How to glean passwords using thermal imaging | Kaspersky official blog
Credit to Author: Enoch Root| Date: Wed, 09 Nov 2022 01:35:39 +0000
In at least two of our previous posts, we touched upon the topic of side-channel attacks. These are attacks in which a certain confidential information (a password, encryption key, or just data that needs securing) is extracted in a certain non-trivial way. For example, instead of directly cracking an encryption system, an attacker can reconstruct the key based on ever so slight changes in the power consumption of the device. Instead of secret data being extracted from the processor cache, it can be restored based on indirect signs: a complex chain of unsuccessful attempts to access the data runs a fraction slower or faster, suggesting the presence of a zero or one in the section of data of interest.
That’s a complex example of a side-channel attack. But there are simpler variants, which we’ll talk about today…
What’s the simplest “attack” there can be on a computer system? Shoulder surfing: when thieves steal your password by looking over your shoulder. They then enter the password and gain access to your data, without hacking any computer or software. And there’s an equally simple defense against shoulder surfing: just cover the keys with your hand, or make sure there’s no one behind you when you log in. But what if an attacker could steal your password after you’ve typed it, by reading thermal fingerprints on the keyboard?
Thermal imaging and ATMs
Thermal imaging attacks (aka thermal attacks) have been on researchers’ radars for more than 15 years. One of the earliest studies in this area explores the most common real-life scenario: attacks on ATMs. It works like this. Let’s take a standard ATM keypad:

A typical ATM keypad. Source.
You go to an ATM, insert your card, enter your PIN, take your cash, and walk off. But unbeknown to you, an attacker sidles up to the same ATM a few moments later, and takes a picture of the keypad using a thermal imager, or thermovisor:

ATM keypad captured by a thermovisor. Source.
If the image is taken within 30 seconds after the PIN is entered, there’s a 50% chance of recovering the sequence. The thermovisor creates an infrared image in which bright and dark areas represent high and low temperatures, respectively. The original purpose of a thermovisor is for checking a building’s walls or windows to determine where pesky drafts are coming from. And now it seems it can be harnessed to steal PINs — although it’s worth remembering that we’re talking about research here, and not (yet) about real-life attacks.
Early thermovisors used to cost tens of thousands of dollars, while for some time now they’re generally priced at a few hundred dollars. And today they can vary in their level of sensitivity (ability to distinguish between small temperature differences). For example, The photo above (taken with an expensive professional device) shows not only which buttons were pressed, but in which order: the warmer the button, the later it was pressed.
Using a thermovisor on an ATM keypad isn’t all that simple. The image needs to be taken as soon as possible. The example above was done almost immediately after the PIN was entered. The maximum delay between input and imaging is around 90 seconds. And even then there’s no guarantee of success. For example, the potential victim could be wearing gloves, so the buttons won’t heat up at all. Or one – or two – of the PIN digits might be repeated, which would complicate the process. By the way, what PIN was entered in the above image, do you think? Test your own powers of deduction! The correct answer is 1485.
The researchers carried out a full 54 experiments, slightly varying the parameters of each. Thermal fingerprints were analyzed both manually and with automated systems (the latter were slightly better). In about half of cases it was possible to find out the buttons pressed, but not the correct sequence. The exact PIN was recovered in less than 10% of the experiments. A four-digit code out of any of all available 11 digits gives 10,000 potential combinations. If we know all the numbers, but not the sequence, there are 24 combinations to try out. But that’s still more than the number of attempts allowed: after three incorrect attempts, the bank card is often blocked. The above-mentioned 2011 study thus expanded our knowledge of thermal spying, but didn’t give us any meaningful results. But it wasn’t the last study…
Thermal imaging and smartphones
Smartphones are also susceptible to thermal attacks. This was demonstrated clearly in a 2017 study, contains this revealing image:
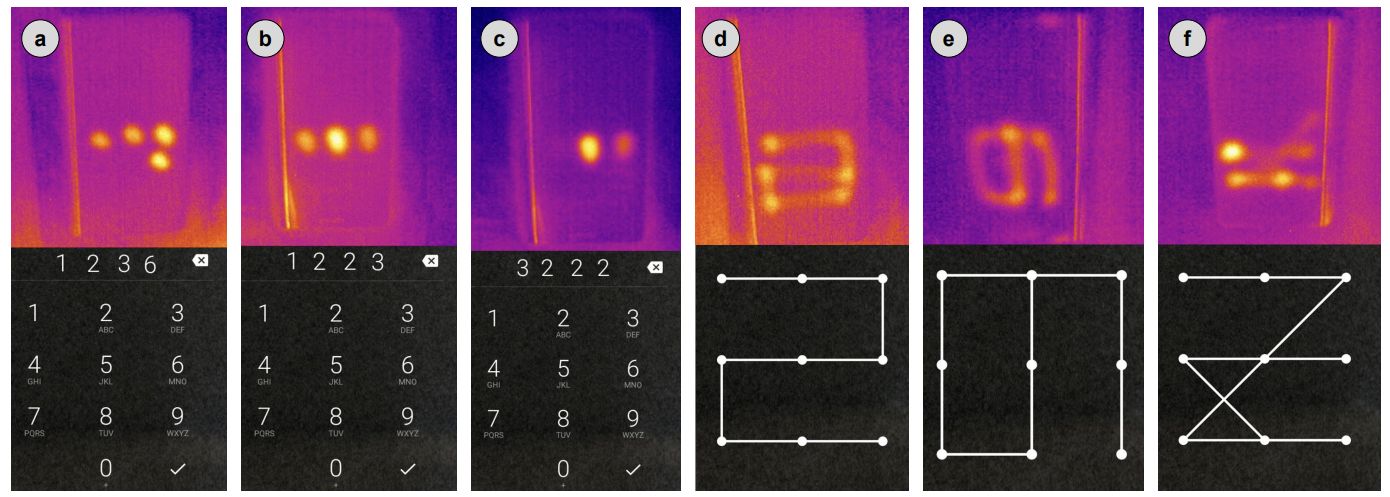
Real PINs and patterns for smartphone unlocking, and their heat traces. Source.
As before, the success of an attack depends on how quickly the thermal image is taken after input of the PIN or secret combination. Taking an image is somewhat trickier in this case, since, unlike with an ATM, folks carry their smartphones around with them. Nevertheless, it’s not so far-fetched to imagine a scenario where it might be possible to take an image at the right moment.
By 2017, data analysis technologies had improved, and the overall success rate was higher than in the ATM experiments of 2011: up to 89% of PINs were correctly garnered through timely thermal imaging. 78% of the codes were cracked when an image was taken 30 seconds after phone was unlocked, and 22% — when researchers waited 60 seconds. Incidentally, pattern locks are harder to unravel using this method. But there’s another problem with those: it was shown back in 2010 that these combinations are quite easy to guess from the finger smudges left on the screen (which stay there much longer than do thermal prints).
Thermal imaging and keypads
What do ATMs and smartphones have in common? Not many buttons! In both cases, we’re dealing with the input of short combinations of digits. To really test the possibilities of thermal spying, it’s best to try it out on real alphanumeric passwords entered on a real keyboard. And that’s exactly what a team of researchers from University of Glasgow in Scotland did. See here for the results of their work. A full-fledged keyboard through a thermovisor looks something like this:

