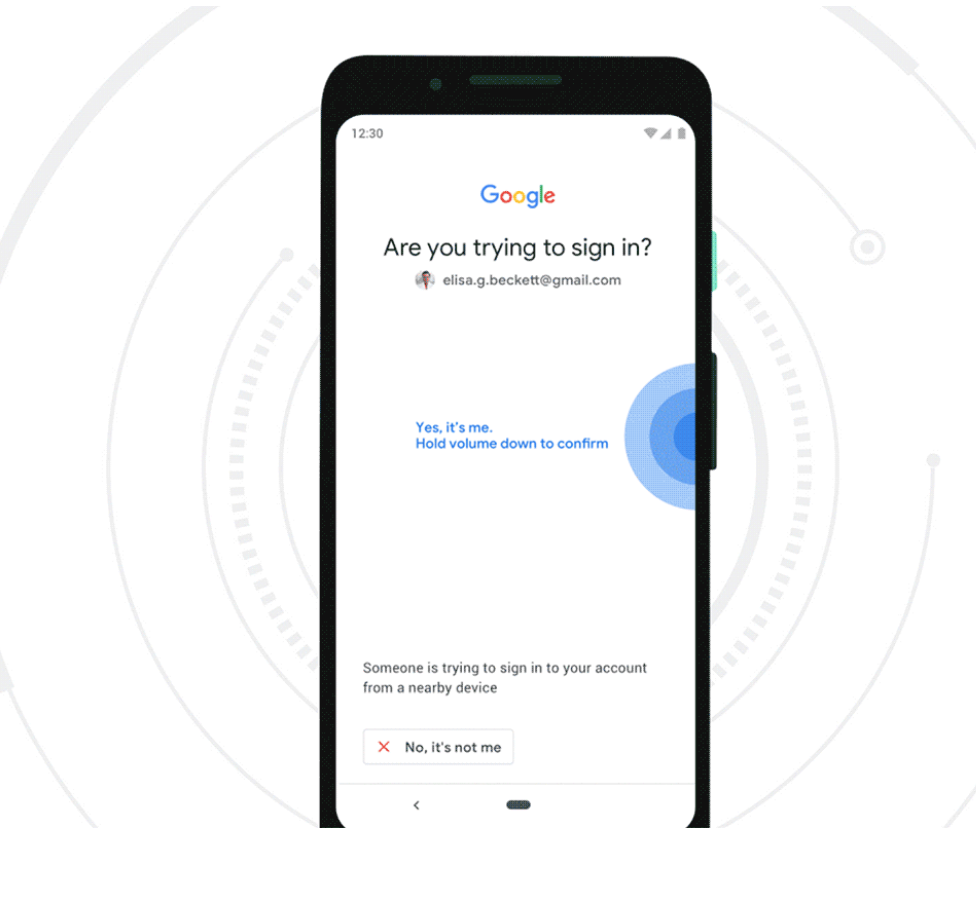
Credit to Author: BrianKrebs| Date: Thu, 11 Apr 2019 16:14:53 +0000
Google this week made it easier for Android users to enable strong 2-factor authentication (2FA) when logging into Google’s various services. The company announced that all phones running Android 7.0 and higher can now be used as Security Keys, an additional authentication layer that helps thwart phishing sites and password theft.
Read moreCredit to Author: David Ruiz| Date: Tue, 02 Apr 2019 15:00:00 +0000
 | |
| For any American company taking steps outside the US market, global data privacy compliance is a question of risk versus reward. Categories: Tags: AfricaamazonArgentinaasiaBahrainBrazilchinaCNILData privacydata privacy lawsdata protection authorityEuropeEuropean UniongdprGeneral Data Protection Regulationglobal data privacyGooglemicrosoftMiddle EastNational Data Protection CommissionPersonal Information Protection ActQatarsingaporeSouth Koreawhitelist |
The post The global data privacy roadmap: a question of risk appeared first on Malwarebytes Labs.
Read more