The scammers who scam scammers on cybercrime forums: Part 2
Credit to Author: Matt Wixey| Date: Wed, 14 Dec 2022 12:00:20 +0000
Following on from the first chapter of our investigation into scammers who scam scammers, we turn to the variety of scams on criminal marketplaces – which range from crude ‘rip-and-runs’ to sophisticated, long-term efforts.
Rip-and-run
One of the most common scams, a ‘rip-and-run’ can work in two ways: A buyer receives goods but doesn’t pay for them, or a seller receives payment but doesn’t deliver. That’s the ‘rip.’ The ‘run’ part means that the scammer goes dark, refusing to answer messages or disappearing from the forum altogether.
Rip-and-runs usually involve small amounts, but there are exceptions.
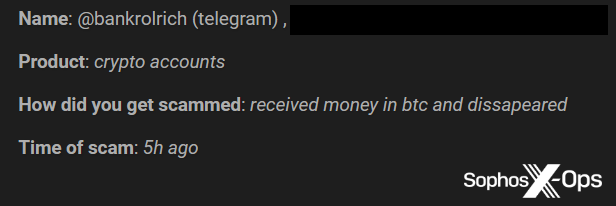
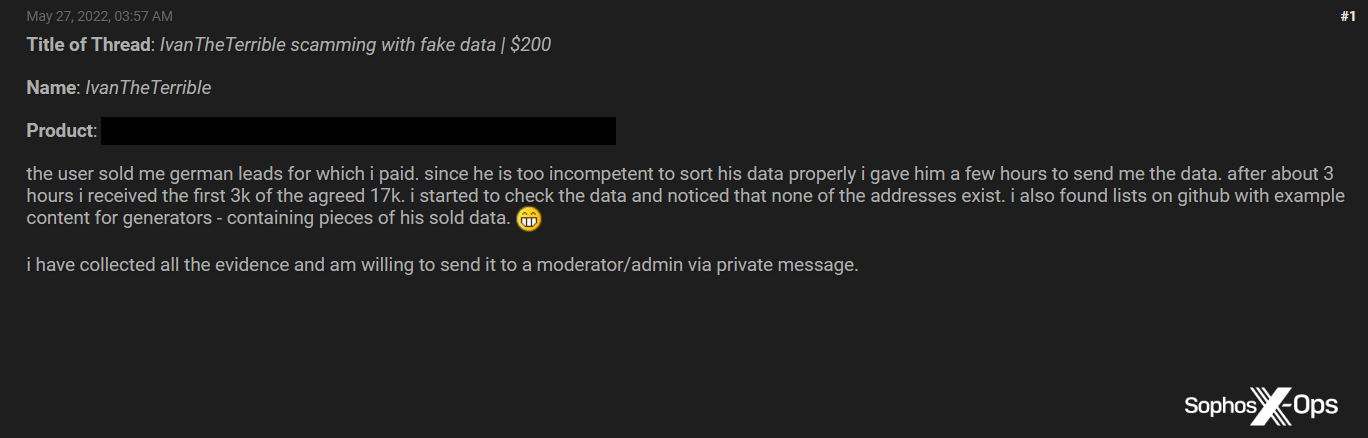
Figure 1: A simple example of a rip-and-run scam on BreachForums, involving $200 USD
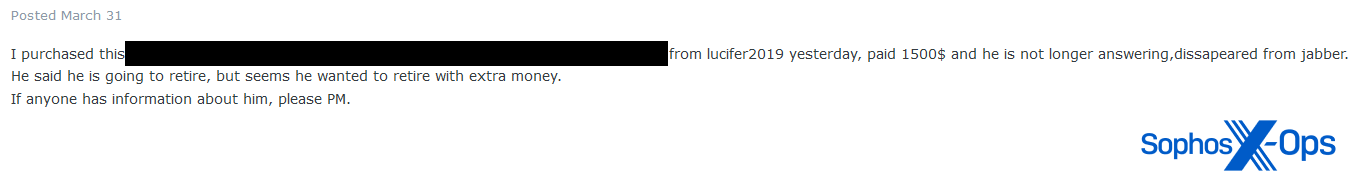
Figure 2: A higher-value rip-and-run on Exploit, for $1500
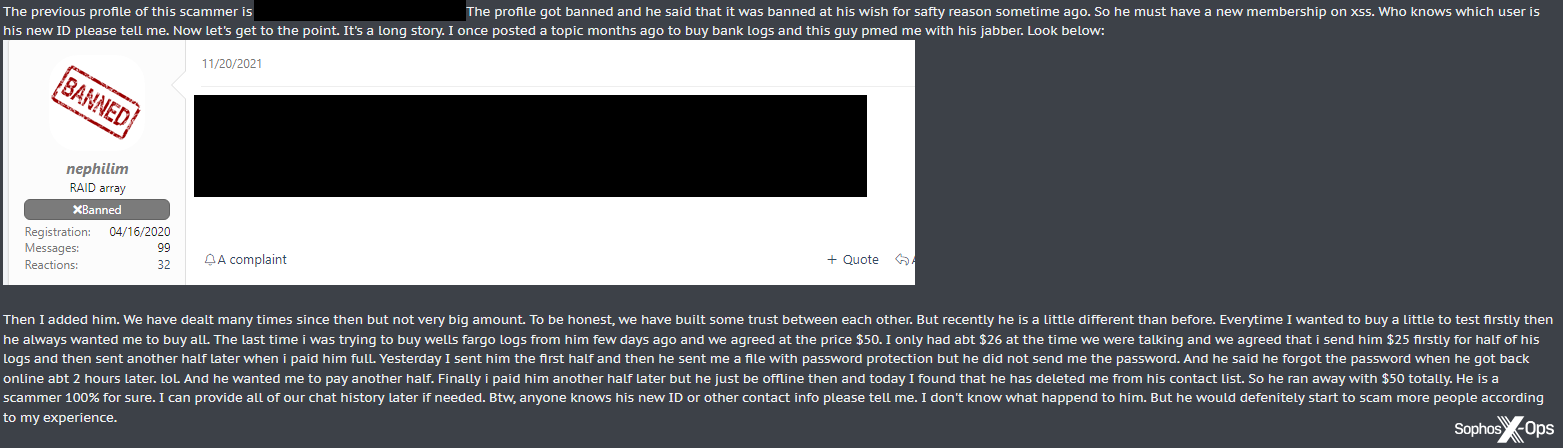
There’s not much arbitrators can do about rip-and-runs; they usually ban the scammer, but it doesn’t have much impact as the scammer is long gone. From the scammer’s perspective, they lose their profile (and any associated reputation points), so they’ll have to start from scratch if they want to run the scam again.
Figure 3: An example of a scammer apparently creating a new profile to commit further rip-and-run scams
Fake leaks and tools
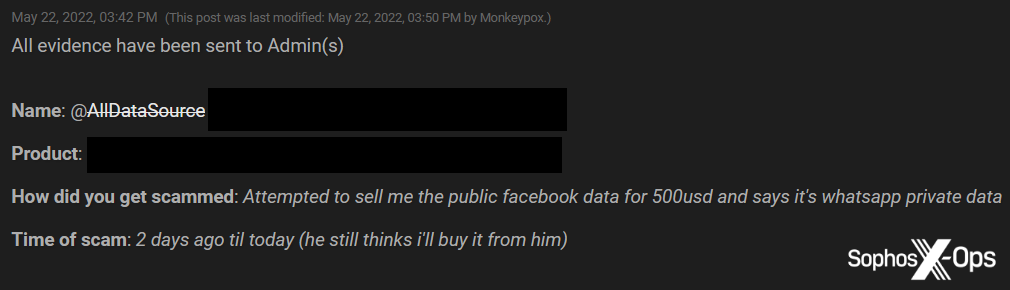
A scam that embodies the warning caveat emptor, this attack can take various forms, although it’s especially common with database trades. A scammer offers a database for sale, which is actually publicly available or previously leaked.
Figure 4: A BreachForums scam report concerning a fake database
This type of scam is prevalent on BreachForums (and was also very popular on its predecessor, RaidForums).
