Turning the screws: The pressure tactics of ransomware gangs
Credit to Author: Matt Wixey| Date: Tue, 06 Aug 2024 10:00:49 +0000
Back in 2021, Sophos X-Ops published an article on the top ten ways ransomware operators ramp up pressure on their targets, in an attempt to get them to pay. Last year, X-Ops revealed that threat actors have since developed a symbiotic relationship with sections of the media, leveraging news articles as extortion pressure. Three years on, threat actors continue to adapt and change their tactics to increase leverage against their targets.
The methods we described in the 2021 article – such as threats to publish data, calling employees, and notifying customers and the media about breaches – are all still in use today. However, ransomware gangs are adopting some new, and concerning, tactics.
A brief summary of our findings:
- Ransomware operators increasingly weaponize legitimate entities – such as the news media, legislation, civil regulatory enforcement authorities, and even law enforcement – to ramp up pressure on victims
- In some cases, criminals encourage affected customers and employees to claim compensation, or launch litigation – sometimes providing the names and contact details of CEOs and business owners
- Threat actors claim to assess stolen data for evidence of illegal activity, regulatory noncompliance, and financial discrepancies – all of which can be used as further leverage and to inflict reputational damage
- Ransomware criminals openly criticize their victims, and will sometimes attempt to deride them as unethical or negligent, which can also cause reputational damage – as well as contributing to some threat actor groups’ attempts to ‘flip the script’ and portray themselves as beneficent vigilantes
- Ransomware operators appear to be increasingly comfortable with stealing and leaking extremely sensitive data, including medical records, nude images, and, in one case (as we’ll cover later), the personal details of a CEO’s daughter
Legislation and litigation
Something we didn’t see much, if any of, in 2021 was ransomware actors weaponizing legislation, or encouraging secondary victims of their attacks – such as clients, customers, and employees – to launch lawsuits, in order to increase pressure on targeted organizations. However, we’ve seen several recent examples of this.
In November 2023, ALPHV/BlackCat filed a Security and Exchange Commission (SEC) complaint against one of its own victims. The threat actor alleged that the company had failed to notify the SEC of the breach within the four days required under the new final rules (which, while adopted in July 2023, did not actually come into force until December of that year).
We saw threats to expose non-compliance in other contexts, too. In some cases, it’s something for which threat actors appear to be specifically searching. As we reported in our December 2023 piece on the relationship between ransomware gangs and the media, at least one threat actor appears to be actively recruiting for people to look for instances of non-compliance and financial irregularities – possibly to use this as leverage for extortion.
Figure 1: A threat actor posts a recruitment ad on a criminal forum, seeking someone to look for “violations,” “inappropriate spending,” “discrepancies,” and “cooperation with companies on sanction lists.” It’s not clear that this is linked specifically to ransomware
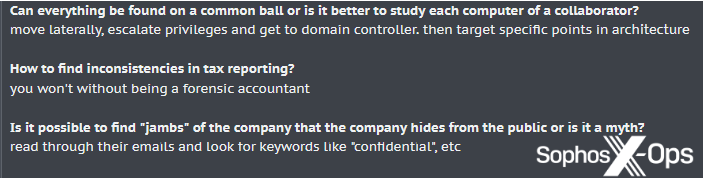
It’s worth noting that this sort of activity can require considerable expertise – as noted by one threat actor on a criminal forum below (Figure 2) – but is likely still attractive to ransomware operators if it provides them with more ammunition.
Figure 2: A threat actor provides some advice on finding “inconsistencies in tax reporting” on a criminal forum
At least one other ransomware group claims to do this type of research. The WereWolves threat actor notes, on its leak site, that it subjects stolen data to “a criminal legal assessment, a commercial assessment and an assessment in terms of insider information for competitors.”
Figure 3: An excerpt from the WereWolves ransomware leak site
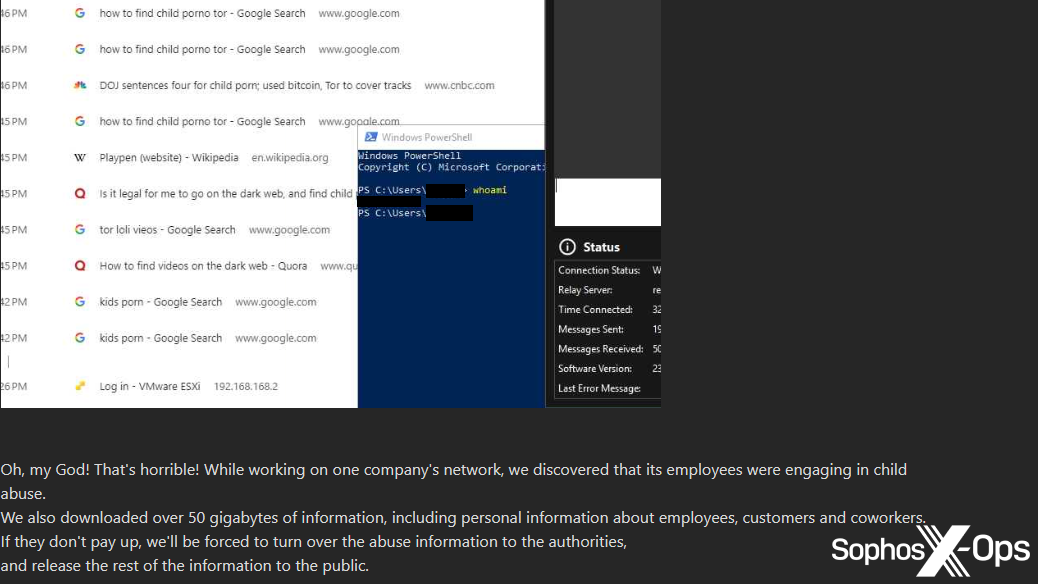
We noted one particularly disturbing example, where the Monti ransomware gang claimed that an employee at a compromised organization had been searching for child sexual abuse material. The threat actor posted a screenshot of a browser history window, along with a PowerShell window showing the alleged username of the offender. Monti went on to state that “if they don’t pay up, we’ll be forced to turn over the abuse information to the authorities, and release the rest of the information to the public.”
