How to qualify for cyber insurance
Credit to Author: stephenlawton| Date: Wed, 16 Mar 2022 12:56:58 +0000
Malware, spam, and cyber threats are ubiquitous. In April 2020, approximately one year after the COVID-19 pandemic first became an issue worldwide, Google said it was blocking 18 million malicious COVID-related emails a day and more than 240 million additional COVID-related spam emails daily. And those were only the malicious messages related to the pandemic caught by one provider on one topic.
Not only must businesses have strong technological protections to identify and stop data breaches, ransomware, and phishing attacks with embedded or fileless malware, but they also need business processes in place to mitigate the risk in case something gets past their technology. Today, transferring the risk as part of a comprehensive approach to cybersecurity (your cybersecurity “posture”) includes cyber insurance.
However, for most mid-sized and large organizations, purchasing cyber insurance is not like any other type of insurance one can purchase — one cannot just call up an agent and buy a generic policy as they would for a liability policy for a car, house, or business. Instead, with few exceptions, cyber insurance policies are negotiated rather than purchased as a preconfigured policy, with cyber rates based on anticipated and historical losses and claims, the prospect’s risk profile and other risk-based considerations (collectively, your “cybersecurity posture”).
Why you need cyber insurance
Organizations have two choices when it comes to cyber insurance: finding an insurer who will write a policy to offset some of the losses (called “risk transfer”) or self-insurance, where the organization absorbs all the potential risk (no “risk transfer”). However, with the average ransomware attack costing almost US$2 million per occurrence, it will not take long for most mid-size organizations to run through their set-aside self-insurance resources if they get hit by one or more attacks in a single year.
The Sophos The State of Ransomware 2021 report notes that some 37% of respondents said they suffered a ransomware attack, with the average cost for rectifying the attack being US$1.85 million. When it comes to ransomware, the results are disconcerting.
According to Insurance Journal, the COVID-19 pandemic played a significant role on corporate risk, especially for small to mid-size businesses (SMBs). “Remote work became a major security consideration stemming from the COVID-19 pandemic. The rise in compromised remote desktop protocols (RDPs), leaked credentials, IoT credential stuffing, and more attacks in general, are all reflected in the 400% spike in cyberattacks reported by the [U.S.’s] Federal Bureau of Investigation in the early days of lockdowns in April 2020,” the publication reported.
Some of the factors that determine the risk level include if the business has a history of data breaches, the severity of past breaches, and if the business has in place cybersecurity controls designed to lower the risk. Also important to insurance underwriters is if the organization is taking proactive steps to reduce its risk or if it is reactive or inactive to potential threats.
Understanding cyber insurance’s nuances requires a change in how one views insurance. While the ideal option is to obtain a full cyber insurance policy, some organizations are opting for a less comprehensive and costly cyber insurance endorsement to a standard liability policy.
An endorsement, for example, might only cover liability with coverage for multimedia, security and privacy, some privacy regulatory and Payment Card Industry Data Security Standard losses, along with privacy breach notifications, network asset protection, cyber extortion coverage and brand coverage. This would be a far smaller policy that a full cyber insurance policy, but for some it might be all they qualify to obtain.
Often an endorsement might only pay a relatively small amount, such as US$100,000 or less; some cover as little as $10,000. When one compares that to an average cyber event costing upwards to US$2 million, one sees that endorsements have limited scope. One such endorsement, called the Cyber Event, Identity Restoration and Fraud Loss Coverage, covers policyholders for up to $50,000 for identity restoration expenses and fraud losses but not other items covered in a full cyber insurance policy.
Traditional liability insurance or most kinds of business umbrella, errors and omissions (E&O), or directors and officers (D&O) insurance policies, are well-defined and fairly generic liability policies. An endorsement could add some cyber coverage but is not a replacement for a stand-alone policy.
For an SMB, the endorsement might seem like a possible option but ultimately it can fall far short of providing the coverage an organization requires. As with any policy, potential exceptions could eliminate some of the benefits of the endorsement.
