What is a hoax, where do hoaxes come from, and why are they dangerous?
Credit to Author: Artemy Ovchinnikov| Date: Wed, 19 Jun 2019 11:45:26 +0000
Kaspersky products characterize certain software as “Hoax.” Let’s investigate what this verdict means, in which cases our products deliver that verdict, and why users should beware of such programs.
Astrologers announce the year of the Hoax: Detections double
The reason for this post is the increase in the number of detections our products have been making with the Hoax verdict. The number of users who have encountered such software has doubled in the past year. In short, more and more users are being caught in the risk zone. So it’s worth taking the time to dissect the problem, starting with a brief background discussion.
Many users complain of slow computer bootup and application startup times, and even system crashes with errors. It’s a problem that just about everyone faces now and again. It happens because during operation the computer gets clogged up with all kinds of data, affecting its processing speed.
Demand generates supply, so programs promising to speed up and scrub down the computer soon started multiplying. The rapid growth in such software began in the late 2000s and never stopped.
Cleanup programs generally look for unused or temporary files, registry keys, startup programs, and so forth, and report the presence of such “digital garbage” to the user, who then decides to have the program clean up the computer. That does improve overall system performance to some extent.
Unfortunately, not all cleanup/speed-up software is equally benign. Amid the ranks of honest developers who create programs to help users, there are a good many cybercriminals at play.
What is a Hoax?
Some programs for cleaning up the computer and improving performance force the user to pay to get rid of alleged detected threats. Two key features help distinguish the good guys from the bad:
- First, the latter deliberately mislead the user by greatly overstating the risk, or even reporting non-existent errors.
- Second, they compel, rather than invite users to make a purchase, declaring that without payment the problem cannot be solved.
At Kaspersky, we call such programs Hoax — software that intentionally misleads the user. Here are some examples of verdicts that Kaspersky products assign to such programs:
- HEUR:Hoax.Win32.Uniblue.gen
- Hoax.Win32.PCFixer.gen
- Hoax.Win32.DeceptPCClean.*
- Hoax.Win32.PCRepair.*
- HEUR:Hoax.Win32.PCRepair.gen
- HEUR:Hoax.MSIL.Optimizer.gen
- Hoax.Win32.SpeedUpMyPC.gen
How Hoax programs work
After installation, Hoax programs run a system scan. They scan everything that legitimate cleaners do. After the scan, the user sees a window with information about issues detected.
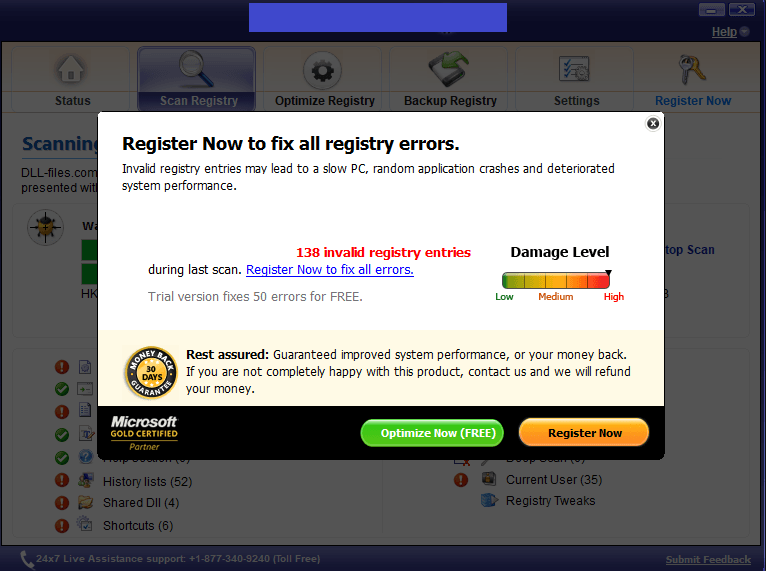
And that’s the main problem with this breed of software. The user is shown intimidating messages about the supposedly huge number of errors found in the system. Here is an example of a “cleaner” that overplays potential problems with registry keys:
Or the tool might find some real bugs, but then overstate the level of importance through deceptive language. For example, in this driver updater, the driver status varies from “old” to “ancient”:
Some programs refuse to close immediately when the user clicks the little x, instead displaying another window with the intimidating message “Damage level: high.”
