What is a cyber immune system? | Kaspersky official blog
Credit to Author: Alexander Vinyavsky| Date: Wed, 23 Nov 2022 00:34:50 +0000
A new approach to protecting information systems is currently gaining popularity in the cybersecurity world: cyber immunity. Systems based on this approach need no antivirus since they’re so well-protected that any hacking attempt would be too hard and prohibitively expensive to successfully carry out.
Sounds too good to be true? Believe it or not, it’s already becoming a reality. Let’s explain in simple terms how exactly cyber immunity works in practice.
We’ll start with the concept of a trusted computing base (TCB), which every information system must have. This is code that developers have no choice but to trust since it’s used to implement security-critical components of the system. Since this code is so vital, to safeguard a system we must first ensure the security of its TCB. How? We suggest using the three following principles:
- Minimizing the TCB
- Isolating components from each other
- Maintaining strict control over all interactions of those components
Let’s look at these three principles in more detail.
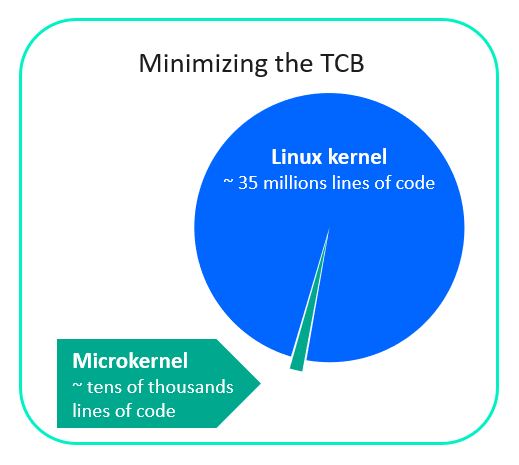
1. Minimize the TCB
The TCB should contain as few lines of code as possible. After all, the less code – the smaller the attack surface and the fewer vulnerabilities in it. For this reason, a cyber immune operating system needs a microkernel architecture.
The most popular modern operating systems such as Windows and Linux were originally built with functionality and ease-of-development in mind, meaning they use a monolithic kernel, which is a major disadvantage. That’s because such kernels contain all sorts of stuff – from interrupt control code to drivers. The result is millions of lines of code, with their number only growing from version to version.
A microkernel, on the other hand, is limited to the mechanisms critical for operation, amounting to no more than a few tens of thousands of lines of code. Everything else (drivers, file systems, etc.) runs as services in user mode.
According to a relevant study:
- 96% of critical vulnerabilities in traditional operating systems would not be critical in a microkernel OS.
- Up to 40% of critical vulnerabilities would not be possible at all.
- 57% of all vulnerabilities would be low severity.
Thus, microkernel implementation renders entire classes of cyberattacks obsolete by default.
2. Isolate components from each other
A cyber immune system is heterogeneous. It’s divided into specific security domains according to the code’s level of trust, with all components isolated from each other by means of these domains. If any system component is hacked, the intruder won’t be able to access neighboring ones and expand the attack through them. This makes it possible to use third-party components (for example, open-source code) without compromising the security of the system.
Isolation significantly reduces both the cyber-risks involved and the labor costs required to create a secure system due to use of third-party code.
3. Control all interactions
All interactions among system components are carefully controlled by a special module: the security monitor. The security monitor checks every interaction between components for compliance with the security policies. If an interaction is valid – it’s allowed; if not – it’s blocked. The potential attacker’s capabilities are significantly reduced as a result.
The security monitor concept is based on the widely-used FLASK architecture, which entails the separation of Policy Decision Points and Policy Enforcement Points.
Using a security monitor eliminates the risk of entire classes of cyberattacks by ruling out any interactions that are not explicitly stated in the security policies.
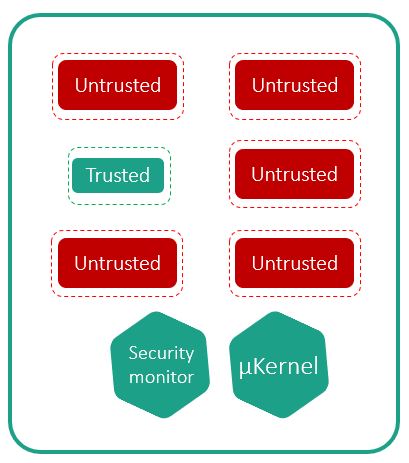
Putting all three principles together, we get the following scheme:
All entities are isolated, and they communicate with each other only through the microkernel – with such communication always checked for compliance with the security policies.
It is these three principles that form the basis of our operating system – KasperskyOS. KasperskyOS is built upon its own microkernel (not Linux) with around 100,000 lines of code, and employs the MILS and FLASK architectural approaches to provide isolation and control of interactions. This makes KasperskyOS the perfect tool for creating cyber immune products.
Cyber immunity is no longer a sci-fi concept. The concept already underpins various products, such as cyber immune IoT gateways and cyber immune thin clients. And the list is only set to grow. Thus, the rapidly approaching future will become overall more secure. In the words of ARC Advisory Group: “Cyber Immunity can be the new foundation for how digital transformation can be implemented more securely.”