Figure 5: Another scam report, this one involving a publicly available database
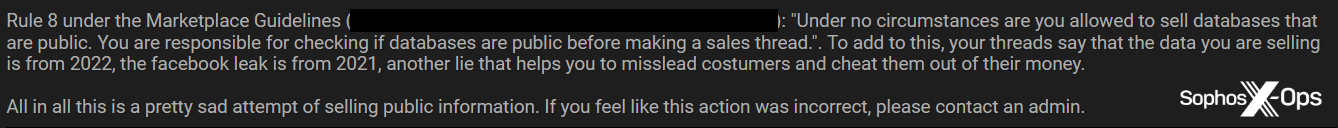
The moderator’s response to the above report finds in favor of the complainant, citing the forum’s rules, despite the accused disputing the claim:
Figure 6: The moderator’s response
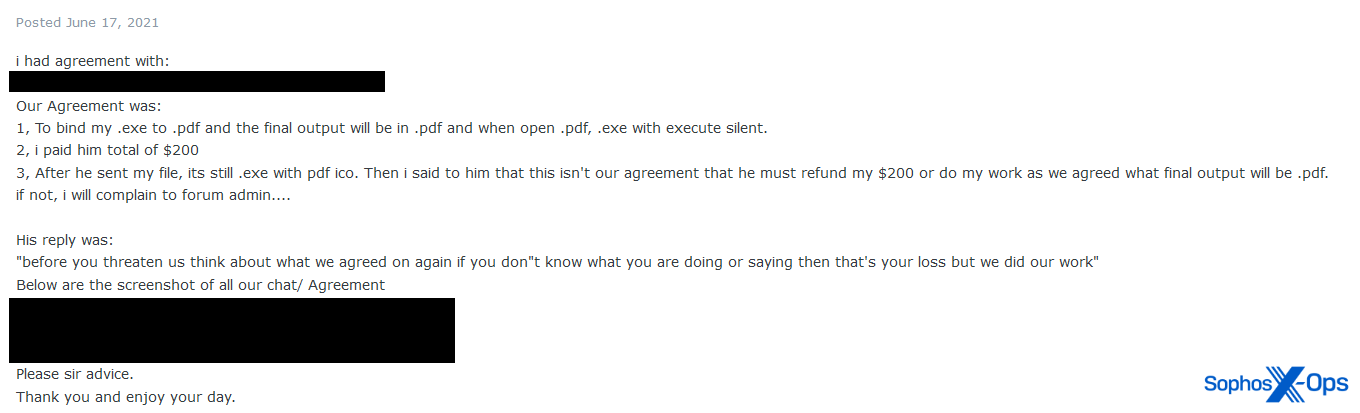
But it’s not just databases. Here’s an example from Exploit, where one user paid $200 USD to another user to bind an executable (presumably malware) to a PDF. The buyer raised a scam report because, rather than binding the executable, the user simply gave the file a PDF icon.
Figure 7: The PDF/exe scam report
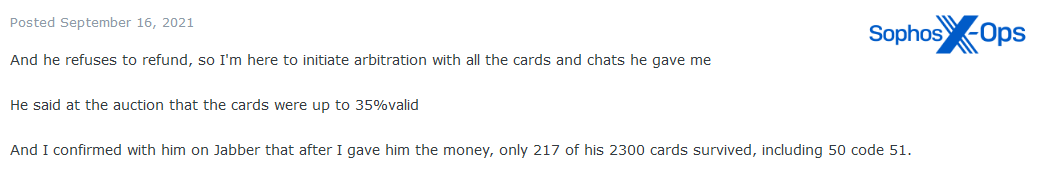
And, in another example from Exploit, stolen credit card data turned out to be invalid.
Figure 8: A scam report involving higher percentages of invalid card data than advertised. Note that the complainant in this case was subsequently banned for scamming!
We saw numerous examples of users buying services, tools, and frameworks which were not as advertised or which did not meet requirements. The accused don’t usually do a runner after pulling these scams, but instead, as one commenter pointed out in the PDF/exe thread, hope that their ‘marks’ don’t understand what they’re paying for. It’s attempted deception, rather than explicit scamming.
Referral scams
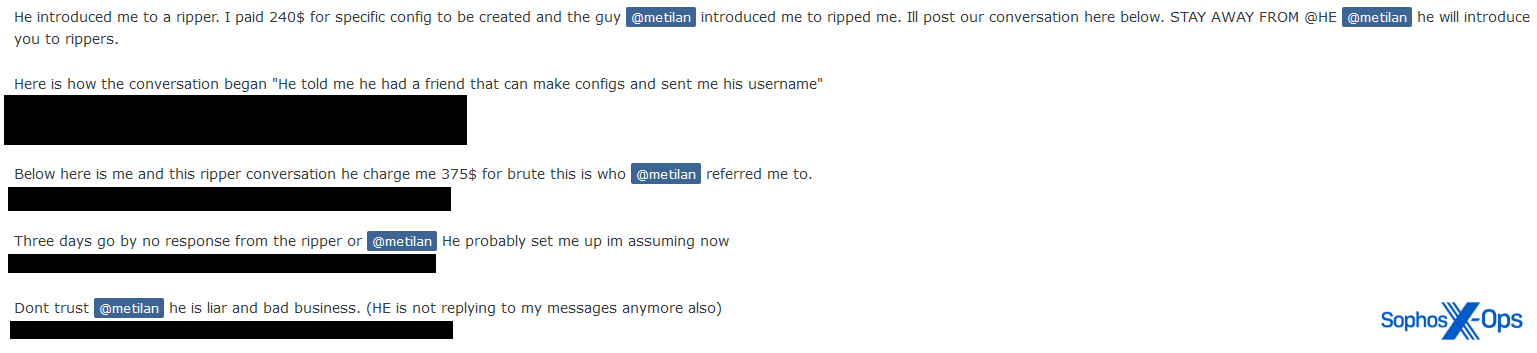
Often a variation of the first two scam types, referral scams involve two or more scammers working in tandem. The first, who may have a reasonable reputation score and feedback (possibly through ‘alt repping’), builds rapport with the victim throughout the sales process, and then introduces them to the second scammer, who they claim can complete the work in question. As shown in the example below, this usually ends with both scammers disappearing with the victim’s money.
Figure 9: A referral scam report on Exploit
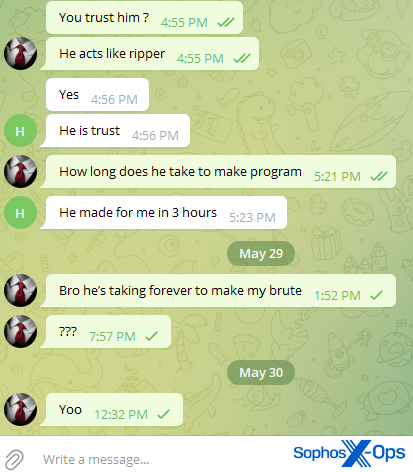
In this case, despite clear misgivings about the trustworthiness of the second scammer, the first scammer’s reassurances were enough to convince the victim to hand over money:
Figure 10: A screenshot from a private chat between the first scammer and the victim, concerning the second scammer
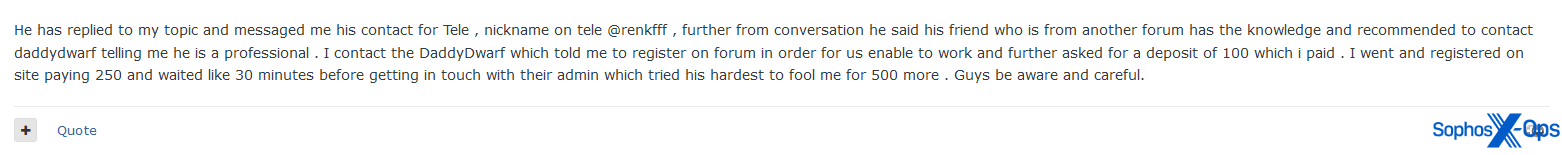
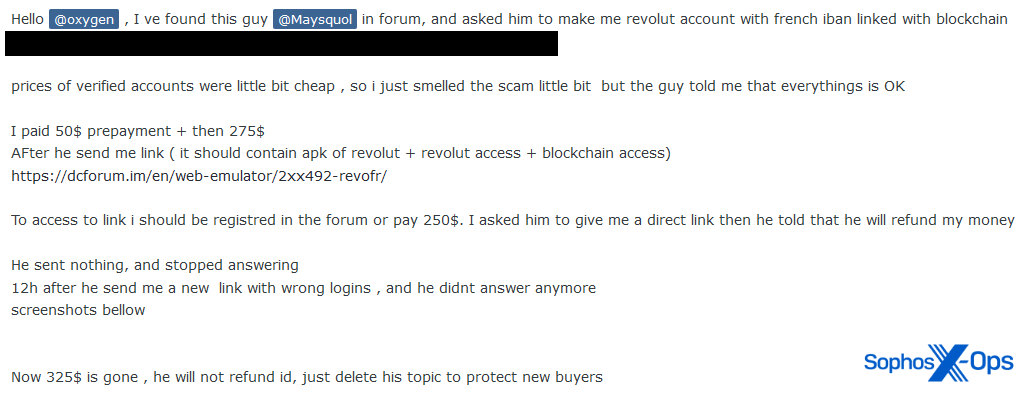
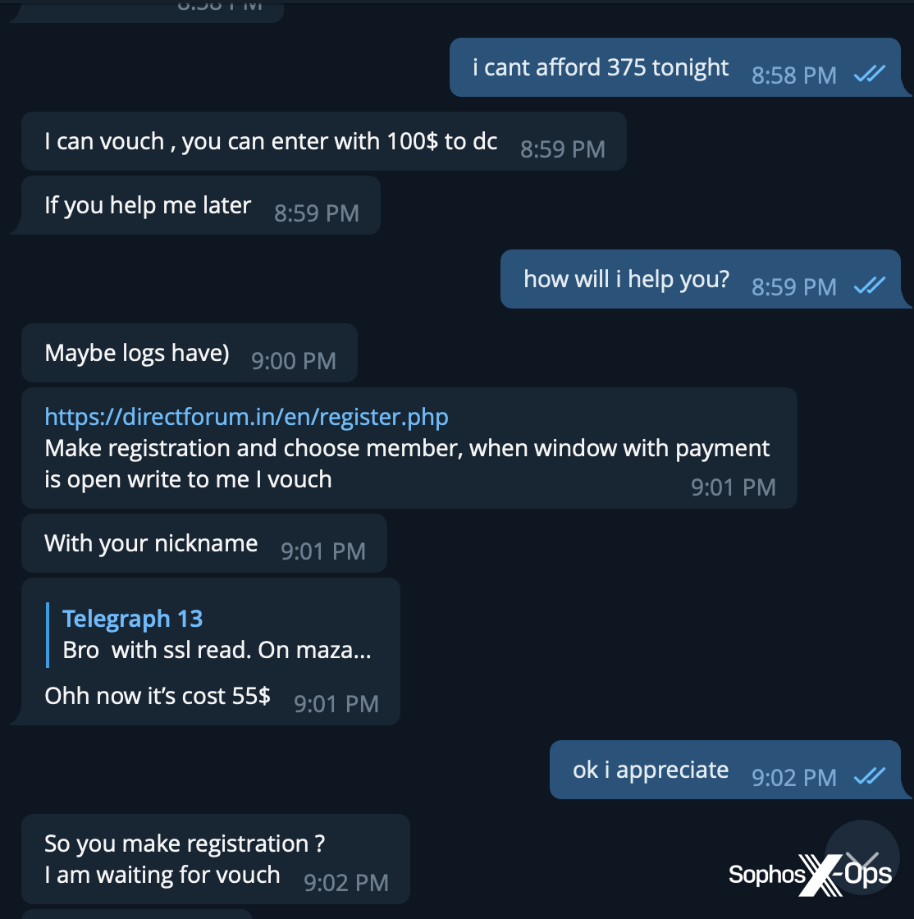
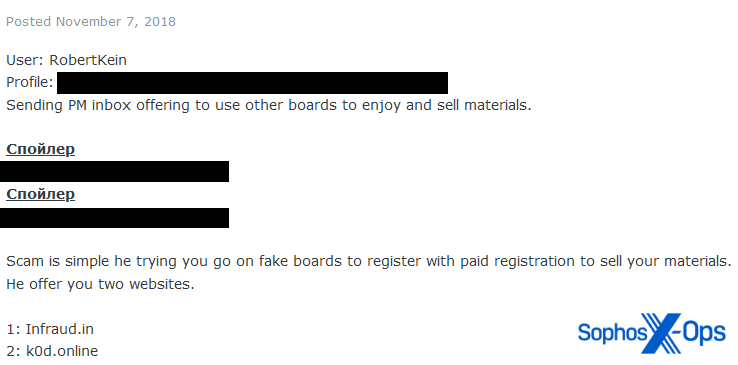
