The chronicle of WannaCry worm | Kaspersky official blog
Credit to Author: Enoch Root| Date: Wed, 24 Aug 2022 01:19:29 +0000
The WannaCry cryptoworm epidemic began on May 12, 2017. Its victims had their work interrupted by the following on-screen message:
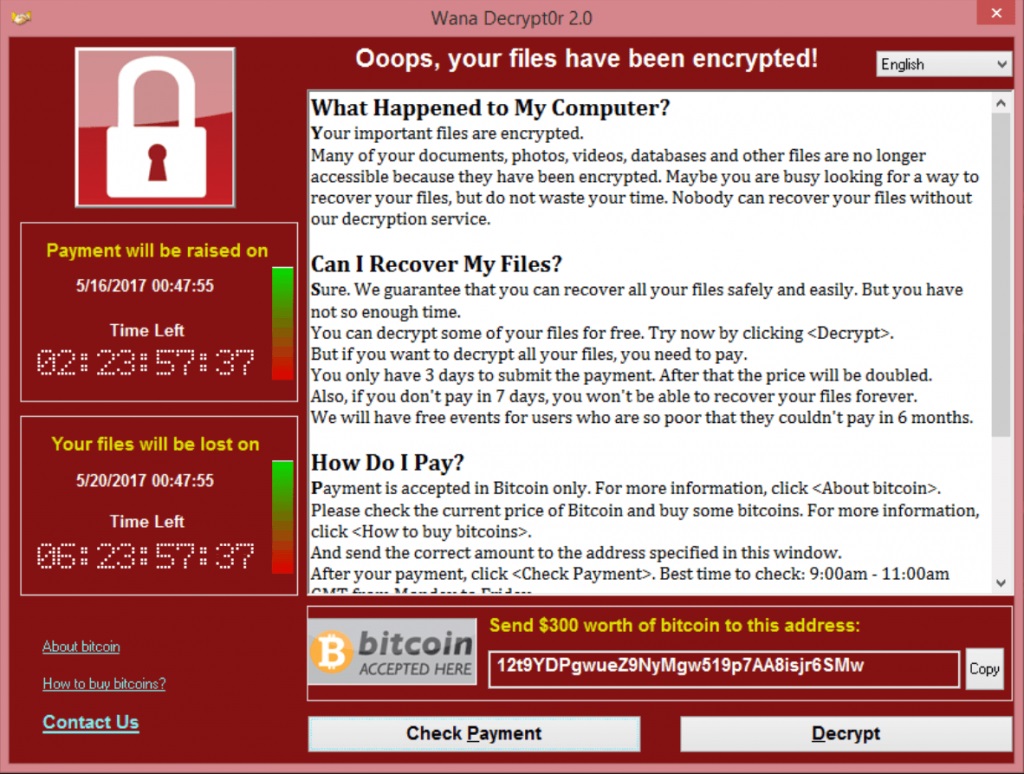
Wannacry ransom note on the screen of an infected computer. Source.
Right after that, victims discovered that all their documents were encrypted, and all normal file extensions like .doc or .mp3 had .wnry extention appended to them. In case anyone will close the window without reading it, the malware also swapped the desktop wallpaper with its own bearing the following message:
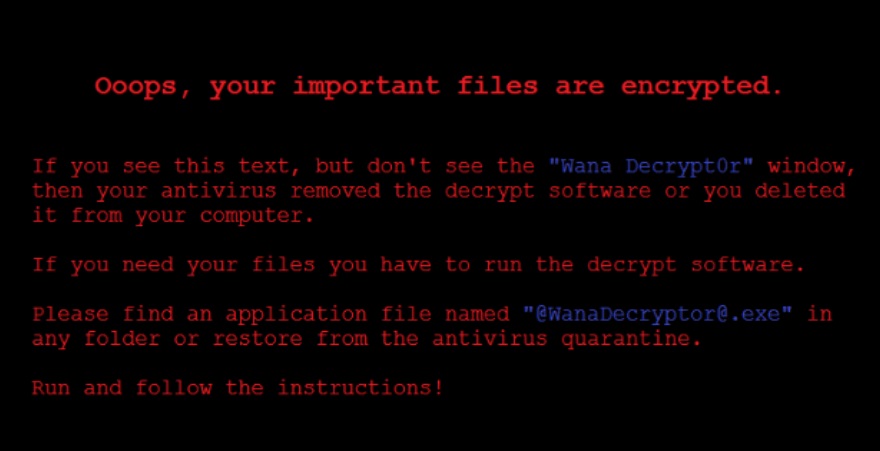
Wallpaper warning. Source.
To decrypt the files, the program demanded transferring $300 in bitcoin to the attackers’ wallet. Later, the amount was increased to $600. Within a day, the rapidly spreading internet worm had infected more than 200,000 systems worldwide, including both home computers and corporate networks: hospitals, transport companies, banking services and cell phone carriers were affected. The Taiwanese chipmaker TSMC had to suspend production due to a mass infection of corporate devices.
How did it happen?
Wannacry’s lightning-fast spread was made possible by vulnerabilities in the Server Message Block (SMB) protocol in Windows. This protocol serves to exchange files over a local network. The vulnerabilities allowed arbitrary code execution on an unpatched computer using a request via the SMBv1 protocol. This is an antiquated version of SMB that has been in use since the early 1990s. Since 2006, the default protocol version used in Windows has been SMBv2 or later, but support for the old protocol was retained for compatibility with computers running legacy software.