Figure 4: Part of a post on the Monti ransomware leak site
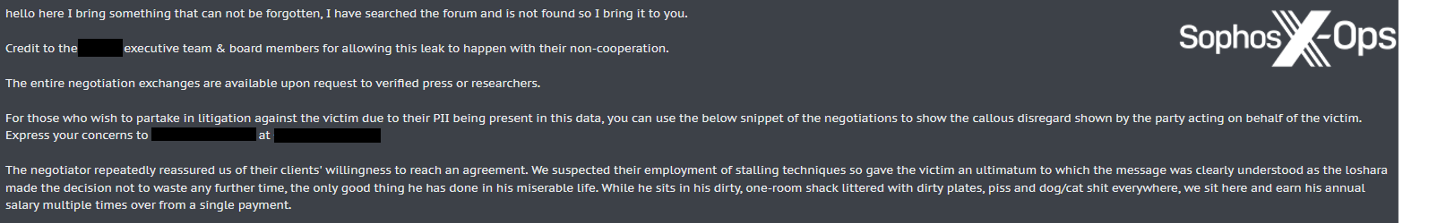
We also noted an instance of a threat actor encouraging people whose personally identifiable information (PII) appeared in a data breach to “partake in litigation against the victim.” Moreover, the threat actor also provided a “snippet of the negotiations” and encouraged those affected to “express your concerns” to an executive at the targeted organization – providing not just that individual’s name, but also their telephone number.
Figure 5: A threat actor posts on a criminal forum, providing material for “those who wish to partake in litigation against the victim”
This tactic of naming specific individuals – along with contact details – is used by more than one ransomware gang. The Qiulong group, for example, regularly includes the details of CEOs and business owners on its leak site, often accompanied by insults, personal information, and accusations of negligence.
Figure 6: A post on the Qiulong ransomware leak site. Note the reference (redacted in the image above) to a specific make of car the CEO drives
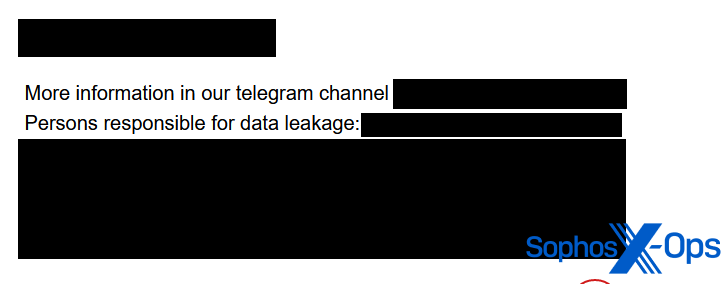
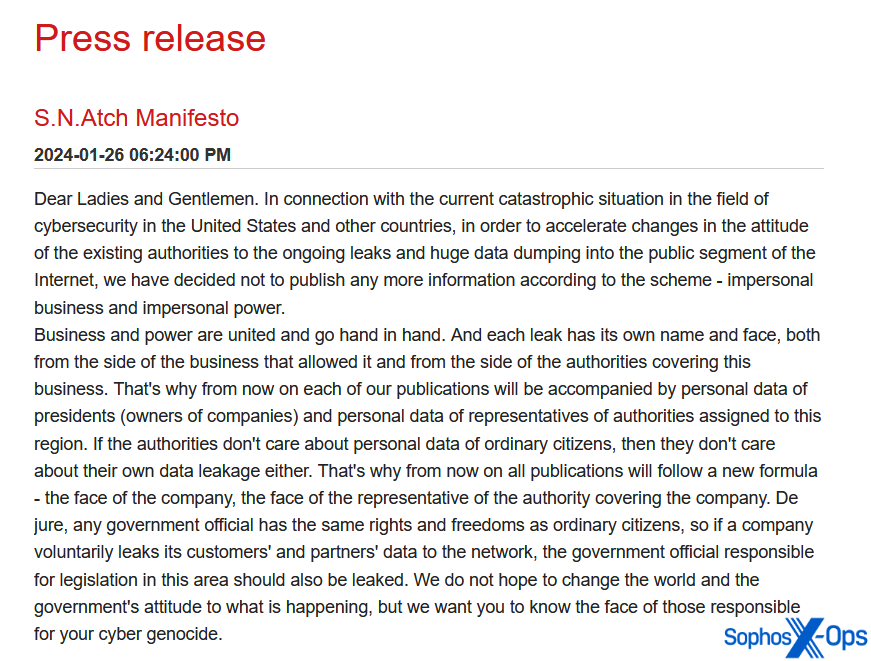
Similarly, the Snatch threat actor regularly names specific individuals as “responsible” for data breaches.
Figure 7: A post on the Snatch leak site, which names a specific individual who Snatch claims is “responsible for data leakage”
Figure 8: The Snatch threat actor explains its reasoning for including the personal data of business owners and authority figures on its leak site
In one case, we noted that the Monti ransomware group had not just named a business owner and published their Social Security number, but had also posted an image of them, crudely edited to include devil horns and a speech bubble reading “I’m a dumb p***y who doesn’t care about my clients.”