Referral scams can also involve dedicated infrastructure. In the example below, the first scammer contacted the victim and convinced them to contact a second scammer on a separate forum, which was a scam site (see Typosquatting, phishing, and ripper sites, below). To access the site, the victim had to pay a deposit and registration fee, losing $350 in total.
Figure 11: A referral scam involving a scam forum site
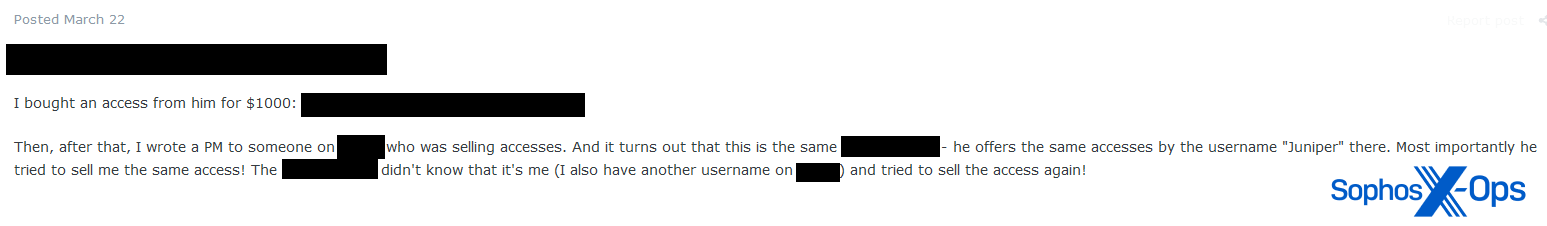
Alt repping and impersonations
‘Alt repping’ is a variation on referral scams; rather than two separate scammers, one scammer operates multiple accounts, usually to artificially inflate their reputation score (a key metric for many users when deciding who to trade with).
Figure 12: A BreachForums moderator accuses a user of alt repping
Occasionally, scammers will use multiple profiles for other purposes. In one Exploit report, for example, a user claimed that an individual was operating accounts on both Exploit and XSS under different names to sell the same product, an AaaS listing, multiple times (we briefly examined reselling in our recent white paper on multiple attackers).
Figure 13: One individual, operating accounts on different forums, attempts to sell the same AaaS listing twice
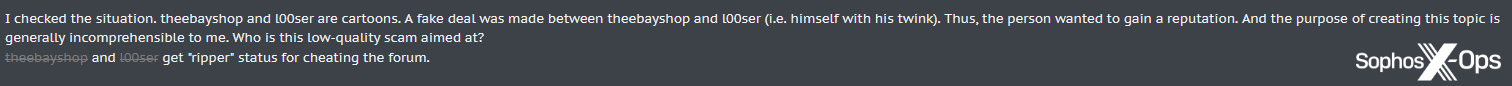
And in a stranger case, a user was banned on XSS for creating a trade between two sockpuppet accounts, and then opening an arbitration case about it (possibly because they incorrectly assumed the forum itself would compensate them):
Figure 14: Two sockpuppet profiles are banned for trying to cheat the XSS forum
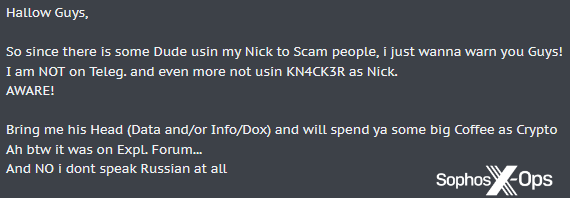
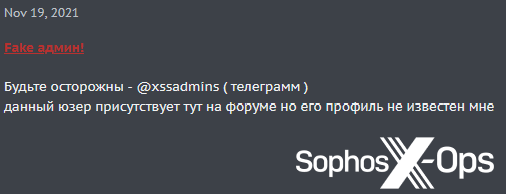
A variation on alt repping is scammers impersonating users with high reputations, or jumping in on in-progress negotiations and attempting to pass themselves off as the seller:
Figure 15: A user warns the XSS forum that someone is attempting to impersonate them
Fake guarantors
Guarantors and ‘middlemen’ are typically optional on criminal forums, but moderators and senior users often recommend them. They function as an escrow service, holding funds until they receive confirmation from the buyer that the goods have been received and are as advertised. They usually take commission for this, although the BreachForums administrator offers it as a free service.
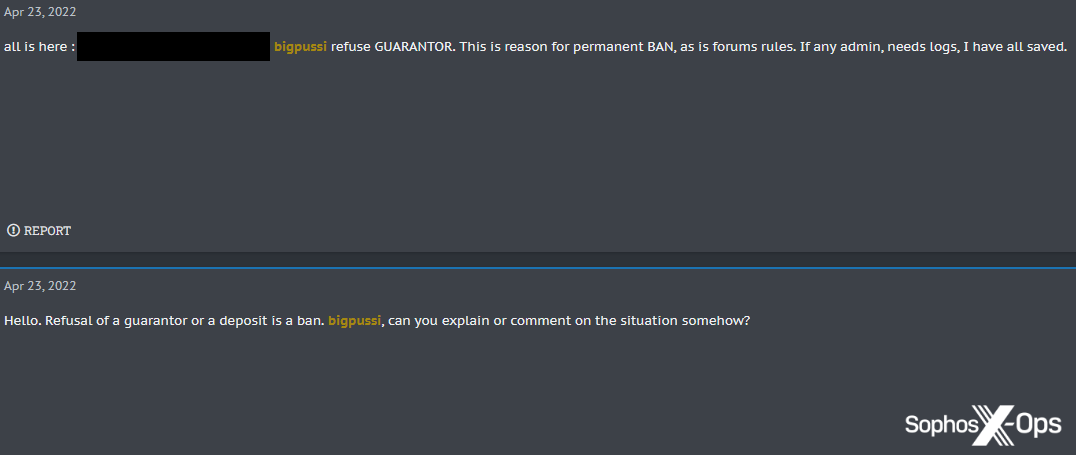
A refusal to use a guarantor if asked is a bannable offense on some forums.
