A Retrospective on the 2015 Ashley Madison Breach
Credit to Author: BrianKrebs| Date: Wed, 27 Jul 2022 01:04:51 +0000
It’s been seven years since the online cheating site AshleyMadison.com was hacked and highly sensitive data about its users posted online. The leak led to the public shaming and extortion of many Ashley Madison users, and to at least two suicides. To date, little is publicly known about the perpetrators or the true motivation for the attack. But a recent review of Ashley Madison mentions across Russian cybercrime forums and far-right underground websites in the months leading up to the hack revealed some previously unreported details that may deserve further scrutiny.

As first reported by KrebsOnSecurity on July 19, 2015, a group calling itself the “Impact Team” released data sampled from millions of users, as well as maps of internal company servers, employee network account information, company bank details and salary information.
The Impact Team said it decided to publish the information because ALM “profits on the pain of others,” and in response to alleged lies that Ashley Madison parent firm Avid Life Media allegedly told its customers about a service that allows members to completely erase their profile information for a $19 fee.
According to the hackers, although the “full delete” feature that Ashley Madison advertises promised “removal of site usage history and personally identifiable information from the site,” users’ purchase details — including real name and address — aren’t actually scrubbed.
“Full Delete netted ALM $1.7mm in revenue in 2014. It’s also a complete lie,” the hacking group wrote. “Users almost always pay with credit card; their purchase details are not removed as promised, and include real name and address, which is of course the most important information the users want removed.”
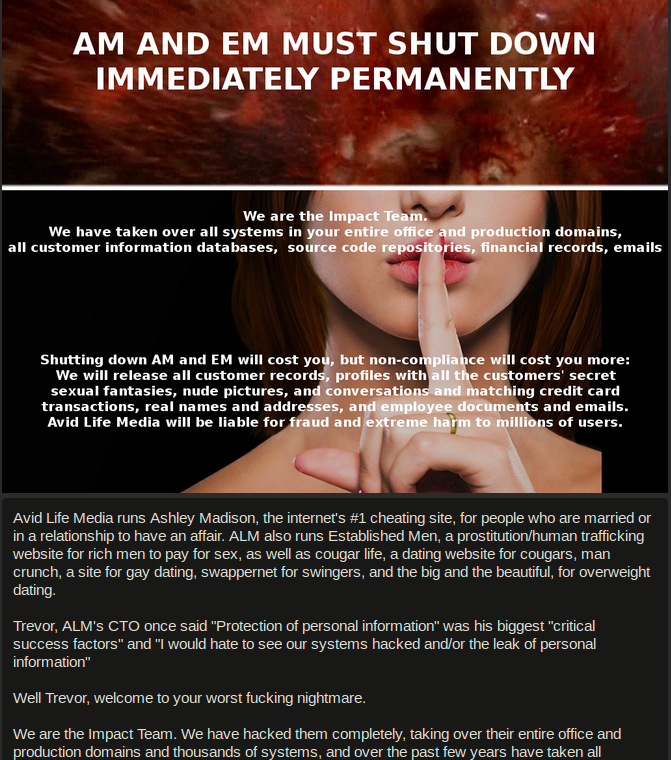
A snippet of the message left behind by the Impact Team.
The Impact Team said ALM had one month to take Ashley Madison offline, along with a sister property called Established Men. The hackers promised that if a month passed and the company did not capitulate, it would release “all customer records, including profiles with all the customers’ secret sexual fantasies and matching credit card transactions, real names and addresses, and employee documents and emails.”
Exactly 30 days later, on Aug. 18, 2015, the Impact Team posted a “Time’s up!” message online, along with links to 60 gigabytes of Ashley Madison user data.
AN URGE TO DESTROY ALM
One aspect of the Ashley Madison breach that’s always bothered me is how the perpetrators largely cast themselves as fighting a crooked company that broke their privacy promises, and how this narrative was sustained at least until the Impact Team decided to leak all of the stolen user account data in August 2015.
Granted, ALM had a lot to answer for. For starters, after the breach it became clear that a great many of the female Ashley Madison profiles were either bots or created once and never used again. Experts combing through the leaked user data determined that fewer than one percent of the female profiles on Ashley Madison had been used on a regular basis, and the rest were used just once — on the day they were created. On top of that, researchers found 84 percent of the profiles were male.
But the Impact Team had to know that ALM would never comply with their demands to dismantle Ashley Madison and Established Men. In 2014, ALM reported revenues of $115 million. There was little chance the company was going to shut down some of its biggest money machines.