From the perspective of ransomware operators, referring to specific individuals serves three purposes. First, it provides a ‘lightning rod’ for any subsequent blame, pressure, and/or litigation. Second, it contributes to the threat of reputational damage (covered in the next section). And third, personal attacks can menace and intimidate the leadership of the targeted organization.
It may seem somewhat ironic that threat actors are weaponizing legislation to achieve their own illegal objectives, and the extent to which this tactic has been successful is unclear. However, when used, it likely adds to the already considerable pressure experienced by C-suite executives – particularly in the context of at least one CEO previously being convicted following legal action related to a ransomware attack. While out of scope for this particular article, it’s worth noting that the current legal landscape pertaining to the personal risk and accountability of CEOs and CISOs in such situations appears uncertain. While we’re not aware of any convictions arising from ransomware groups referring breach information to regulators or law enforcement, that doesn’t mean it won’t happen in the future – and the possibility is likely to be of concern to C-suites.
Moreover, the fact that some ransomware operators claim to take a vigilante role to expose wrongdoing, irregularities, and criminal activity within organizations presents an interesting ethical issue, despite the irony that doing so supports their own criminal activity.
Ethics, reputational damage, and embarrassment
In Figure 4 above, the WereWolves ransomware group claimed to expose (and threatened to report) serious criminal activity allegedly occurring at an organization. While this in no way negates the illegality and seriousness of ransomware attacks, it raises an ethical dilemma: Which is worse, the ransomware attack itself, or the attackers’ revelation of potentially criminal activity taking place within the organization that was victimized?
Many ransomware criminals thrive in this ethical grey area, and want to appear moral, ethical, or genuinely concerned about security and confidentiality. As we noted in our previous article on this topic, numerous ransomware gangs are attempting to ‘flip the script’ and portray themselves as a force for good, by referring to themselves as “honest…pentesters”, or as a “penetration testing service” conducting “cybersecurity [studies]” or “security audit[s].” Of course, legitimate penetration testers operate with the prior permission of, and under parameters set by (and sometimes, active supervision by) the companies who hire them; ransomware criminals do not.
Cactus, for instance, describes itself as a “Direct Security Audit Agency (DSAA) revolutionizing a customer journey, one hyper-targeted solution at a time.” The language here is – probably intentionally – reminiscent of corporate marketing material.
Figure 9: On the FAQ page on its leak site, the Cactus ransomware group claims that it conducts “network security audits”
In contrast, many ransomware gangs refer to their targets as “irresponsible,” “negligent,” or uncaring.
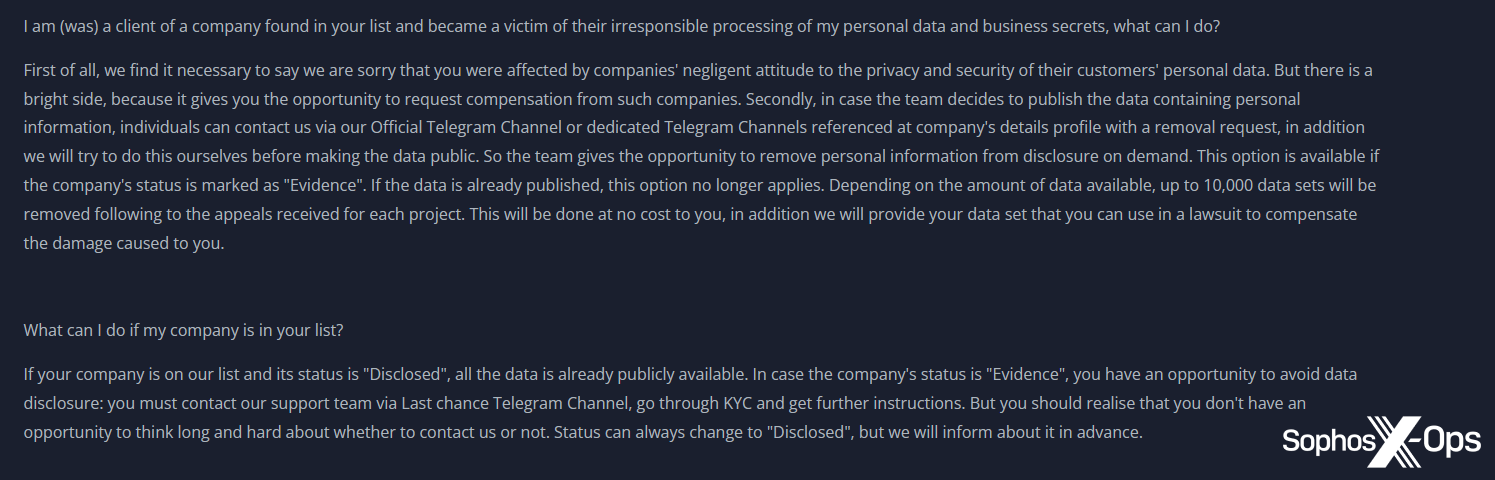
Figure 10: The 8Base leak site mentions “irresponsible processing of…personal data and business secrets” and includes the statement that “we are sorry that you were affected by companies’ negligent attitude to the privacy and security of their customers’ personal data.” Note the claim that this “gives you the opportunity to request compensation”
Of particular interest in Figure 10 is 8Base’s promise that they will “remove personal information from disclosure on demand…at no cost to you,” following requests from individual clients of the targeted organization.