Figure 16: A user is called out in an XSS scam report for refusing a guarantor
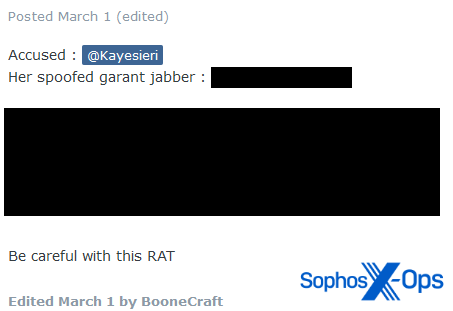
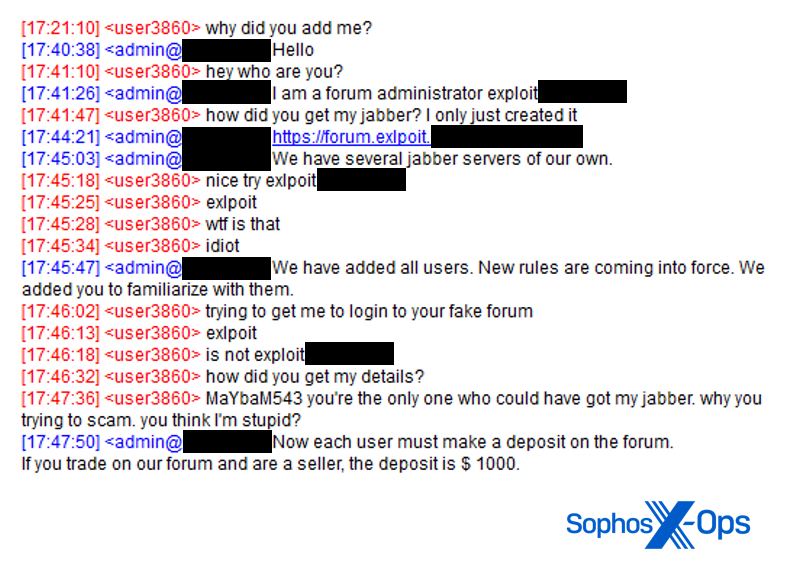
Some scammers weaponize the concept of guarantors. Typically, this involves some form of impersonation attack, where a scammer impersonates an administrator or registers a misleading Telegram or Jabber name, as in the examples below:
Figure 17: An example of a misleading Jabber name designed to impersonate the Exploit guarantor service
Figure 18: A malicious Telegram handle designed to impersonate XSS administrators
A scammer who successfully impersonates a guarantor is likely to then disappear with the buyer’s funds.
The Exploit administrators have implemented a safeguard for this – a ‘fake Jabber checker,’ where users can submit Jabber names to check if they’re legitimate.
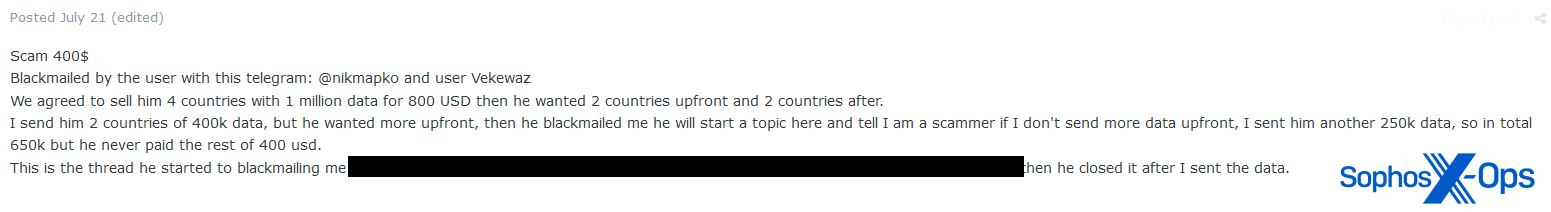
Blackmail
We noted one allegation of blackmail in the scam reports we examined, and it didn’t appear to be a particularly egregious one. The complainant, a database seller, alleged that a buyer threatened to accuse him of being a scammer if he didn’t send more data for free.
Figure 19: An Exploit scam report alleging blackmail
What this case does show is how seriously marketplace users take their reputation. An accusation of scamming can put a serious dent in a vendor’s credibility, and therefore impact their earnings.
What we didn’t see – although that’s not to say it doesn’t happen – were any outright examples of blackmail, where users dox others and threaten to expose them or report them to law enforcement (although there have been public accusations of this nature involving high-profile threat actors).
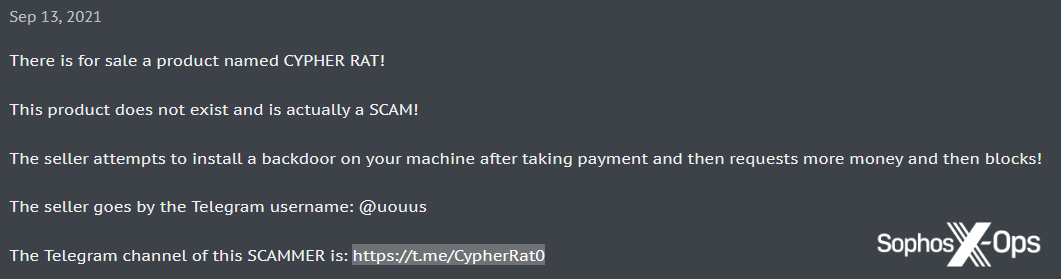
Backdoored malware
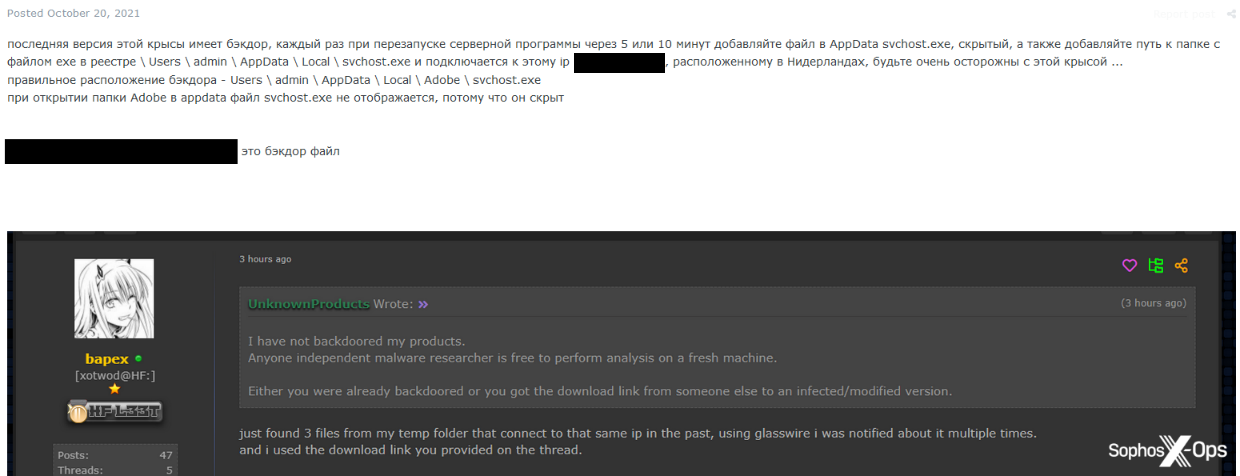
Moving on to more sophisticated attacks, we saw several scam reports about backdoored malware – that is, malware sold or distributed on the forums which contains code designed to covertly attack its operators and steal their data.
Figure 20: An XSS scam report alleging that a RAT sold by a user installs a backdoor
Figure 21: An Exploit user accuses the author of BitRAT of backdooring their malware
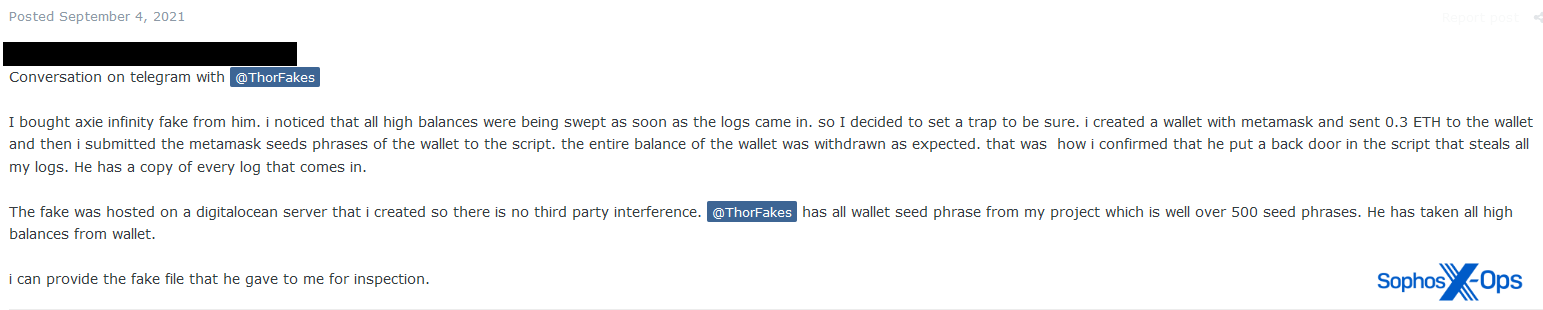
A particularly interesting example involves an Exploit user who purchased a (deliberately) fake copy of Axie Infinity – an NFT-based game – with the intent of defrauding legitimate users by distributing it and passing it off as genuine. The fake copy contained a backdoor which stole the stolen cryptocurrency.
Figure 22: A scam report about a backdoored fake copy of Axie Infinity
As with virtually every scam report we read, the irony of this situation was apparently lost on the victim.