Coverages and exclusions
There is a common misconception that a standard business liability insurance policy will cover a cyberattack. This rarely is the case. Traditional business liability insurance normally covers personal and property damage, not data or the remediation of a cyberattack. Normally, cyber insurance covers both the victim organization and third-party costs. Here are some of the most common coverages for a cyber insurance policy:
- Incident response, including direct costs for responding to the event, investigations, terminating the attack and related costs. It also covers the legal costs associated with determining whether the policyholder needs to give notice to the government, individuals or organizations impacted by the breach
- Forensics fees to investigate the breach or attack and identify the responsible party
- Notifications, credit, and identity monitoring, often for the victims whose personally identifiable information or personal data was compromised
- Data recovery
- Business interruption
- Cyber extortion, including costs associated with ransomware and threats to expose confidential data if an extortion fee is not paid
- Reputational damage, including costs for public relations, media purchases to mitigate harm, and similar reputation mitigation expenses
- Other cybercrimes, including business email compromises, fraudulent instructions, phishing and social engineering attacks
Third-party losses that are normally covered include:
- Security and privacy liability, including legal and settlement costs and often covers regulatory and similar fines and fees
- Media costs related to third-party lawsuits and related legal fees
However, as with all types of liability insurance, there are exclusions. While some exclusions might seem mundane, such as war, invasion, terrorism, or insurrection, others might be surprising. Some policies have a laptop exclusion, security standards exclusions, and Payment Card Industry Data Security Standard (PCI DSS) assessments and fines exclusions. Additionally, if an organization has a prior data breach that is still affecting it or causing current losses, that too is usually excluded from a new policy as a preexisting condition.
The actual coverage and exemptions depend on the negotiations between the insurance company and the client. Should a business choose to reduce its premium by opting out of a specific line item of coverage — take reputational damage, for example — a business potentially could reduce its rates. This might be a choice a business makes if it decides to incur certain expenses on its own rather than spreading that risk to the insurance company as well.
Cybersecurity controls
One approach that insurers take to qualify operations that have mature cybersecurity programs from those that are perhaps less aggressive in investing in cybersecurity operations is identifying and implementing cybersecurity controls.
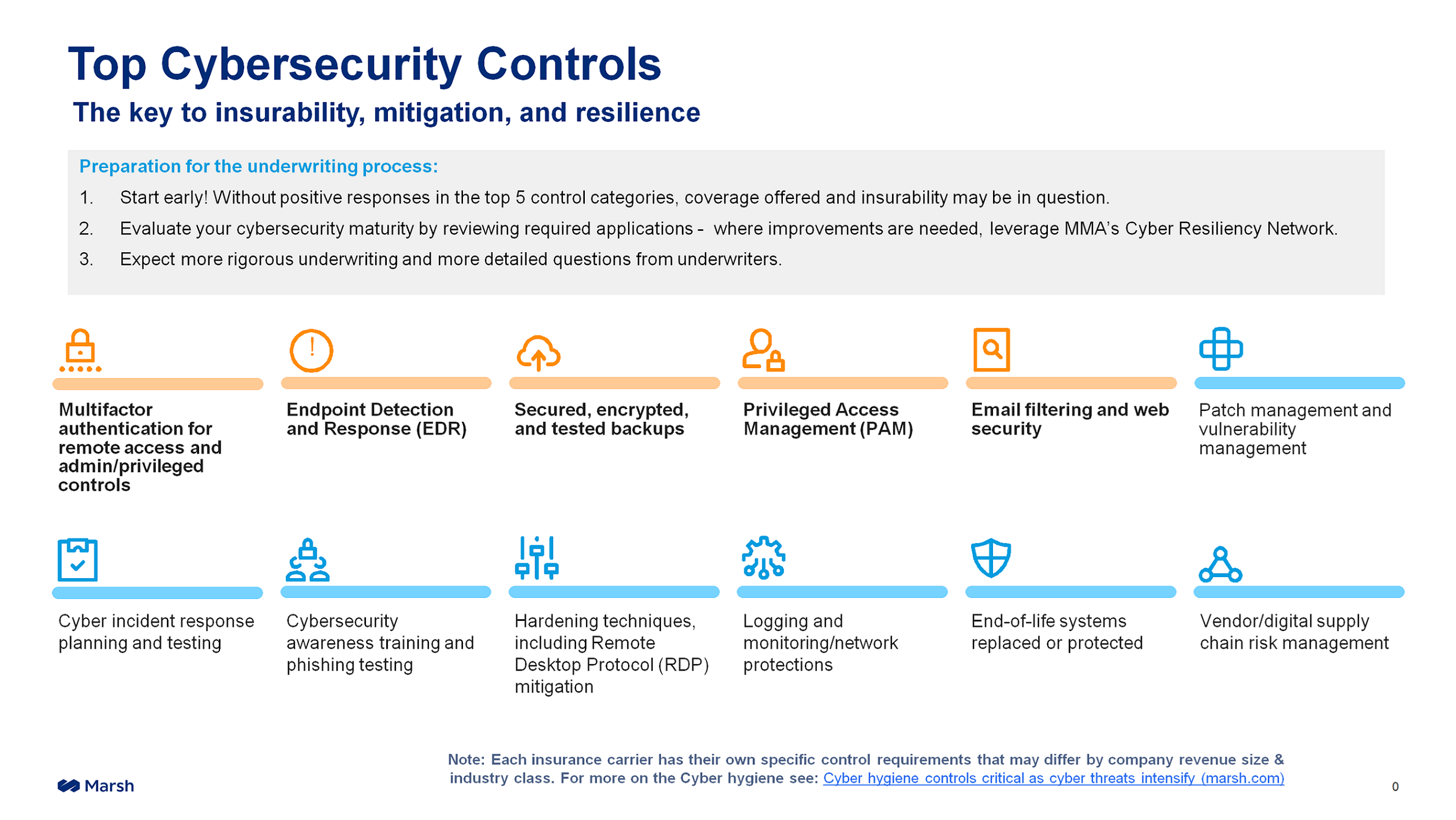