Hence, it appears the Impact Team’s goal all along was to create prodigious amounts of drama and tension by announcing the hack of a major cheating website, and then letting that drama play out over the next few months as millions of exposed Ashley Madison users freaked out and became the targets of extortion attacks and public shaming.
Robert Graham, CEO of Errata Security, penned a blog post in 2015 concluding that the moral outrage professed by the Impact Team was pure posturing.
“They appear to be motivated by the immorality of adultery, but in all probability, their motivation is that #1 it’s fun and #2 because they can,” Graham wrote.
Per Thorsheim, a security researcher in Norway, told Wired at the time that he believed the Impact Team was motivated by an urge to destroy ALM with as much aggression as they could muster.
“It’s not just for the fun and ‘because we can,’ nor is it just what I would call ‘moralistic fundamentalism,’” Thorsheim told Wired. “Given that the company had been moving toward an IPO right before the hack went public, the timing of the data leaks was likely no coincidence.”
NEO-NAZIS TARGET ASHLEY MADISON CEO
As the seventh anniversary of the Ashley Madison hack rolled around, KrebsOnSecurity went back and looked for any mentions of Ashley Madison or ALM on cybercrime forums in the months leading up to the Impact Team’s initial announcement of the breach on July 19, 2015. There wasn’t much, except a Russian guy offering to sell payment and contact information on 32 million AshleyMadison users, and a bunch of Nazis upset about a successful Jewish CEO promoting adultery.
Cyber intelligence firm Intel 471 recorded a series of posts by a user with the handle “Brutium” on the Russian-language cybercrime forum Antichat between 2014 and 2016. Brutium routinely advertised the sale of large, hacked databases, and on Jan. 24, 2015, this user posted a thread offering to sell data on 32 million Ashley Madison users:
“Data from July 2015
Total ~32 Million contacts:
full name; email; phone numbers; payment, etc.”
It’s unclear whether the postdated “July 2015” statement was a typo, or if Brutium updated that sales thread at some point. There is also no indication whether anyone purchased the information. Brutium’s profile has since been removed from the Antichat forum.
Flashpoint is a threat intelligence company in New York City that keeps tabs on hundreds of cybercrime forums, as well as extremist and hate websites. A search in Flashpoint for mentions of Ashley Madison or ALM prior to July 19, 2015 shows that in the six months leading up to the hack, Ashley Madison and its then-CEO Noel Biderman became a frequent subject of derision across multiple neo-Nazi websites.
On Jan. 14, 2015, a member of the neo-Nazi forum Stormfront posted a lively thread about Ashley Madison in the general discussion area titled, “Jewish owned dating website promoting adultery.”
On July 3, 2015, Andrew Anglin, the editor of the alt-right publication Daily Stormer, posted excerpts about Biderman from a story titled, “Jewish Hyper-Sexualization of Western Culture,” which referred to Biderman as the “Jewish King of Infidelity.”
On July 10, a mocking montage of Biderman photos with racist captions was posted to the extremist website Vanguard News Network, as part of a thread called “Jews normalize sexual perversion.”
“Biderman himself says he’s a happily married father of two and does not cheat,” reads the story posted by Anglin on the Daily Stormer. “In an interview with the ‘Current Affair’ program in Australia, he admitted that if he found out his own wife was accessing his cheater’s site, ‘I would be devastated.’”
The leaked AshleyMadison data included more than three years’ worth of emails stolen from Biderman. The hackers told Motherboard in 2015 they had 300 GB worth of employee emails, but that they saw no need to dump the inboxes of other company employees.
Several media outlets pounced on salacious exchanges in Biderman’s emails as proof he had carried on multiple affairs. Biderman resigned as CEO on Aug. 28, 2015. The last message in the archive of Biderman’s stolen emails was dated July 7, 2015 — almost two weeks before the Impact Team would announce their hack.
Biderman told KrebsOnSecurity on July 19, 2015 that the company believed the hacker was some type of insider.
“We’re on the doorstep of [confirming] who we believe is the culprit, and unfortunately that may have triggered this mass publication,” Biderman said. “I’ve got their profile right in front of me, all their work credentials. It was definitely a person here that was not an employee but certainly had touched our technical services.”
Certain language in the Impact Team’s manifesto seemed to support this theory, such as the line: “For a company whose main promise is secrecy, it’s like you didn’t even try, like you thought you had never pissed anyone off.”
But despite ALM offering a belated $500,000 reward for information leading to the arrest and conviction of those responsible, to this day no one has been charged in connection with the hack.