Again, this is (perhaps) an attempt to make the group appear reasonable and ethical, but it’s also combined with a pressure tactic aimed at the organization. In the same paragraph, 8Base notes that “in addition we will provide your data set that you can use in a lawsuit to compensate the damage caused to you.”
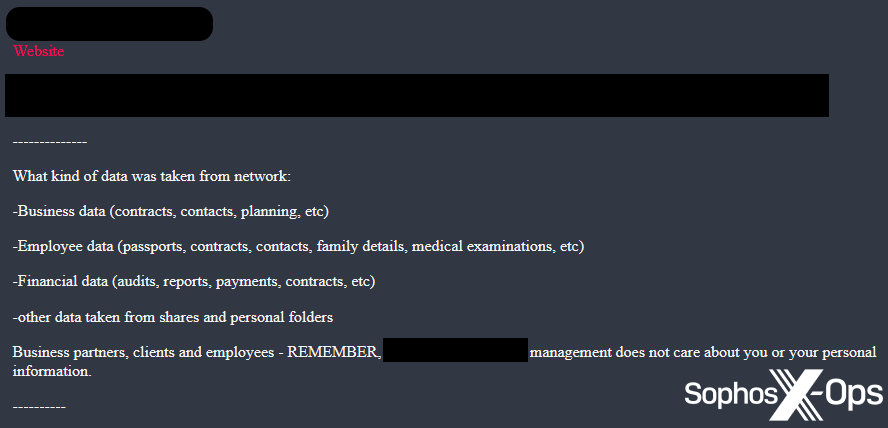
Figure 11: In a post on its leak site, the Blacksuit ransomware group claims that the management of a targeted organization “does not care about you or your personal information”
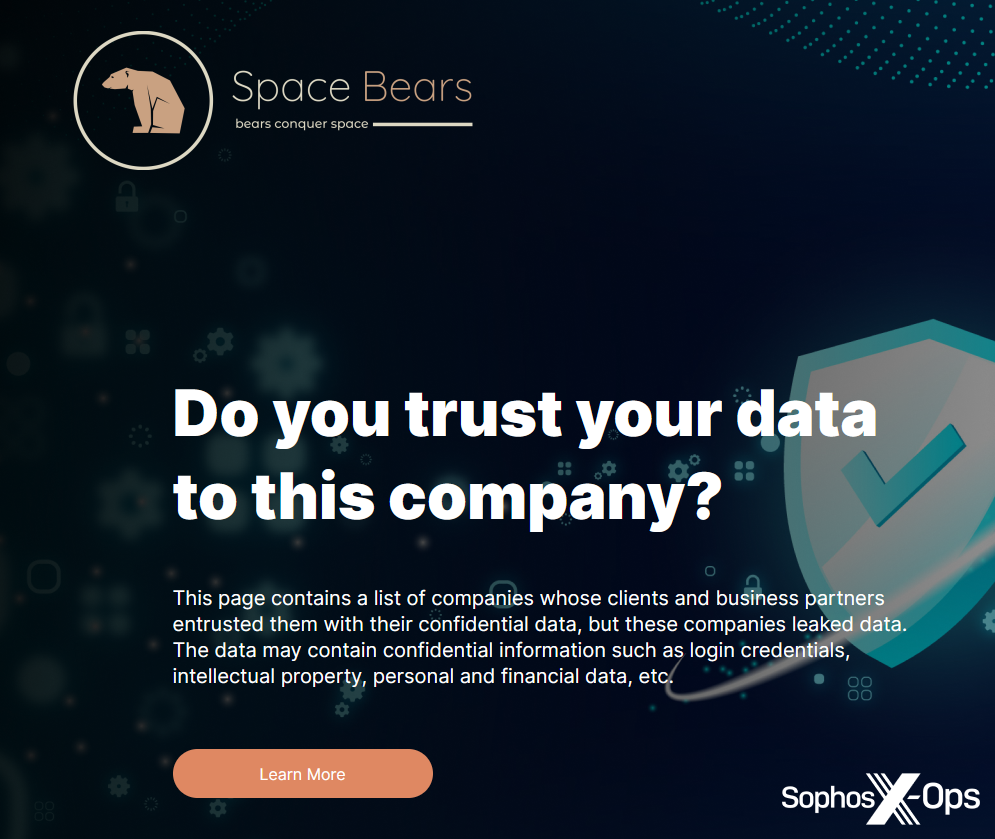
Figure 12: A screenshot of the Space Bears leak site, asking visitors whether they trust targeted companies with their data
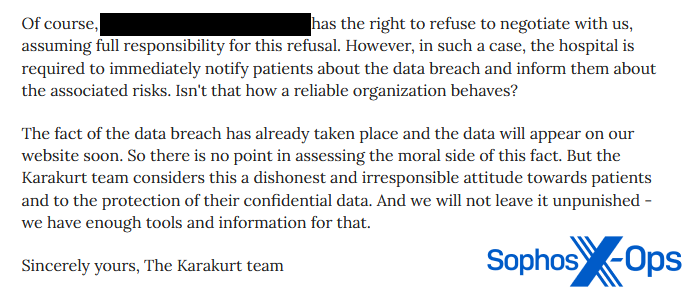
In many cases, this criticism continues after negotiations have broken down and victims have decided not to pay. For instance, the Karakurt group, in a ‘press release,’ called out a hospital after it failed to pay a ransom.
Figure 13: The Karakurt group criticizes a hospital after it failed to pay the ransom, calling it “dishonest and irresponsible”
Typically, in the context of exposing security weaknesses and negligence, ransomware operators portray themselves as morally superior to their targets. Occasionally, the waters are muddied further.