Backdoored malware isn’t unique to criminal marketplaces. Security researcher BushidoToken reported in June 2022 that a software piracy site was serving up malware builders and panels backdoored with an infostealer. And research by security firm JFrog in February 2022 revealed that some malicious npm packages contained code designed to steal secret tokens from threat actors, who themselves steal tokens from legitimate users.
Typosquatting, phishing, and ripper sites
We noted numerous instances of typosquatting, phishing, and scam forum sites designed to either trick users out of a ‘registration fee’ or to steal credentials for genuine criminal marketplaces (with possible motivations including theft of cryptocurrency, impersonating users for future scams, or ruining users’ reputations).
In many cases, scammers adopted similar approaches to those used by traditional threat actors to target individuals and organizations, with some context-specific differences.
For example, we observed several cases where scammers had set up clones of current or former criminal marketplaces. Here’s a fake version of the Exploit site, which uses the misspelling ‘explolt’ in the domain name, but is otherwise an identical clone:
Figure 23: The fake Exploit homepage
This site is probably intended to harvest credentials, or trick users into paying false registration fees, and appears to be well-constructed, redirecting to the genuine Exploit site.
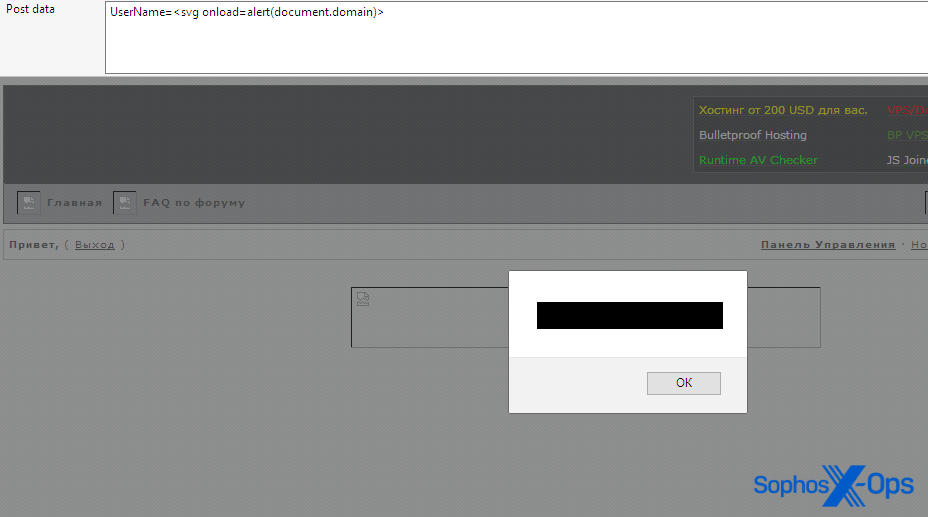
Amusingly, some Exploit users, on becoming aware of this fake site, tested its security and found an XSS vulnerability:
Figure 24: An Exploit user’s screenshot of an XSS vulnerability in the fake Exploit site
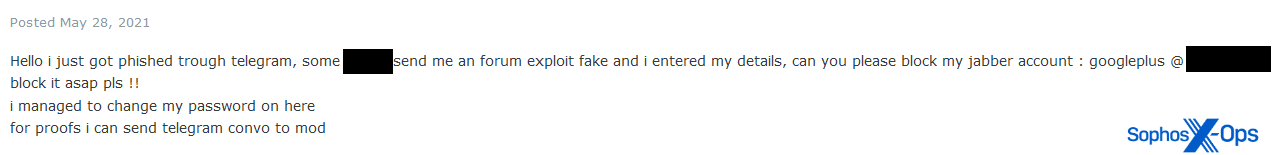
We observed another fake Exploit domain – this one misspelled as ‘exlpoit’ – used in conjunction with a Jabber phishing attack. Judging by the conversation, this scam was designed to dupe users into paying a deposit fee, although the target didn’t fall for it on this occasion.
Figure 25: An excerpt of the Jabber conversation between scammer and target
Other users aren’t so canny:
Figure 26: A user was fooled by a fake Exploit forum and entered their credentials
We saw a few other typosquatting examples, like ‘explolit’ and ‘exploti’, used with varying degrees of success. Some users spotted the scam, others fell for it.
XSS isn’t immune either. We observed an XSS clone (spelled as ‘xsss’) which was previously reported by journalist Lawrence Abrams. Upon entering credentials, the clone redirects to hxxps://fe-avv18[.]ru/send.php, which presumably processes and stores the harvested credentials.
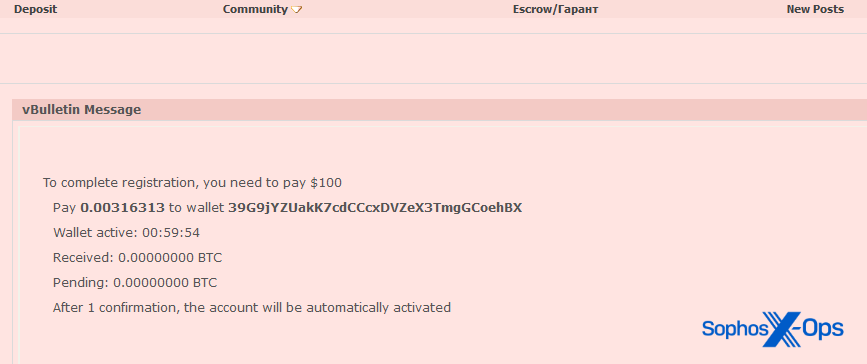
We also noted a website, named ‘xsx’, which doesn’t look anything like the genuine XSS site but may be designed to fool inexperienced users. This site demands a $100 registration fee (a very common scam amount, as we’ll see in Part 3 of this series), and is reported on the XSS forum as a ripper site.
Figure 27: The ‘xsx’ scam site
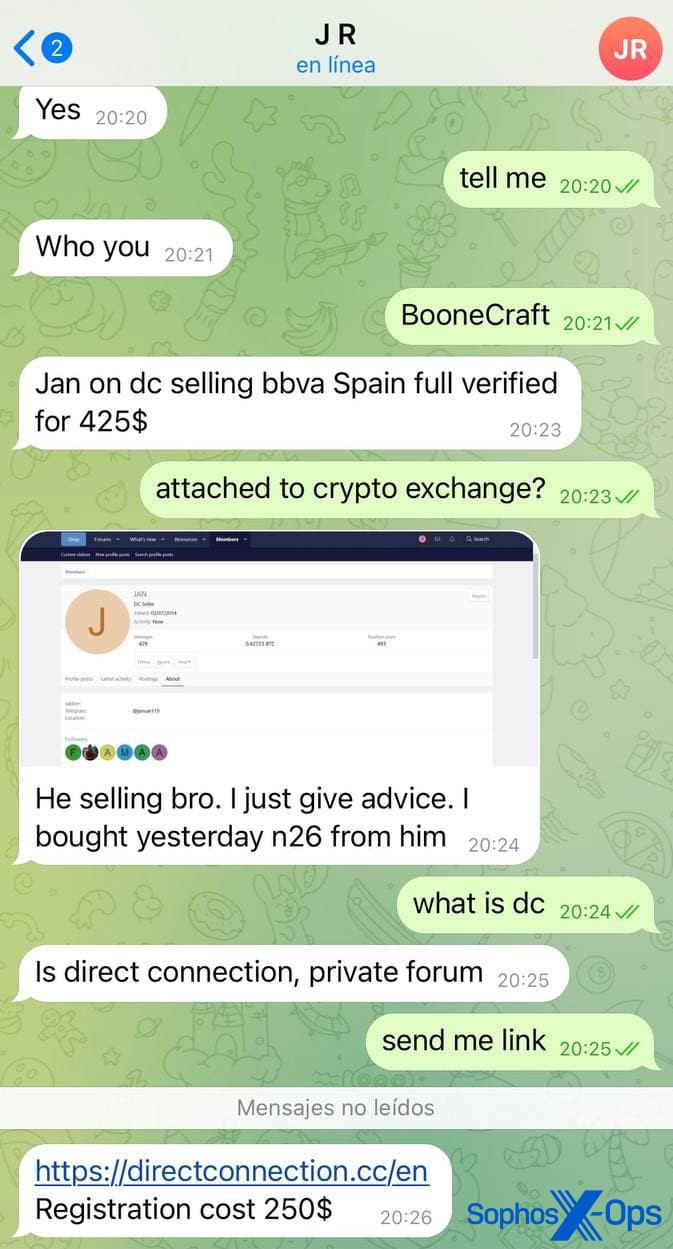
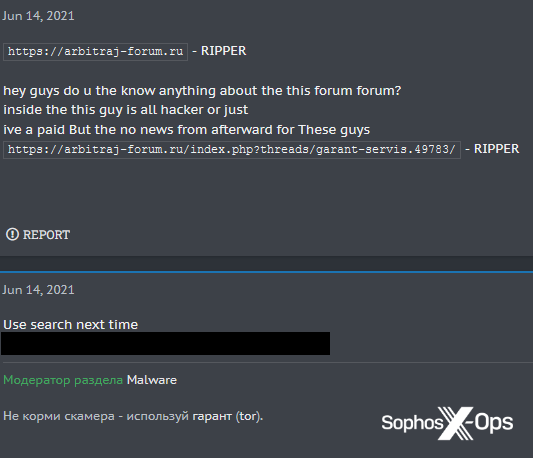
More commonly, we saw scams using domains similar to now-defunct criminal marketplaces, particularly Mazafaka (compromised in March 2021) and Direct Connection.