Hoax programs also like to add themselves to autorun and flood the user with pop-up notifications that something is wrong with the computer.
Hoax programs are not restricted to the Windows ecosystem. Here is an example of one for MacOS, with mildly high log/cache usage is reported as critical.
To resolve the issue, the user is told to acquire the full version of the software. When the full version is purchased, many of these programs really do rid the computer of what they found, but the need for such services is overstated, as mentioned above. Some Hoax programs may not clean the computer at all. So at best the user overpays, and at worst, they get nothing for their money.
Bundled adware and the chance to win a Trojan
In their greed, some creators of fraudulent cleaners go a step further and, in addition to their own handiwork, install other programs on the user’s computer. It’s usually adware, but in some cases, it can be a Trojan.
For example, getting mixed up with a Hoax utility could result in a user’s computer being partially blocked. The program pictured below expands to full screen, overlaps the toolbar, and blocks attempts to switch between programs by pressing Alt+Tab and to get back by pressing F11.
Next, the user is prompted to enter a code to unblock the computer (which, of course, they do not have), or to open remote access to it through TeamViewer, AnyDesk, or other remote access programs whose icons are placed conveniently at the right of the window.
How a Hoax penetrates the computer
Hoax developers’ target audience is inexperienced home users not very familiar with device operating systems or concerned about “taking out the trash” and updating the system.
When the computer starts to slow down noticeably, many users search online for solutions and may pick up a Hoax app if they are not careful.
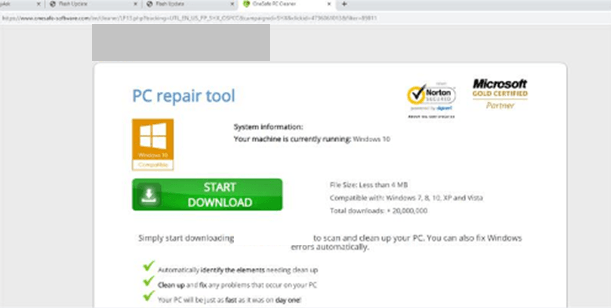
But there is also another distribution method. A Hoax is sometimes acquired through promotional offers or scam Web pages. An adware-based infection might look as follows:
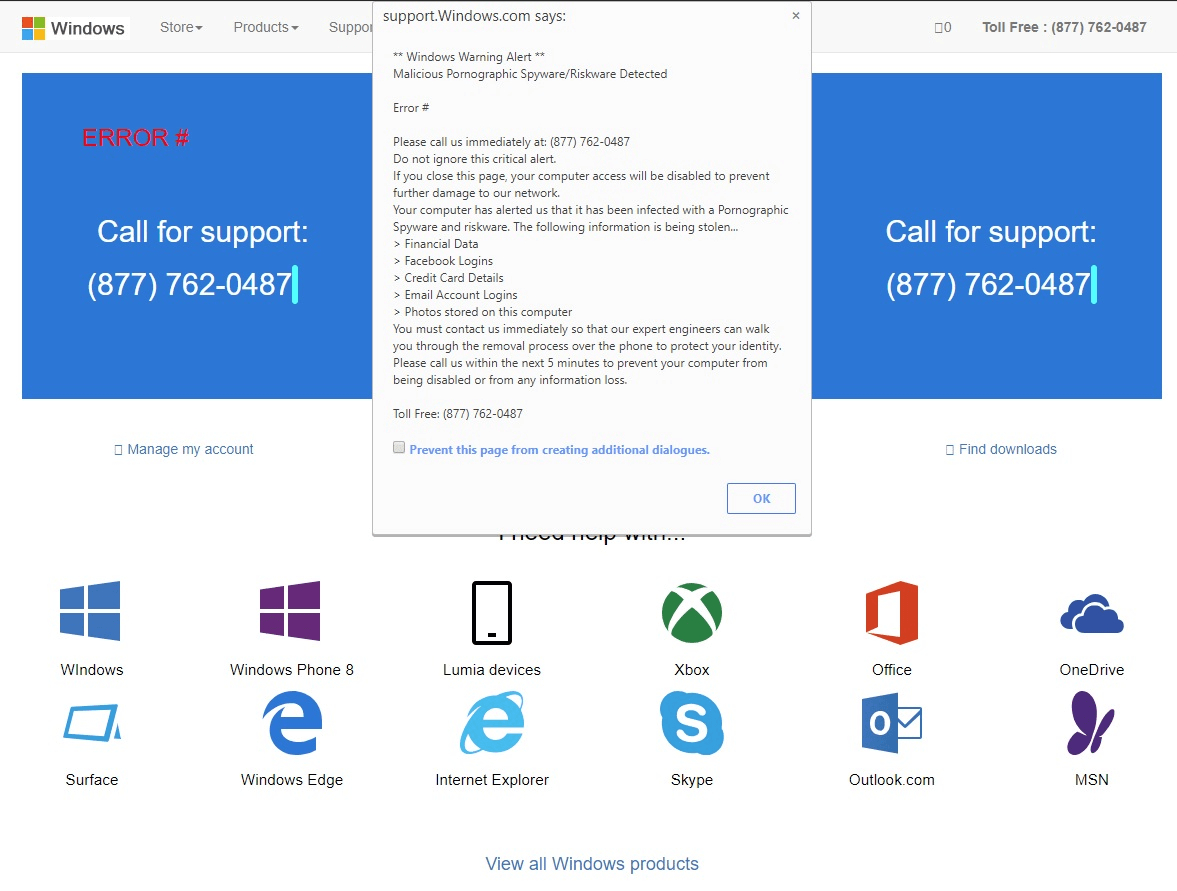
You may also encounter fraudulent pages offering cleanup/speed-up “services” when visiting dubious websites. For example, this page displays a notification that spyware was detected on the computer.
Usually, the user is prompted either to call “technical support” (where money is extorted verbally), or to download a Hoax utility. Don’t trust such pages for one second — just close them immediately.
Another increasingly common way to spread Hoax software is through browser pop-up notifications, which some users agree to for without thinking. Browser push notifications are now very popular (including among scammers), and they are starting to cause many user headaches.