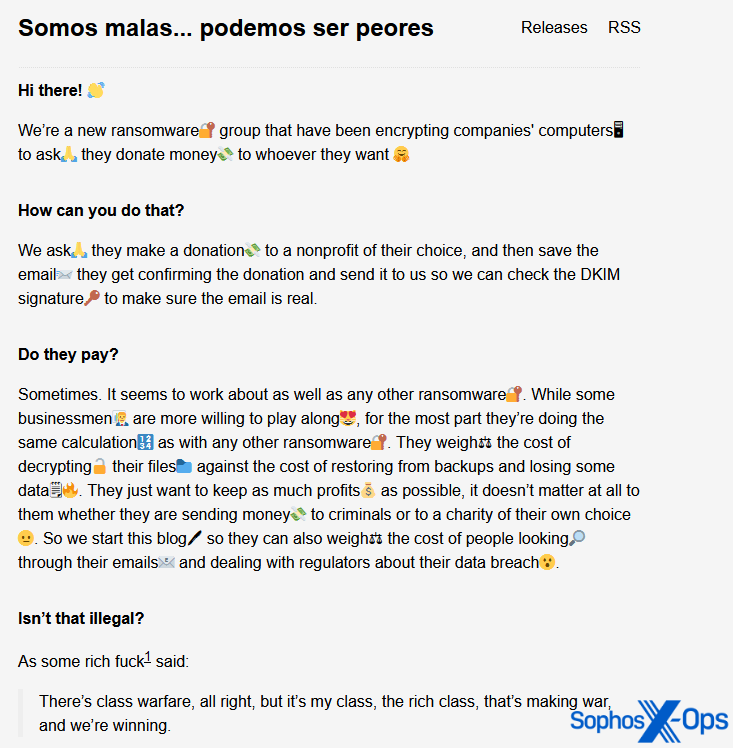
The Malas ransomware gang, for example, demands that its victims “make a donation to a nonprofit of their choice.”
Figure 14: An excerpt from a post on the Malas ransomware gang’s leak site. The quotation in the last response is attributed to financier Warren Buffet
Other threat actors have previously adopted a similar approach. In 2022, for example, the GoodWill ransomware group demanded that victims perform charitable activities – such as feeding poor children, or providing clothes and blankets to the unhoused – and post video evidence online. In 2020, the Darkside ransomware gang claimed to have donated a proportion of its gains to two charities. As far as we can tell, there were no known victims of the GoodWill ransomware strain, so we don’t know if the tactic was successful, and at least one of the two charities to which Darkside donated funds stated that it would not be keeping the money.
Malas, however, takes things a step further. In addition to requiring charitable donations, it also explicitly criticizes specific organizations on the basis of alleged ethical shortcomings – arguably combining ransomware with hacktivism.
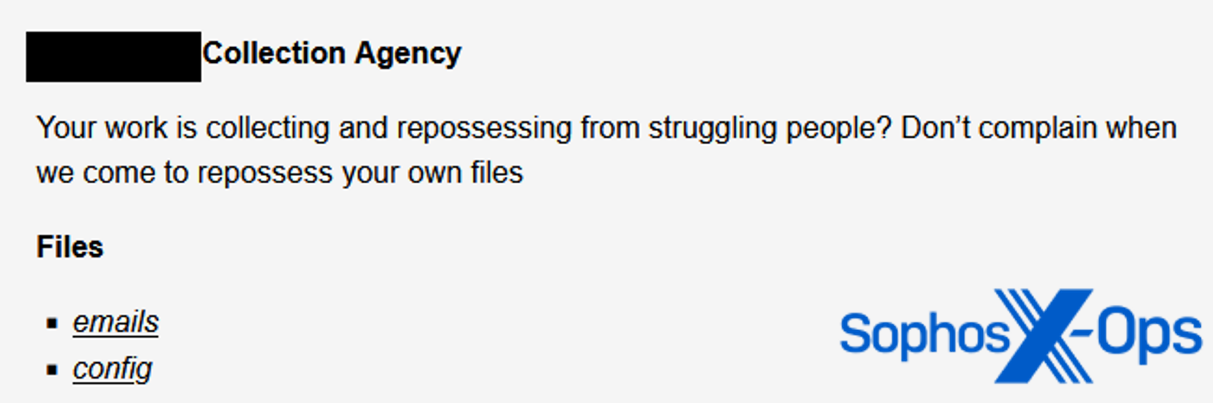
Figure 15: A post on the Malas leak site following an attack on a collection agency (a company that attempts to recover debts on behalf of creditors)
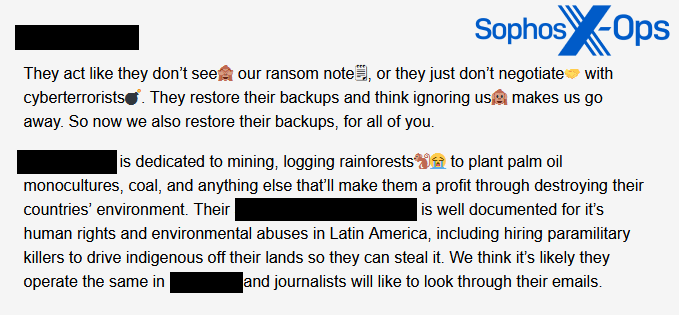
Figure 16: Another post on the Malas leak site, referring to an attack on an organization in the natural resources sector
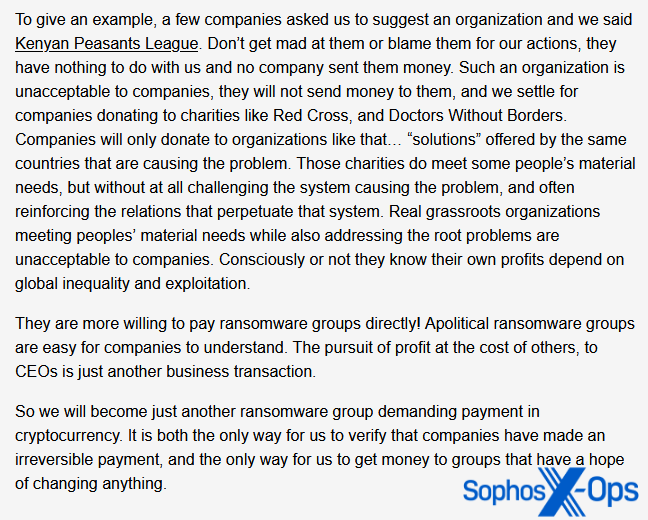
Malas admits that this approach has not been particularly successful. On its FAQ, its response to the question “Has it been effective?” is an unequivocal “So far, no.” Interestingly, the author of the FAQ claims that one of the reasons for this is that victims “won’t send money to genuine grass-roots organizations.”