Figure 28: A user falls for a scam which plays on the name of a defunct criminal marketplace
Figure 29: A user falls for another Direct Connection scam
Figure 30: Yet another Direct Connection scam
Other examples include typosquatting domains relating to the prominent criminal forum Verified, with misspellings such as ‘verifeid.’
Sometimes, scammers create sites which don’t imitate known marketplaces but use the same methodology, i.e., charging a registration fee:
Figure 31: Two alleged scam sites reported by an Exploit user
Figure 32: A scam site reported by an XSS user
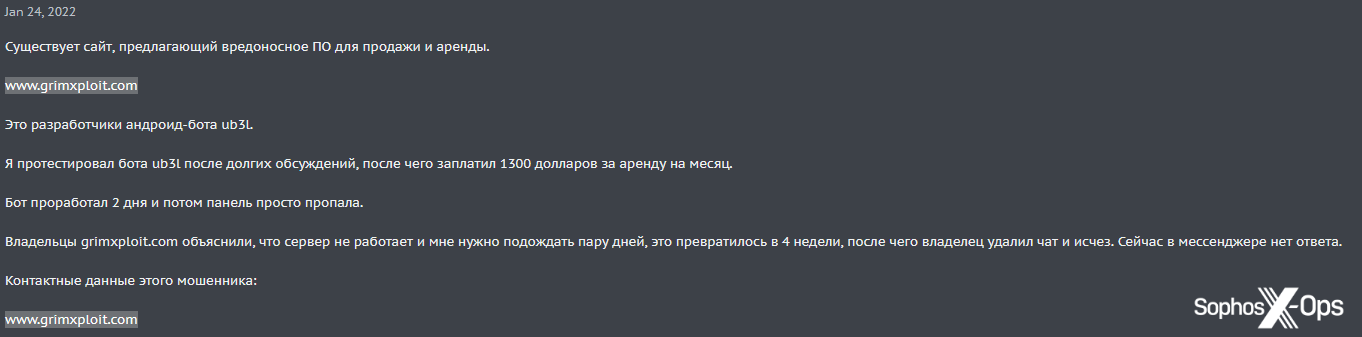
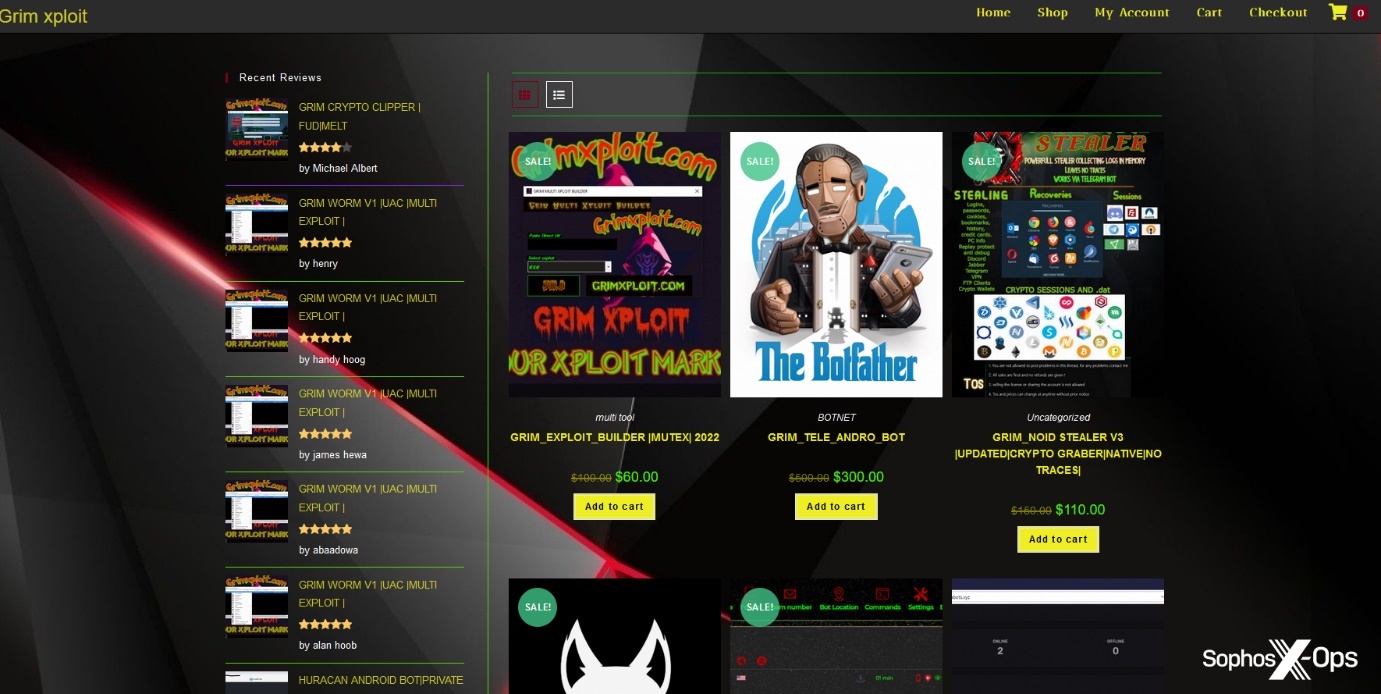
Most of these scams involve fake registration fees, although we saw some variations of other scams, like rip-and-runs and fake tools, connected to scam sites. For instance, one XSS user rented malware from a site, which worked for two days before the C2 panel disappeared (followed shortly by the site’s owner):
Figure 33: A user reports being scammed by a malware rental site
Figure 34: The malware rental site in question
Scammers scamming the scammers who scammed them
Unsurprisingly, while scamming threat actors might be lucrative, it can also be a dangerous game. We observed a few instances where threat actors weren’t just indignant about being scammed – they wanted to get even.
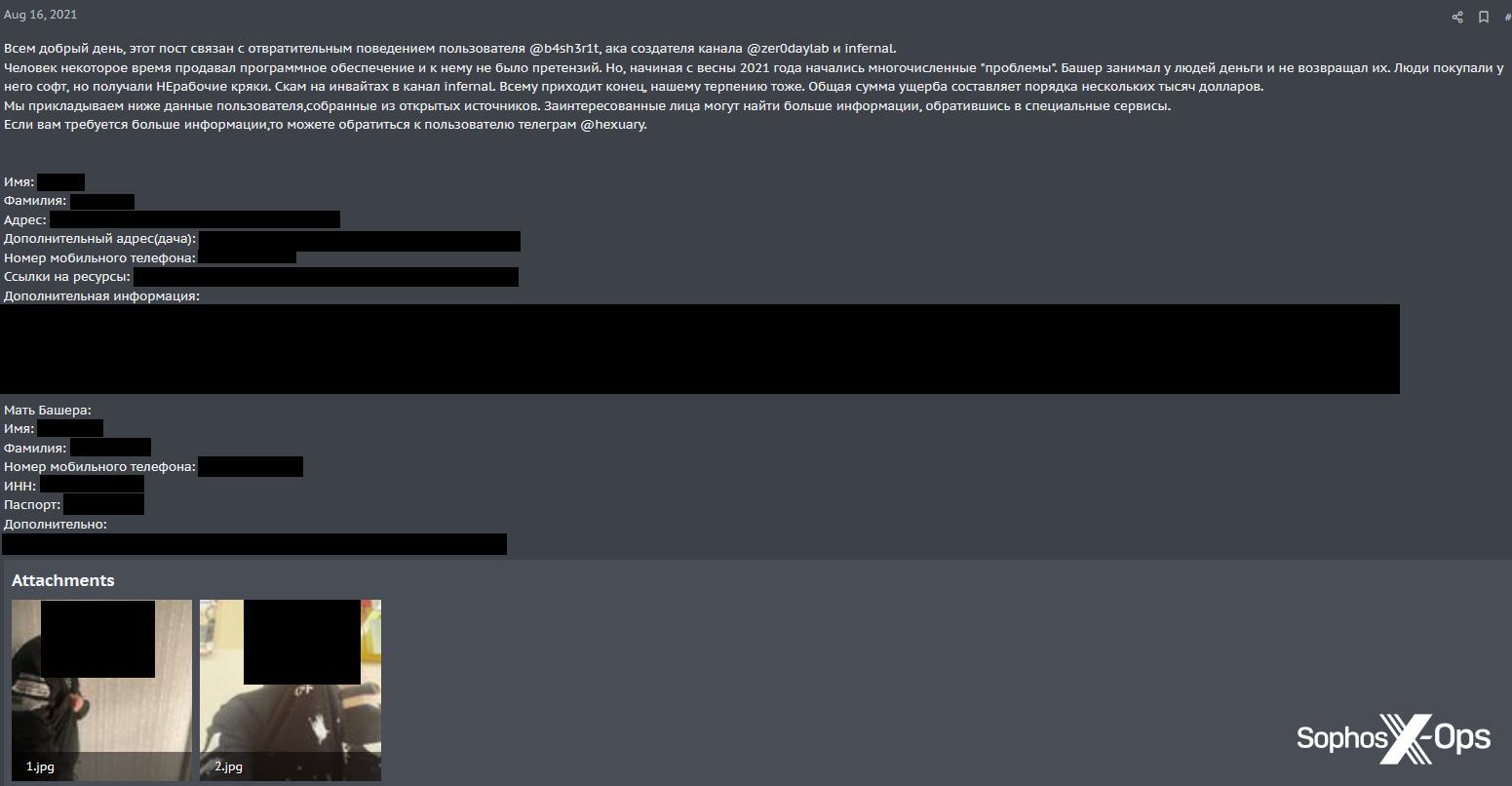
An XSS user annoyed at an alleged scammer for selling non-working tools and sending scam invites, doxed them – revealing their name, address, mobile phone number, and social media profiles, and their mother’s name, phone number, and passport number. The accuser threw in a couple of photographs for good measure.
