Known ransomware attacks up 68% in 2023
Today, Malwarebytes released its 2024 State of Malware report, detailing six cyberthreats that resource-constrained IT teams should pay attention to in 2024. Top of the list is “Big Game” ransomware, the most serious cyberthreat to businesses all around the world.
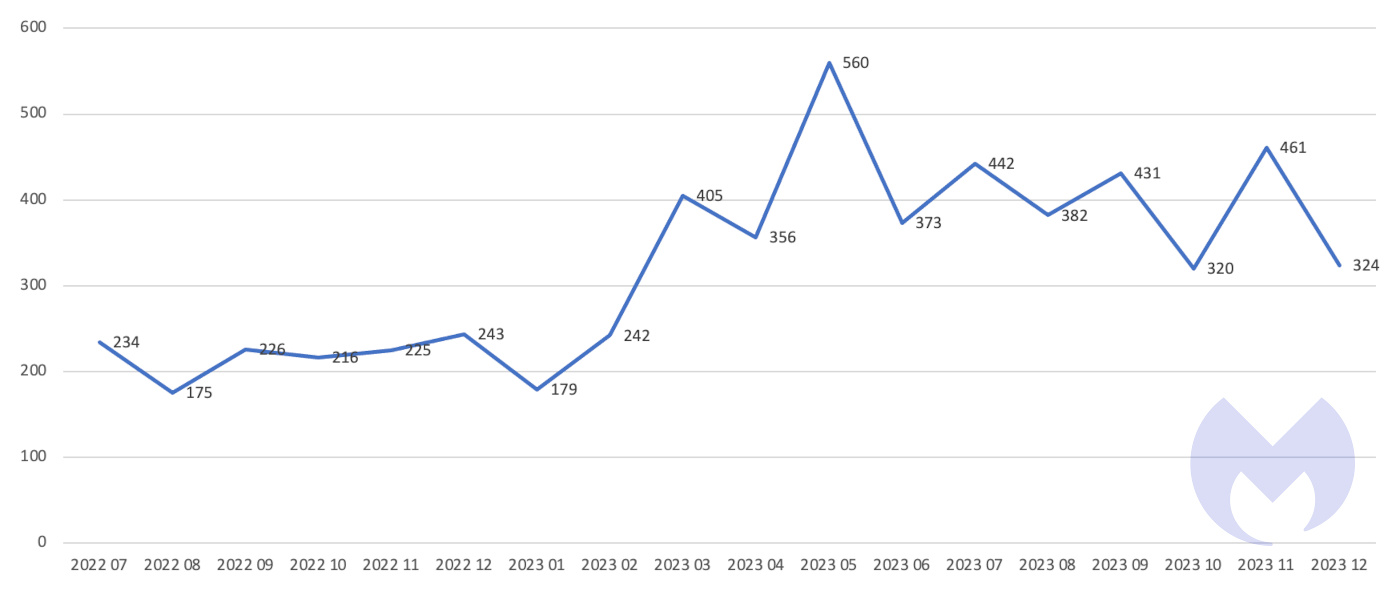
Big game attacks extort vast ransoms from organizations by holding their data hostage—either with encryption, the threat of damaging data leaks, or both. The report reveals that, awash with money, the number of known Big Game attacks surged by 68% in 2023, thanks to Ransomware-as-a-Service groups like LockBit and ALPHV.
Big Game ransomware is just one part of a thriving and highly organized cybercrime business—a multi-billion-dollar mirror to the legitimate economy it feeds off. Its ecosystem supports entire supply chains, dotted about with specialized organizations like access brokers and malicious software vendors. It has brand names, PR stunts, HR departments, incentive schemes, and “employees of the month.”
And like broader, law-abiding “Business” at large, cybercrime has settled on a collection of tools that work. Its activity is built around evergreen techniques like phishing, software exploits, and password guessing, along with mature malicious technologies like info stealers, trojans, and ransomware.
For years, the latest iterations of these ideas have only offered marginal improvements on their predecessors. As a result, innovation in cybercrime has increasingly shifted towards tactics—advancements that focus more on how attacks can succeed and less on what malware can do. The 2024 State of Malware report also details how ransomware gangs use Living of the Land (LotL) techniques to hide in plain sight, and how one gang, CL0P, turned to automated zero-day attacks to break ransomware’s scalability barrier.
The report also explains how cybercriminals turned to a tactic called “malvertising” in 2023, using search ads and disposable websites that mimic legitimate brands to distribute malware as an alternative to malicious emails and document macros.
And as Macs continued to buck the trend in declining PC sales, some criminals began to add Mac malware, like Atomic Stealer, to their Windows distribution channels.
As we enter 2024, malware is as dangerous as ever, but when it is used, it is just one link in an attack chain of multiple different threats. IT and security teams now face active adversaries, zero-day exploits, compromised accounts, social engineering, and a range of other threats that don’t meet the traditional definition of malware. Against this backdrop, security budgets are shrinking while resource-constrained IT and security teams firefight ever more complex environments.
When it comes to security, “more of the same” will not work in 2024, so this year’s report also outlines what effective cyberdefense in the year ahead will require.
To learn more about the most serious threats facing IT teams in 2024, and how to combat them, download the 2024 State of Malware report.