Figure 17: Malas goes into some detail as to why it believes its approach has not been effective
However, in attempting to present its targets as morally deficient, Malas is essentially no different to its peers. It leverages the threat of reputational damage, in the same way that other ransomware gangs do. The intent is to reduce trust and good faith, with the proposed solution being for the target to pay up and therefore negate, at least partially, any adverse impact.
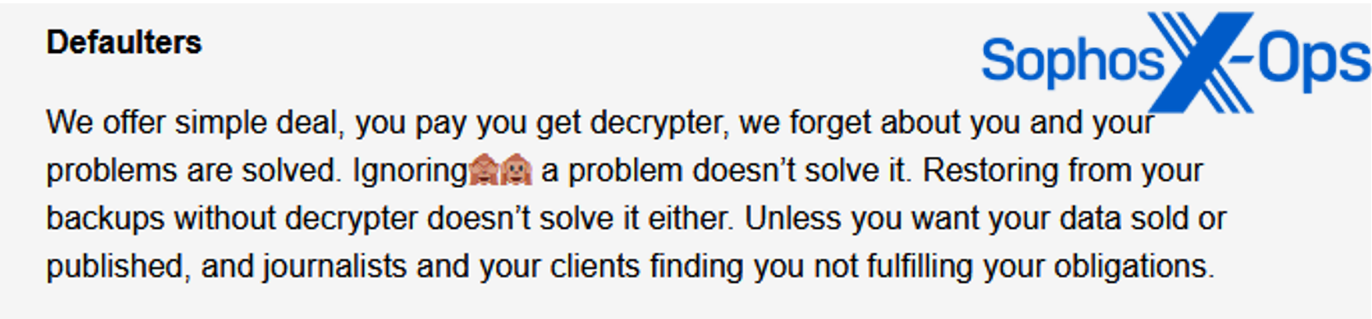
Malas is also no different to its peers when it comes to its communications with victims. Like other ransomware groups, it threatens to sell or publish data and inform journalists and customers.
Figure 18: An excerpt from the Malas leak site
The prevalence of this threat was something we noted both in our article on ransomware gangs and the media, and in our 2021 examination of ransomware pressure tactics. Conscious that many news outlets are keen to publish stories on ransomware, and that media attention may compound reputational damage to organizations and increase the pressure to pay up, many ransomware gangs explicitly make this threat on their leak sites, and will solicit media coverage and communication with journalists.
In addition, some threat actors also threaten to notify customers, partners, and competitors. The intent here is to generate and intensify pressure from multiple angles and sources: media attention, customers, clients, other companies, and potentially regulatory bodies too.
