Detection Tools and Human Analysis Lead to a Security Non-Event
Credit to Author: Angela Gunn| Date: Wed, 30 Nov 2022 12:00:13 +0000
A recent Sophos X-Ops case provides an example of how Managed Detection and Response (MDR) is more effective when tools talk to one another… and a team of analysts is listening in.
The customer in this example is a large private telecommunications company. Our customer has an assortment of security systems from Sophos and other vendors in place, and now, with Sophos MDR, a way to tie them all together. MDR watches for alert data not just from Sophos’ security products but also other vendors’ security products as well. As we see later, MDR analysts can take that data from multiple vendors’ sources and use it to analyze what’s happening in the customer’s environment.
In this mid-October attack, the adversary spoofed a large European financial-services company. After obtaining several dozen email addresses for certain departments, the attackers sent our customer hundreds of Spearphishing Links (SL) messages – official-sounding attempts at getting recipients to click a link and, on a maliciously crafted web page, to type in their credentials or download a file. (SL is a popular variation on spearphishing; MITRE ATT&CK lists it as Technique T1566.002.)
In this case, the emails (two versions, same phish) claimed that the recipient was required to authenticate their identity on the site to which the email claimed to link – and that since they’d already failed to do so earlier, their security was disabled until they clicked the link in the email. The customer’s email appliance flagged both versions of the suspicious emails and modified the malicious links to protect users, then delivered 118 of the modified emails to users – two of whom clicked the link.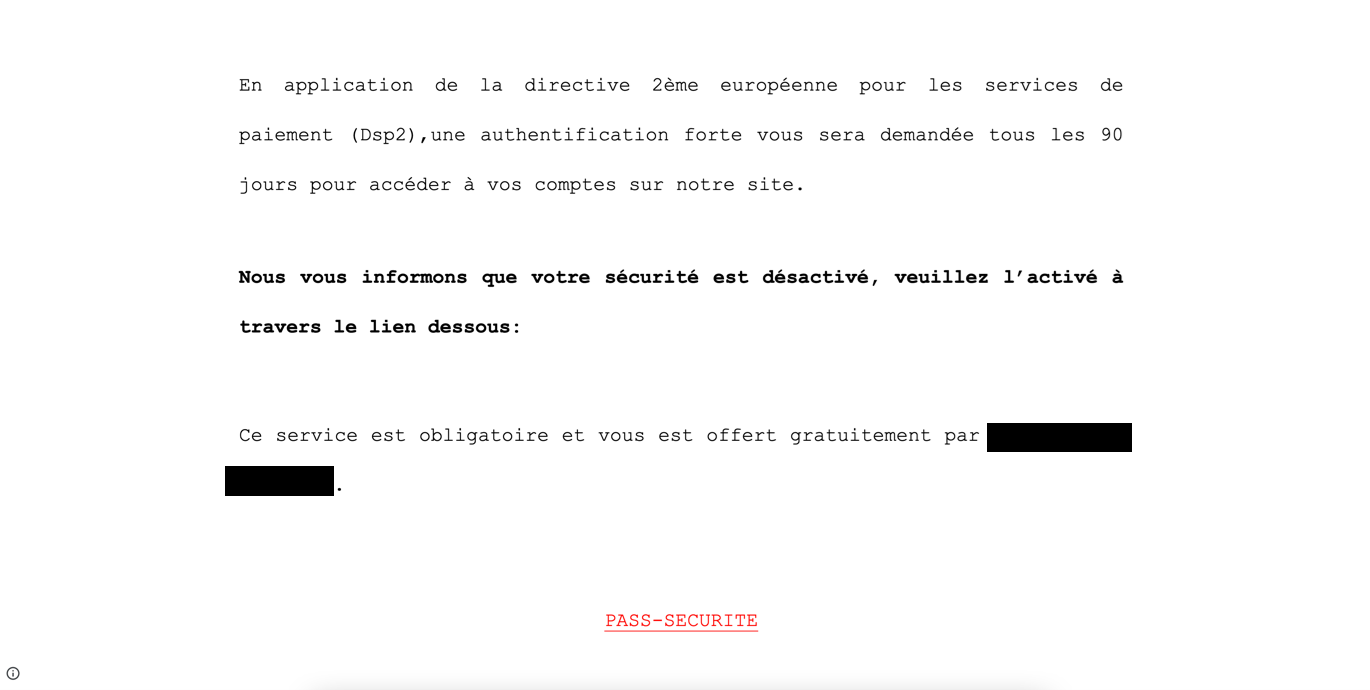

Figure 1: The phishing attempt, with an official look and tone
A Google Translate English version of the lure reads:
In application of the 2nd European directive for payment services (Dsp2), strong authentication will be required of you every 90 days to access your accounts on our site.
We inform you that your security is disabled, please enable it through the link below:
This service is mandatory and is offered to you free of charge by [REDACTED].
PASS-SECURITY
**You risk a temporary ban on all your debit transactions by ignoring this notice**
*If you are an administrator: Get the code on your portal
Sogecash.net
Best regards,
Sophos’ MDR platform examined the flag from the appliance, which showed that 69 of the customer’s email addresses received at least one instance of suspicious mail, with 234 alerts firing in total. MDR’s automated processes evaluated the alerts, noted strong similarities, and clustered all 234 into two clustered events for deeper analysis.
At this point, humans stepped in. Looking at the information communicated from the third-party appliance to the MDR platform, Sophos’ analyst made note of various parameters including the subject header, time sent, purported sender, and the URL to which the emails pointed. The analyst also made note of the sender’s actual IP address and two smallish files attached to the email, text.html and text.txt.
With this information, our analyst was able to draw in further intelligence from multiple sources. Our first stop was a VirusTotal check on the IP address to which the email was directing recipients, an address we (and other security vendors) identify as malicious. Inside Sophos’ own XDR, the analyst dug into the two attached files, checking the customer’s network journals for traffic to the malicious URL and trawling the data lake to see if any process associated with the attack was successfully executed.
The news was good: Our investigation confirmed that no malicious process had slipped through the firewall or lingered to trouble the network later, even though two users were confirmed to have clicked the (neutered) link. A quick alert to the customer laid out the initial flag and the ensuing deeper investigation and recommended that the customer delete the malicious emails still sitting in user inboxes.
In the end, nothing bad happened — thanks to the combination of detection tools and human analysis as part of ongoing managed detection and response. Not only did this combination of defense capabilities prevent something bad from happening, it also enabled us and this customer to learn from the non-event, in order to better protect this customer and other customers – a view from sentries with an unprecedented view of the action.