VB2019 paper: Different ways to cook a crab: GandCrab Ransomware-as-a-Service (RaaS) analysed in depth
Though active for not much longer than a year, GandCrab had been one of the most successful ransomware operations. Running as a Ransomware-as-a-Service scheme, the malware regularly updated itself to newer versions to stay ahead of decryptors released by security researchers.
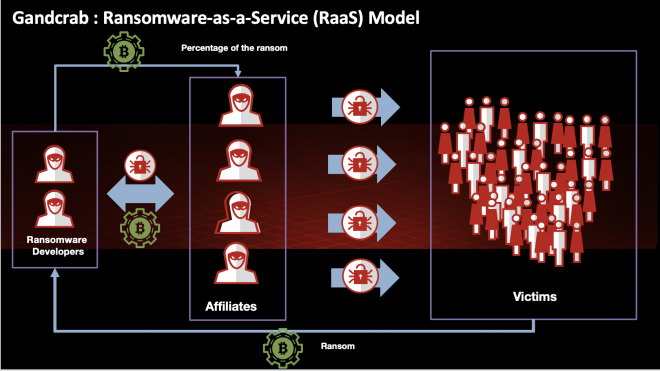 High-level overview of the GandCrab RaaS model.
High-level overview of the GandCrab RaaS model.
In a paper presented at VB2019 in London, McAfee researchers John Fokker and Alexandre Mundo looked both at the malware code and its evolution, and the affiliate scheme behind it or, as they presented it: how GandCrab is cooked. Through affiliate IDs, they were able to track various actors using the scheme to infect users and organisations.
Not included in the paper, but discussed in their presentation, was more recent research that links GandCrab to Sodinokibi, a ransomware family that appeared earlier this year. This research was published in a series of McAfee blog posts last month.
Today we publish John and Alexandre’s paper in both HTML and PDF format. We have also uploaded the video of thier VB2019 presentation to our YouTube channel.
outertext
https://www.virusbulletin.com/rss