Fighting Fake EDRs With ‘Credit Ratings’ for Police
Credit to Author: BrianKrebs| Date: Wed, 27 Apr 2022 14:27:35 +0000
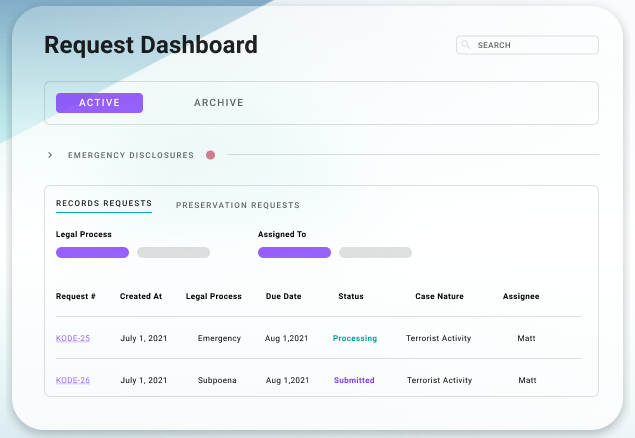
When KrebsOnSecurity last month explored how cybercriminals were using hacked email accounts at police departments worldwide to obtain warrantless Emergency Data Requests (EDRs) from social media and technology providers, many security experts called it a fundamentally unfixable problem. But don’t tell that to Matt Donahue, a former FBI agent who recently quit the agency to launch a startup that aims to help tech companies do a better job screening out phony law enforcement data requests — in part by assigning trustworthiness or “credit ratings” to law enforcement authorities worldwide.
Read more