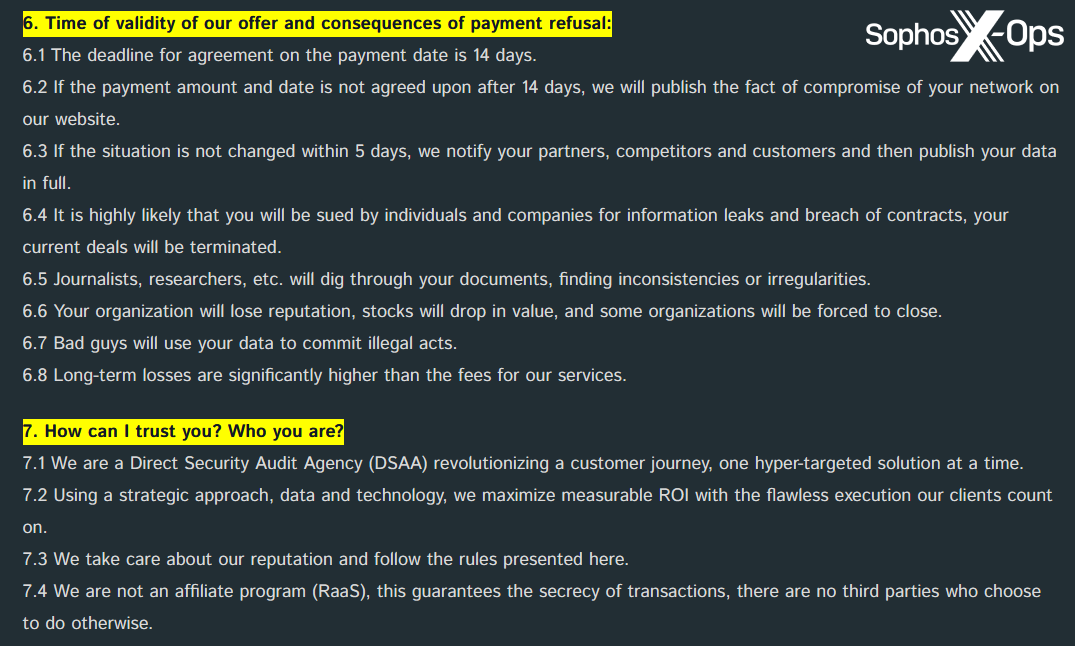
Figure 19: An excerpt from the FAQ on the Cactus leak site. Note the threats that “it is highly likely that you will be sued,” and that “journalists, researchers, etc. will dig through your documents, finding inconsistencies or irregularities”
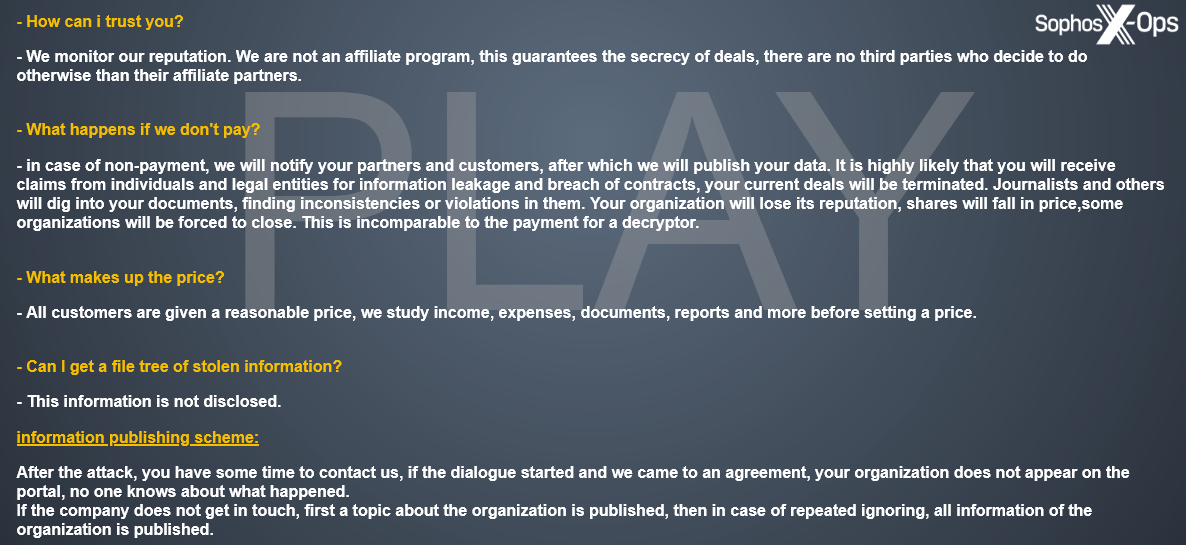
Figure 20: An excerpt from the FAQ on the Play leak site. Note that there is some similar wording to the Cactus notice in Figure 19, in the answer to the “What happens if we don’t pay?” question
We noted in our 2021 article that the threat of leaked personal data was a big concern for organizations (and, of course, for the individuals involved), with both privacy and potential legal ramifications. While this is still the case, in recent years ransomware gangs have stepped up their game, sometimes leaking, or threatening to leak, particularly sensitive data.
Sensitive data, swatting, and more
Several ransomware groups have published sensitive medical data following attacks. This has included mental health records, the medical records of children, and, recently, blood test data.
In a world where data breaches are increasingly commonplace, threatening to leak extremely sensitive data exacerbates the pressure on victim organizations, and can cause considerable distress and concern to those affected.