Not everyone understands how they work, where they come from, and how to disable them. Sometimes users are not even aware these notifications come through their browser, and that they may come from websites with less-than-pure intentions.
After clicking such notifications, users are taken to fraudulent pages masked as security components. Here is an example of a fraudulent website simulating the Windows Defender interface:
Once the user is sufficiently spooked by all the apparent problems with their computer, they are redirected to a Hoax download page.
Hoax distribution statistics and geography
As mentioned at the start of the post, in late 2018 we observed a boom in activity in the market for fraudulent performance optimization software. That boom is ongoing. The number of affected users has doubled since the beginning of last year, with a corresponding rise in complaints.
Our statistics show that the most popular target country for Hoax creators and distributors is Japan, where in recent years one in eight users has encountered it. Japan is followed by Germany and, surprisingly, Belarus. Italy and Brazil round out the top five.
Antivirus developers are stemming the Hoax tide to some extent, with some fraudulent programs even banished from the “market.”
In response, various Hoax distributors are abandoning the “intimidation” distribution model in favor of informing users more properly, not overly inflating the severity of the issues they find, and offering free trial versions of their products. All the same, the struggle is far from over.
Why are Hoax apps bad?
We consider it important to warn users about Hoax-category programs for several reasons:
- The creators of such software deliberately mislead users by overstating the risk of the problems they detect — or even reporting nonexistent ones.
- Such “services” can be unreasonably costly.
- Some Hoax programs do not address any real issues at all, and only create the illusion of fixing errors.
- A number of Hoax creators additionally install software ranging from adware to downright malware along with their programs.
How to protect against Hoax software
These tips will help you guard against the potential threat:
- Ignore intimidating warnings about viruses or errors on your computer displayed by websites. Never click on such warnings, let alone download and install anything.
- Take care to select a quality cleanup tool, if you want to use one; do some research and heed the advice of reputable computer publications.
- To avoid a rendezvous with a Hoax, install a reliable antivirus solution that will warn you about fraudulent programs.