When the problem was discovered and updates released in March 2017 (almost two months before the WannaCry outbreak), SMBv1 vulnerabilities affected all unpatched versions of the operating system, from Vista to the then brand-new Windows 10. The outdated Windows XP and Windows 8 were also at risk. Microsoft released a patch for Windows XP, despite having officially pulled support for it back in 2014. The exploit that targeted vulnerabilities in SMBv1 is commonly referred to by the codename EternalBlue, for reasons worthy of a separate mention.
But first, you should know another codename: DoublePulsar. This is the name of the malicious code used to create a backdoor in the attacked system. Both the EternalBlue exploit and the DoublePulsar backdoor were made public by the anonymous group ShadowBrokers in March and April 2017 correspondingly. They, along with other malicious tools, were allegedly stolen from a division of the US National Security Agency. The WannaCry worm uses both components: it first acquires the ability to run malicious code through the EternalBlue exploit, then uses a customized DoublePulsar tool to launch the payload for encrypting files and displaying the ransom note.
In addition to file encryption, WannaCry communicated with the attackers’ C2 server through the anonymous Tor network, and propagated itself by sending malicious requests to random IP addresses. This is what drove the worm’s incredible rate of distribution — tens of thousands of infected systems per hour!
Kill switch
On the same day, May 12, a then-unknown cybersecurity blogger MalwareTech took an in-depth look at the WannaCry code. He discovered that stitched inside the code was an address of the form <very_long_nonsensical_set_of_characters>.com. The domain name was not registered, so MalwareTech registered it to himself, initially assuming that infected computers would use this address for further communication with C2 servers. Instead, he inadvertently stopped the WannaCry epidemic.
Although it transpired that by the evening of May 12, after registration of the domain, WannaCry was still infecting computers, it did not encrypt the data on them. What the malware was doing, in fact, was accessing the domain name and, if this did not exist, encrypting files. Since the domain was now available, all malware instances for some reason halted their efforts. Why did the creators make it so easy to kill their ransomware? According to MalwareTech, it was a failed attempt to deceive automated sandbox analysis.
Sandboxing works like this: a malicious program is run in an isolated virtual environment allowing real-time analysis of its behavior. This is a common procedure that is performed either manually by virus analysts or automatically. The virtual environment is designed to allow the malware to execute fully and give up all its secrets to the researchers. If the malware requests a file, the sandbox pretends that the file exists. If it accesses a site online, the virtual environment can emulate a response. Perhaps WannaCry’s authors believed they could outwit sandbox analysis: if the worm accessed a domain known not to exist, and it got a response, then the victim is not real and malicious activity must be hidden.
What they probably didn’t reckon with was the worm’s code being disassembled in just three hours, and its “secret” domain name being found and registered.
MalwareTech: “the hacker who saved the internet”
MalwareTech had reasons to hide his true identity. His real name is Marcus Hutchins. When WannaCry hit, he was just 23 years old. While still in high school, he fell in with the wrong crowd, as they say, and hung out on forums involved in petty cybercrime. Among his sins was writing a program to steal browser passwords. He also wrote a program to infect users through Torrents, and used it to build a 8,000 strong botnet.
In the early 2000s, he was spotted by a bigger player and invited to write a piece of Kronos malware. For his work, Marcus was paid a commission on each sale on the gray market: other cybercriminals bought the malware to carry out their own attacks. Hutchins revealed that on at least two occasions he gave out his real name and home address in the UK to accomplices. This information later fell into hands of US law enforcement.
The man who “saved the internet” was anonymous no more. Two days later, reporters were knocking on his door: the daughter of one of the journalists went to the same school as Markus, and knew that he used MalwareTech alias. He avoided talking to the press at first, but eventually gave an interview to the Associated Press. In August 2017, now as an honored guest, he was invited to Las Vegas for the famous DEF CON hacker conference.
That’s where he was arrested. After spending several months under house arrest and partially admitting to the charges regarding Kronos, Hutchins got off lightly with a suspended sentence. In a major interview with Wired magazine, he described his criminal past as a regrettable mistake: he did it less for money than the desire to show off his skills and achieve recognition in the underground community. At the time of WannaCry, he had had no contact with cybercriminals for two years, and his MalwareTech blog was read and admired by experts.
Was it the last epidemic?
We recently wrote about the ILOVEYOU worm, which caused a major epidemic in the early 2000s. It had a lot in common with WannaCry: both worms spread through a vulnerability in Windows for which a patch was already available. But not all computers had been updated when the infection broke out. The result was hundreds of thousands of victims worldwide, million-dollar damage to companies and lost user data.
There are differences, too. The creators of WannaCry (presumably a group from North Korea) used off-the-shelf hacking tools available in the public domain. ILOVEYOU simply deleted a few files; WannaCry demanded a ransom from users robbed of all their documents. Luckily, WannaCry’s authors got too cute by embedding a kill switch that worked against them. The story of this epidemic is also about the genius of malware hunters able to take someone else’s handiwork, analyze it in next to no time, and develop a defense mechanism.
The WannaCry epidemic was studied by dozens of companies and received maximum media attention, which makes it rather an exception to the rule. A ransomware attack on a specific business these days is unlikely to get front-page coverage: in fact, you’ll be left facing your tormentor alone. Therefore, it’s important to involve top experts in the damage control operation, and not succumb to extortion. As the case of WannaCry shows, even a highly sophisticated and effective attack can have its Achilles heel.