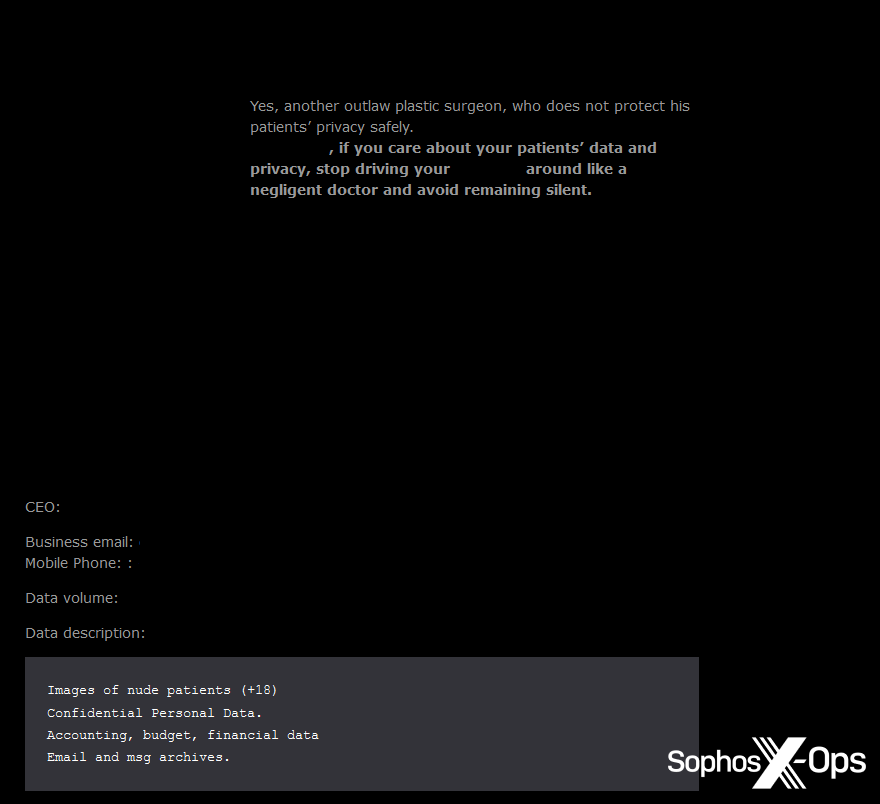
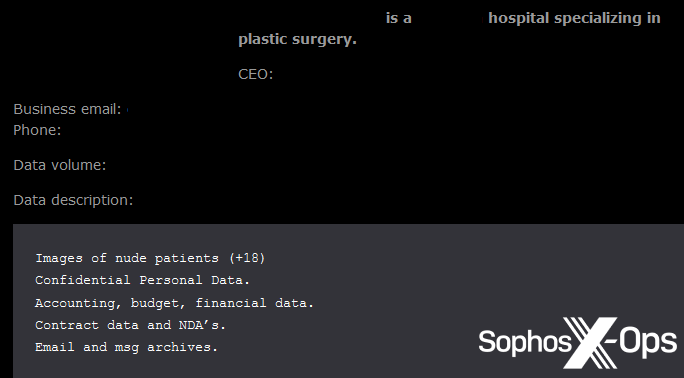
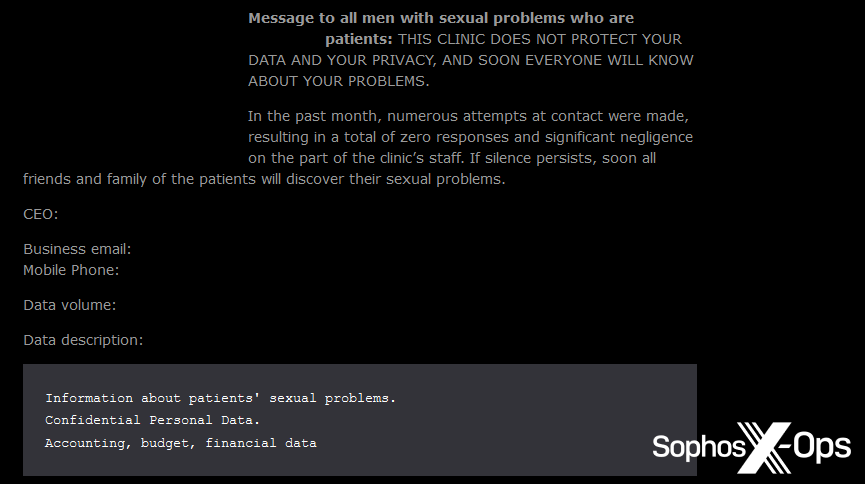
In some cases, we noticed ransomware gangs explicitly calling this out on their leak site – noting that stolen data included “images of nude patients” and “information about patients’ sexual problems.”
Figure 21: A post on the Qiulong leak site
Figure 22: Another post on the Qiulong leak site
In one particularly concerning example, the Qiulong ransomware group posted screenshots of a CEO’s daughter’s identity documents, along with a link to her Instagram profile.
Figure 23: The Qiulong ransomware group posts personal data of a CEO’s daughter on its leak site. From the limited context provided, this may have been an act of revenge after negotiations had broken down
In 2021, we noted that ransomware gangs would sometimes email and call employees and customers in order to increase pressure on organizations. However, in recent years, threat actors appear to be increasingly interested in not merely threatening organizations directly, but also secondary victims, as in Figure 23. For instance, as reported in January 2024, attackers threatened to ‘swat’ patients of a cancer hospital, and have sent threatening text messages to a CEO’s spouse.
As we wrote in 2021, ransomware operators will often warn their victims not to contact law enforcement. However, the threat of swatting demonstrates some attackers’ willingness to weaponize law enforcement when it suits them – not unlike their willingness to weaponize legislation and regulations.
An escalation in tactics
While many ransomware gangs are still using the pressure tactics we reported on in 2021, there appears to have been an escalation. It’s not certain whether this is driven by increasing numbers of victims opting not to pay ransoms, competition from other threat actors, ransomware groups feeling increasingly emboldened, or other factors. However, what is apparent is that all the tactics we discuss here are designed to intimidate targeted organizations and people linked to them.
Some ransomware groups will weaponize any legitimate resource to increase the pressure on their targets – whether that’s the news media, as we explored in our earlier article, law enforcement, or threats of civil legal action or reporting malfeasance to regulatory authorities. While it’s probably too early to say if this approach is effective (and, it’s also worth noting, the threat isn’t always carried out), the criminals’ objective is to generate pressure from multiple angles and sources.
The use of phone calls and swatting also indicate a willingness to move threats from the digital sphere and into the real world. Swatting, in particular, is an extremely dangerous crime that has on some occasions resulted in injury and death, as well as significant psychological distress.
In the future, ransomware gangs appear likely to continue to devise and employ novel strategies to coerce their victims into paying, and to inflict reputational damage – and perhaps worse – if ransoms are not paid.
Sophos has several resources to help defenders protect against ransomware. You can find best practice guidance, an anti-ransomware toolkit, a link to our incident response services, and links to several of our ransomware-related reports here. Specific advice on configuring Sophos products to prevent ransomware is also available.