Insurance broker Marsh McLennan Agency (MMA), which serves customers worldwide, has 12 security controls that it deems essential for an organization to employ, but five that it puts at the top tier of the most basic security controls that potential clients must have.
Some of these controls might seem like obvious cybersecurity controls but surprisingly, there are many operations that have yet to fully implement them. These essential controls include multifactor authentication, endpoint detection and response (EDR), secure backups, privileged access management, and advanced email filtering.
Businesses that want a new cyber insurance policy or renewal of an existing policy with MMA must have at least the top five of the 12 top security controls in place to open discussions, and ideally should have all 12 of the controls in place, although even with all 12 controls in place getting a cyber insurance policy is not guaranteed.
Sophos offers products and services that address nearly all the 12 security controls from MMA. For more information on the Sophos offerings that address each of these controls, you can download Top Cybersecurity Controls Required to Secure Cyber Insurance and How Sophos Can Help.
Coverages and capacities
Organizations need to demonstrate they are serious about reducing risk in today’s tight insurance market. Business Insurance described the market pressures this way: “Driven by ransomware attacks, the cyber liability insurance market has been hardening at a dizzying pace, with increased losses, rising rates, higher retentions, the imposition of sub-limits and coinsurance requirements, limited capacity, and insurers’ sometimes onerous information demands that must be met before coverage is provided.”
The article went on to note that as losses mount, cyber insurers are reducing the capacity of insurance available in general — with a reduced amount of coverage written per policy and the number of policies being written overall. As available insurance volume diminishes, prices will go up, coverage will decrease, and terms will be more restrictive.
This lack of capacity is one of the driving forces behind the higher rates. “Capacity restrictions that started to impact the market [in 2020] have intensified in 2021,” wrote Insurance Business Magazine last year.
Insurers that were happy to issue $5 million cyber liabilities policies in 2020 have scaled back to limits of $1 million to $3 million this year, even on renewals, according to Risk Placement Services, a U.S. national broker that also can bind customers through a partnership with Lloyd’s of London. “As a result,” the story continued, “organizations have had to turn to additional carriers to reach desired cyber liability coverage limits.”
Marc Schein, a risk management consultant and National Co-Chair Cyber Center of Excellence at MMA, said that while it was normal for his firm to write policies for US$10 million in the past, many of the current policies were only for US$3 million to US$5 million. But MMA is not alone — many of the insurers are sharply reducing coverage while concurrently increasing prices.