Figure 35: An alleged scammer is doxxed on XSS
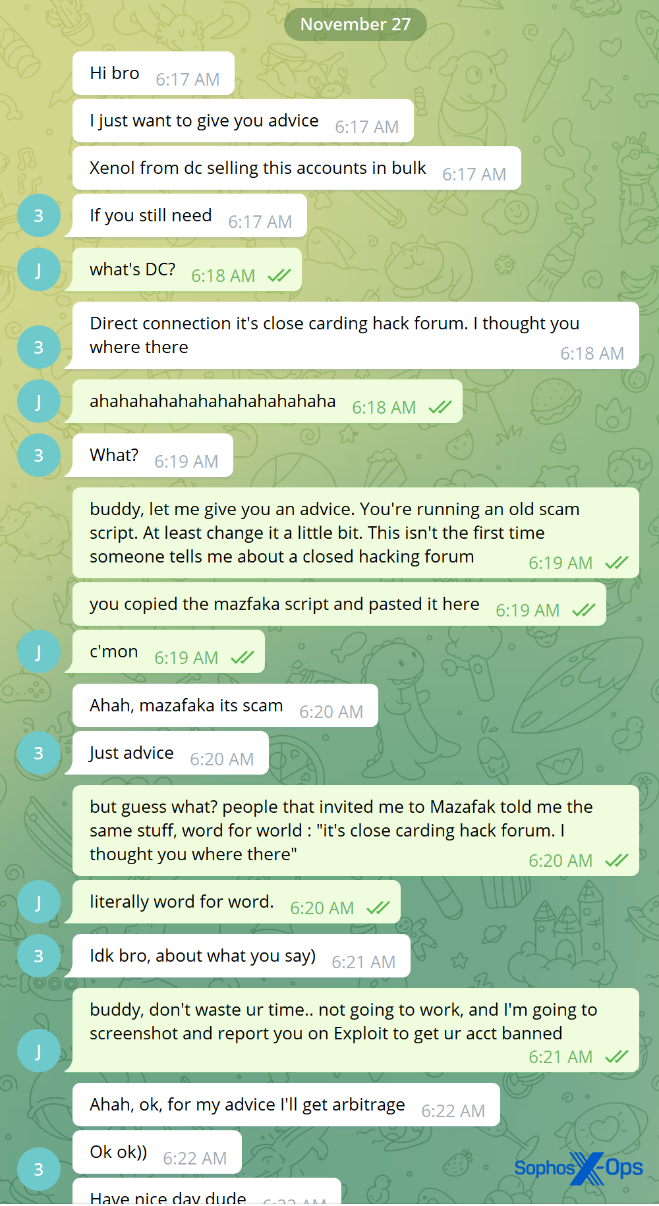
Over on Exploit, a scammer who phished new users with a fake Direct Connection marketplace link (see Typosquatting, phishing, and ripper sites) got short shrift from a user who recognized the scam:
Figure 36: A user recognizes the Direct Connection/Mazafaka scam and challenges the scammer
The user then posted the scammer’s information on Exploit, and invited other users to harass them:
Figure 37: The Exploit user invites others to harass the scammer on Telegram
The most interesting examples of scammers who scammed scammers getting scammed come from BreachForums.
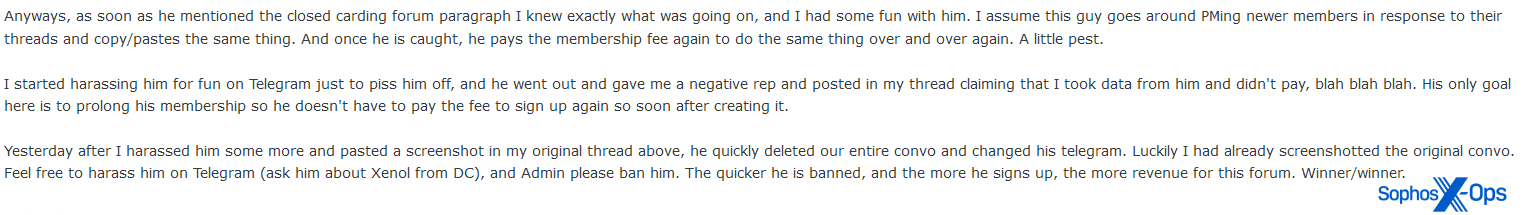
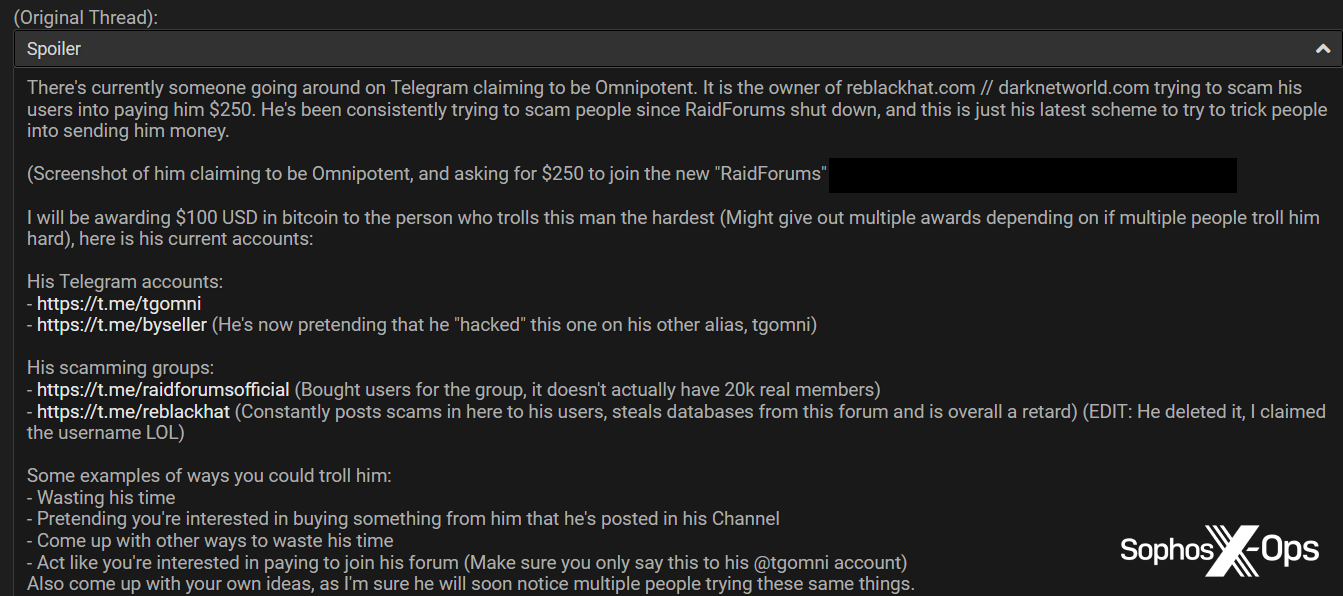
Following the news that a scammer was pretending to be Omnipotent (one of the founders and administrators of RaidForums) to trick users into paying $250 to join the ‘new RaidForums,’ the BreachForums administrator started a contest: $100 to whoever “trolls this man the hardest.”