Heat traces from pressing keys on a PC keyboard. Source.
The bright dots indicate traces of key presses. This study, like others, tested the reliability of password recovery after a certain time: the thermal snapshot was taken at intervals of 20, 30, and 60 seconds. A new variable appeared in the shape of password length, which can be arbitrary. Most importantly, the researchers applied machine-learning (ML) algorithms. In experiments that involve extracting useful data from noise, these are indispensable. ML algorithms that were trained on hundreds of images of keyboards paired with known combinations have shown excellent results in recovering passwords. Below is a table summarizing their performance:

How password recovery depends on the time between input and imaging, as well as on password length. Source.
Surprisingly, in half of cases even a long password of 16 characters was recoverable. From the examples above, you can appreciate the complexity of recovering the sequence of key presses based on tiny temperature differences. The study has one major takeaway, which you and I know already: passwords should be long and preferably generated by special password manager software.
There were also some unexpected findings. The effectiveness of the method depends on the type of plastic: some warm up less than others. And whether the keyboard is backlit is also a factor. In general, any extraneous heating of the buttons — be it from built-in LEDs or the CPU located under the keyboard in a laptop — destroys the thermal footprint. And one other point: the faster the password is entered, the less likely it is to reveal itself to thermal imaging.
How realistic are these attacks?
There’s no universal answer to this question. Is the data on your phone valuable enough for someone to follow you around with a thermal camera? Is such a scenario plausible? Fortunately, most people are not affected by such attacks — they’re simply too complicated. Thermal spying seems to pose the biggest threat to digital locks, which require a code to be entered; for example, at the entrance to an office building. The code in this case almost never changes, and the locks are often located in public places. A potential spy will have lots of time and plenty of attempts to guess the correct access code.
In other cases, the method is doable only as part of a targeted attack on particularly valuable information. The solution, as per the usual method of defeating most side-channel attacks, is to drown the sensitive data in noise. You can enter your PIN wearing thick gloves, rendering an attack impossible. You can use a backlit keyboard, and the cybercriminals will be scratching their heads. When entering your password, you can press, or simply touch, extra keys, making it almost impossible to recover the correct sequence.
2022 saw the release of a meta-analysis of thermal attack studies, whose aim was to try to assess how realistic a threat thermal imaging attacks are. The authors reported that such attacks are both implementable and affordable — and need to be factored in when building a threat model. We’re not convinced that the problem will become serious any time soon. But the meta-analysis does draw one important conclusion: a password can only be stolen if it is actually entered!
So, in a roundabout way, we’ve arrived at the topic of password death. The threat of thermal attacks is, of course, a highly exotic reason to discard them. But just think: when your phone recognizes you by your face or fingerprint, you don’t enter a password. When you use a hardware security key, you don’t enter a password. A whole layer of potential attacks (and years of research) becomes irrelevant if no password is entered. Sure, alternative authentication methods have their weaknesses too, but ordinary passwords tend to have more. Modern password-less authentication systems make life almost impossible for phishers. There are many advantages to ditching traditional passwords. And now we have one more: no one will be able to sneak up on you with a thermal imaging camera and steal your secret code. That is, we repeat, if you do not enter it.