Considering that no two organizations normally have exactly the same requirements for coverage, especially when it comes to business interruption, data recovery, notifications and the like, no two policies will be exactly the same. Similarly, no two businesses approach proactive cybersecurity the same way. The terms, coverage and premiums ultimately are a combination of the organization’s risk profile, combined with the amount of coverage it requires, its policy two reducing risk, and its history, experts agree. It also depends on the negotiation between the insurance company and the client.
Prices go up; coverage goes down
While the cyber insurance industry is still in somewhat of its early stages of maturity, insurers’ payouts in 2021 were far higher than they anticipated due to ransomware attacks and policies they wrote for companies that had unaddressed vulnerabilities. Nowhere was this more evident than in Canada, where cyber security insurers paid out far more than they took in.
In the August 2021 article How much Canadian insurers have lost on cyber liability so far in 2021 in Canadian Underwriter, Greg Meckbach wrote: “In cyber liability, total net premiums earned for the second half of 2021 were CA$94.15 million – CA$12.15 million from Canadian insurers and CA$82 million from foreign insurers. But total net claims incurred (not including reinsurers’ share but including adjustment expenses) were CA$106.26 million (CA$97.4 million from foreign insurers and CA$8.86 million from Canadian insurers), for a loss ratio of nearly 113%.”
In November, Reuters reported a phenomenon that businesses around the world began discovering on their own: Where they once were able to get elevated levels of coverage for reasonable rates, these insurers were tipping the proverbial tables. The Reuters story quoted David Dickson, head of enterprise at broker Superscript, stating: “It’s very unlikely people are getting the same limits — if they are, they are paying an extraordinary amount.”
Dickson reported a story of a U.K.-based technology client that previously purchased UK£130 million of professional indemnity and cyber coverage for UK£250,000. However, that coverage fell by more than half from UK£130 million to just UK£55 million but the price for the lower amount soared to UK£500,000 when the policy was renewed.
The reduced coverage is a significant problem for businesses that have made representations in contracts that they have certain levels of cyber insurance coverage — perhaps indicating that they had US$25 million in coverage. When the cyber insurance vendors reduce that coverage to just US$5 million, for example, that could leave the policyholder in a potential breach of contract with their customer to whom they assured they had higher cyber insurance coverage.
Ultimately that means the organizations need to either find additional coverage from the same or another broker or carrier, or they must renegotiate their contracts to disclose a lower rate of coverage. Finding that additional coverage, however, is even more difficult when the business might require more multiple cyber insurers to fill the legal representation gap.
Many businesses include statements of cyber insurance coverage in their contracts. Should a business contractually agree to carrying a specific level of cyber insurance and later lose all or part of that policy, the loss of a cyber policy could put it into breach of contract. While laws around the world normally permit a business time to replace the policy, it can be a huge challenge to do so in today’s market. This is one of the main reasons why organizations are motivated to maintain their policies, regardless of price.
Positioning yourself for the future
Currently there are few indicators that point to the capacity of cyber insurance increasing or prices falling. The current tightening of the market is attributed to increased ransomware, the issues organizations are facing due to the ongoing pandemic, and perhaps a lack of resolve by some to make aggressive moves to proactive cybersecurity.
MMA’s 12 security controls mirror closely the security controls recommended by other brokers and carriers—there appears to be a consensus that organizations that want cyber insurance need to do a better job of lowering their risk and investing in cybersecurity before the insurance industry relents and agrees to increase capacity or lower their cybersecurity requirements.
Improving your cybersecurity profile and lowering risk are what insurers desire. Demonstrating a proactive approach to cybersecurity, along with reducing your risk profile and making a concerted effort to meeting and exceeding best practices, shows underwriters that a company is a particularly good insurance risk and less likely to submit a claim.
Another way organizations can demonstrate a dedication to reducing their risk profile is to have a third party, such as an auditor, certified public accountant (CPA) or other professional, certify the reduction of risk, be it implementation of organization-wide multifactor authentication, implementing privileged access management for all privileged users, or testing and remediating all third-party risk management vulnerabilities.
Insurers appreciate a third-party certification of proactive risk reduction as a stronger statement than simply self-attestation by the organization making the claim, the experts agreed. While self-attestation is permitted on many insurance applications, the third-party sign-off verifies that the security controls were not only implemented but done so correctly and have been tested.