Glut of Fake LinkedIn Profiles Pits HR Against the Bots
Credit to Author: BrianKrebs| Date: Wed, 05 Oct 2022 21:20:53 +0000
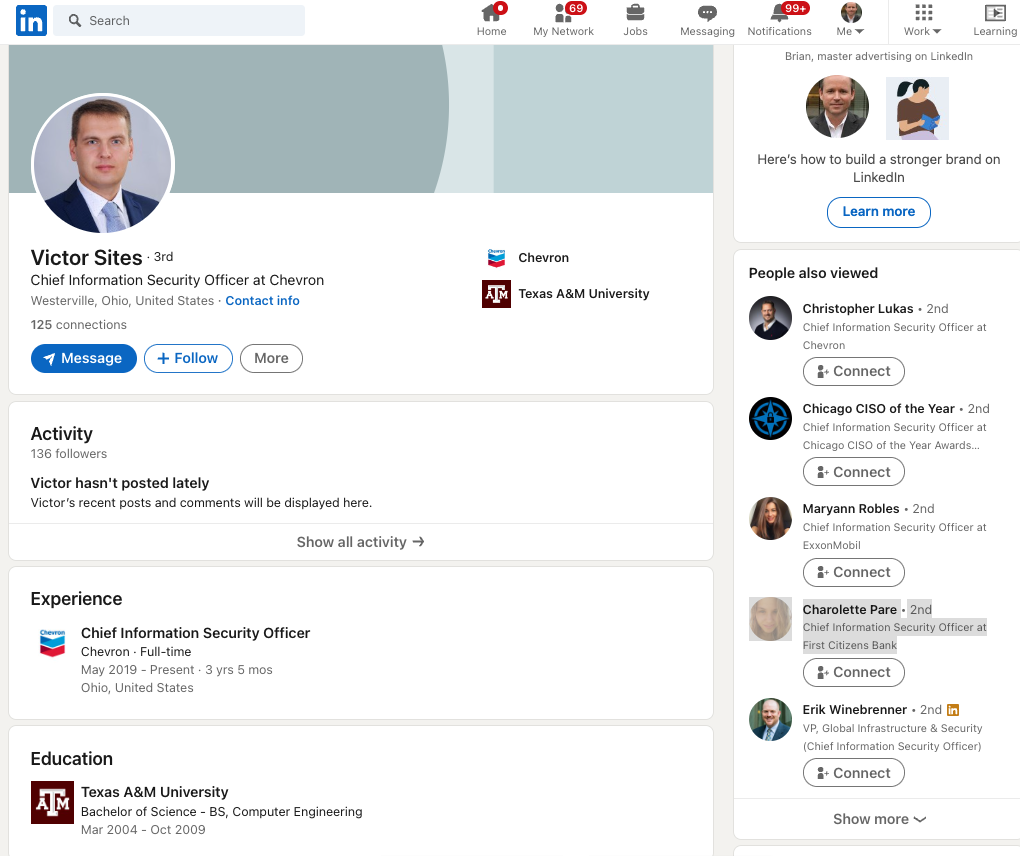
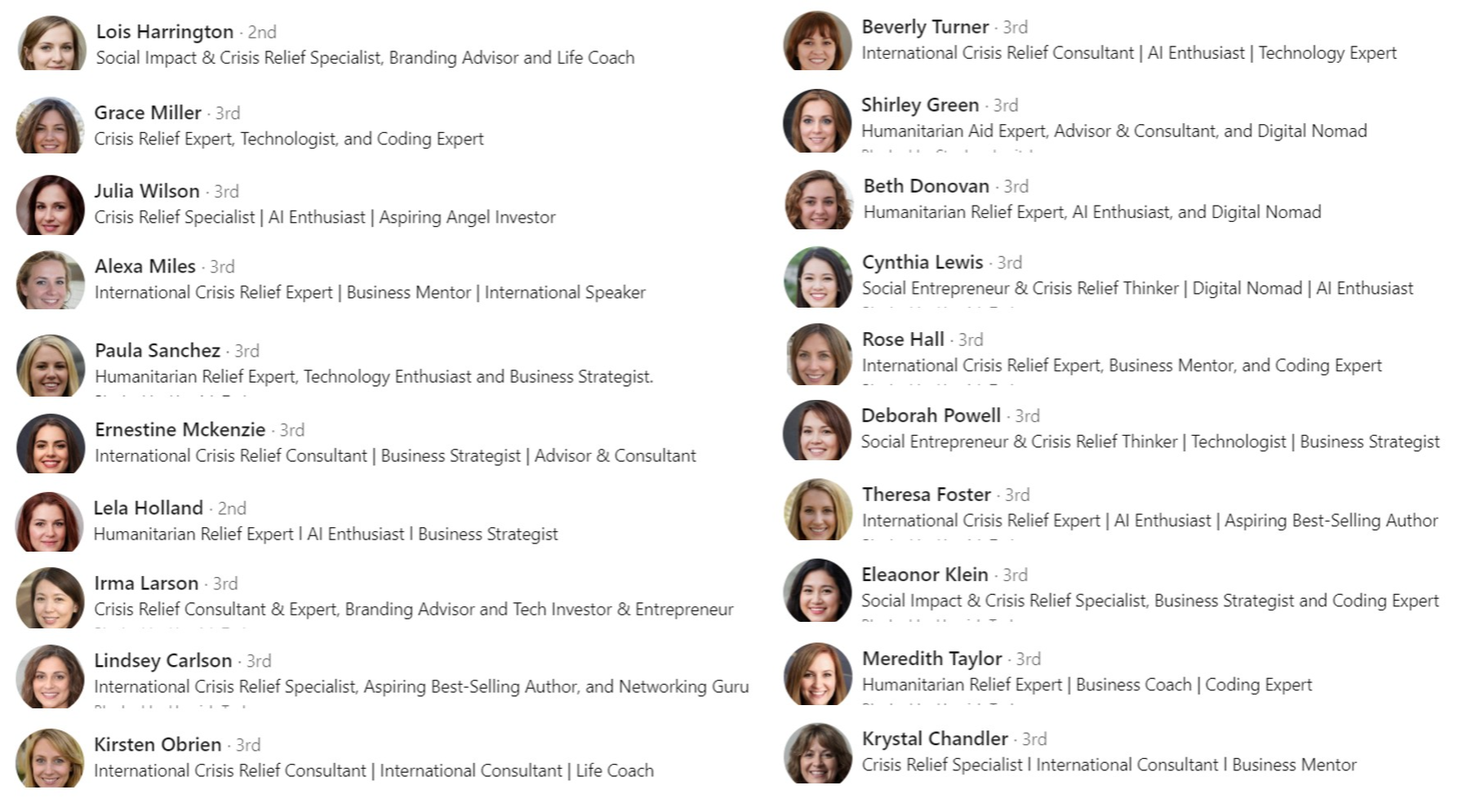
A recent proliferation of phony executive profiles on LinkedIn is creating something of an identity crisis for the business networking site, and for companies that rely on it to hire and screen prospective employees. The fabricated LinkedIn identities — which pair AI-generated profile photos with text lifted from legitimate accounts — are creating major headaches for corporate HR departments and for those managing invite-only LinkedIn groups.
Read more