Figure 38: The BreachForums administrator announces a contest to troll a scammer
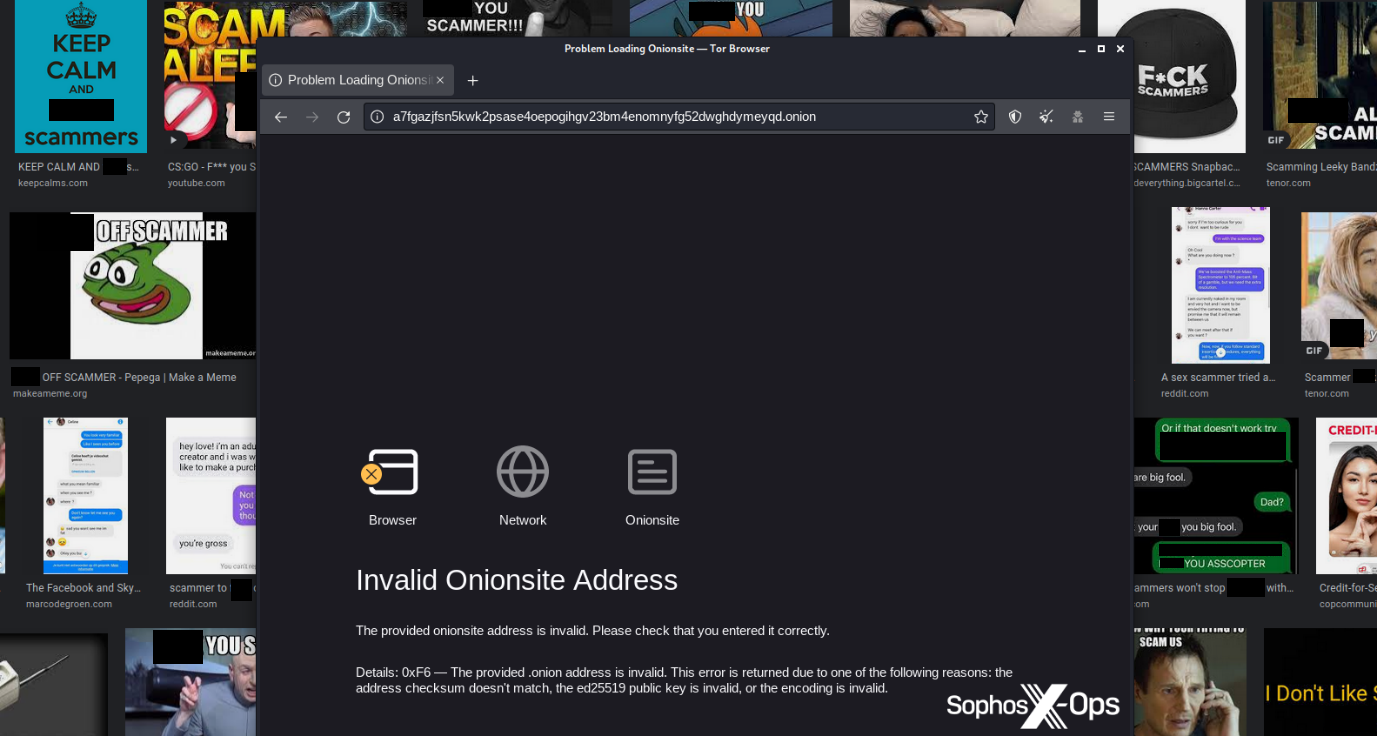
Figure 39: One of the entries to the trolling contest. A BreachForums user sent this screenshot to the scammer, saying they couldn’t access the fake RaidForums site
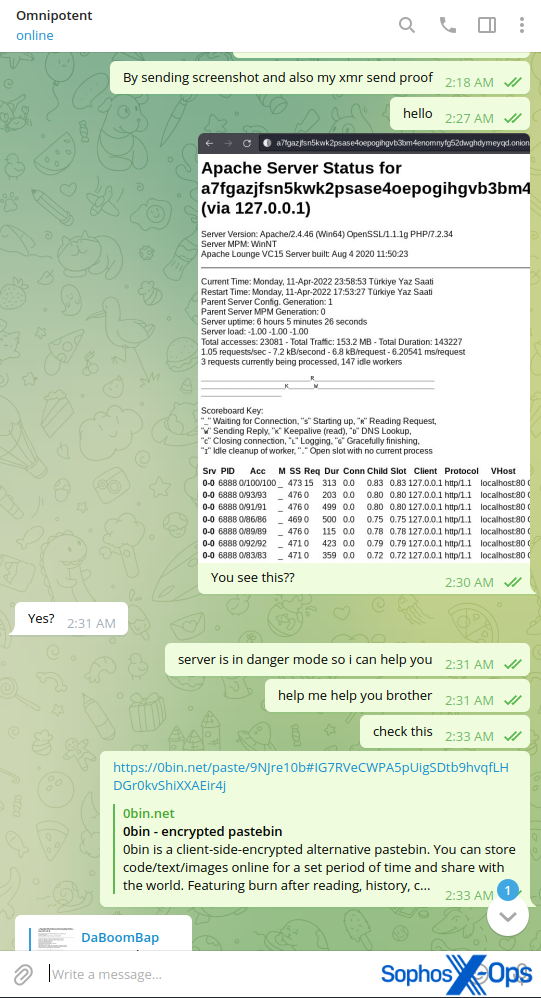
The eventual winner convinced the scammer that their website was leaking sensitive information, by showing them a screenshot of the Apache Server Status page. The scammer ended up taking the site down because they thought it had been compromised.
Figure 40: Part of a long trolling thread targeting a BreachForums scammer
According to recent posts, the same scammer is back at it again, and the BreachForums administrator has started another trolling contest – this time with a $300 prize.
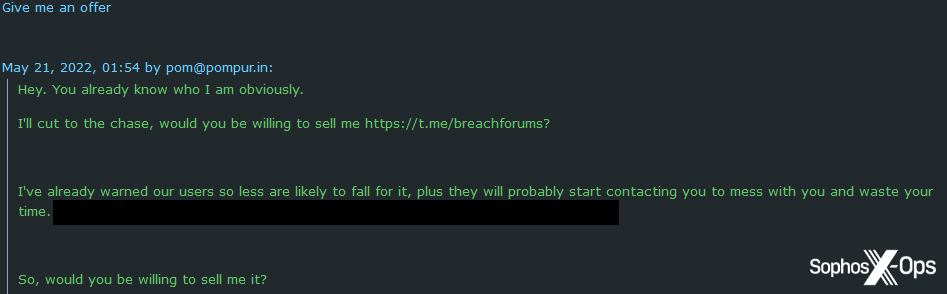
Finally, the BreachForums administrator scammed a scammer personally. An individual registered a Telegram username very similar to BreachForums, and was offering public databases for sale.
The admin offered to buy the username from the scammer.
Figure 41: The BreachForums administrator contacts a scammer and asks them to sell their Telegram handle
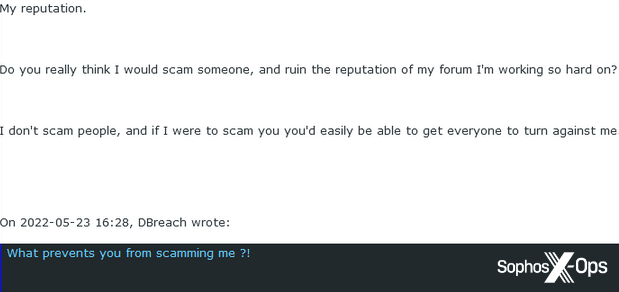
After some back and forth, they agreed on a price of $10,000, and the admin asked the scammer to transfer the group to his account. The scammer was concerned about being scammed, but the admin reassured them, citing their reputation:
Figure 42: The administrator reassures the scammer that they won’t get scammed
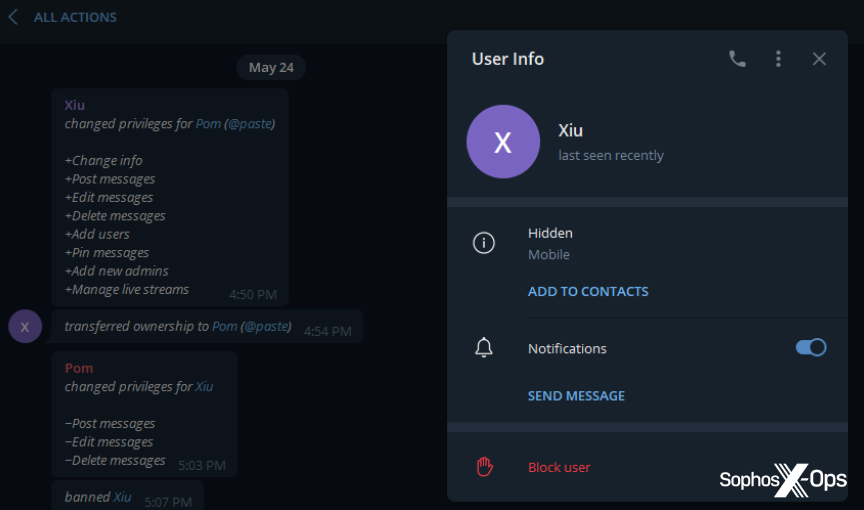
Once the scammer transferred ownership, the admin removed the scammer’s permissions and banned him. Without paying, naturally – making this a rip-and-run scam against a scammer.
Figure 43: The BreachForums administrator bans the scammer
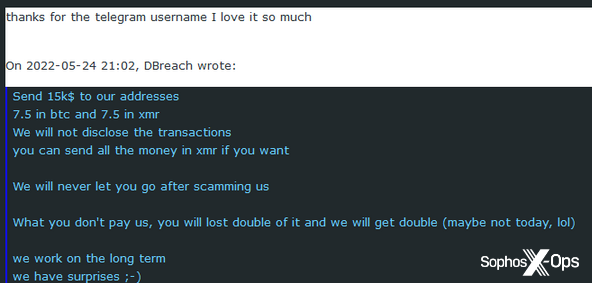
The scammer was not thrilled.
Figure 44: The scammer threatens the BreachForums admin
According to the admin, the scammer later attempted to DDoS BreachForums, but there have been no other repercussions since.
In the third part of our series, due out the same time next week (Wednesday 21 December), we’ll look at a specific, curious large-scale typosquatting scam, which involved a coordinated network of twenty fake marketplaces.