A helping hand for a smart hand: How we hacked it so others wouldn’t
Credit to Author: Marvin the Robot| Date: Wed, 27 Feb 2019 19:14:24 +0000
“The S in IoT stands for security” is perhaps the most over-told joke of recent years in the field of information security. Sure enough, security experts have long made fun of the Internet of Things, and every hacker conference worth its salt always has a talk about yet another so-called smart device having been hacked in some crazy way. Everyone is so used to such cases that they are surprised when the opposite happens and researchers conclude that a device is actually rather secure.
Usually, research focuses on IoT vulnerabilities and how they threaten users. But every coin has a flip side: Vulnerabilities in smart devices can be dangerous for the developers too; they can cause data leakage or damage, disrupt infrastructure, and render the devices themselves broken or useless.
At MWC19, experts from our Industrial Industrial Control Systems Cyber Emergency Response Team (ICS CERT) presented a report on smart artificial limbs developed by Motorica.
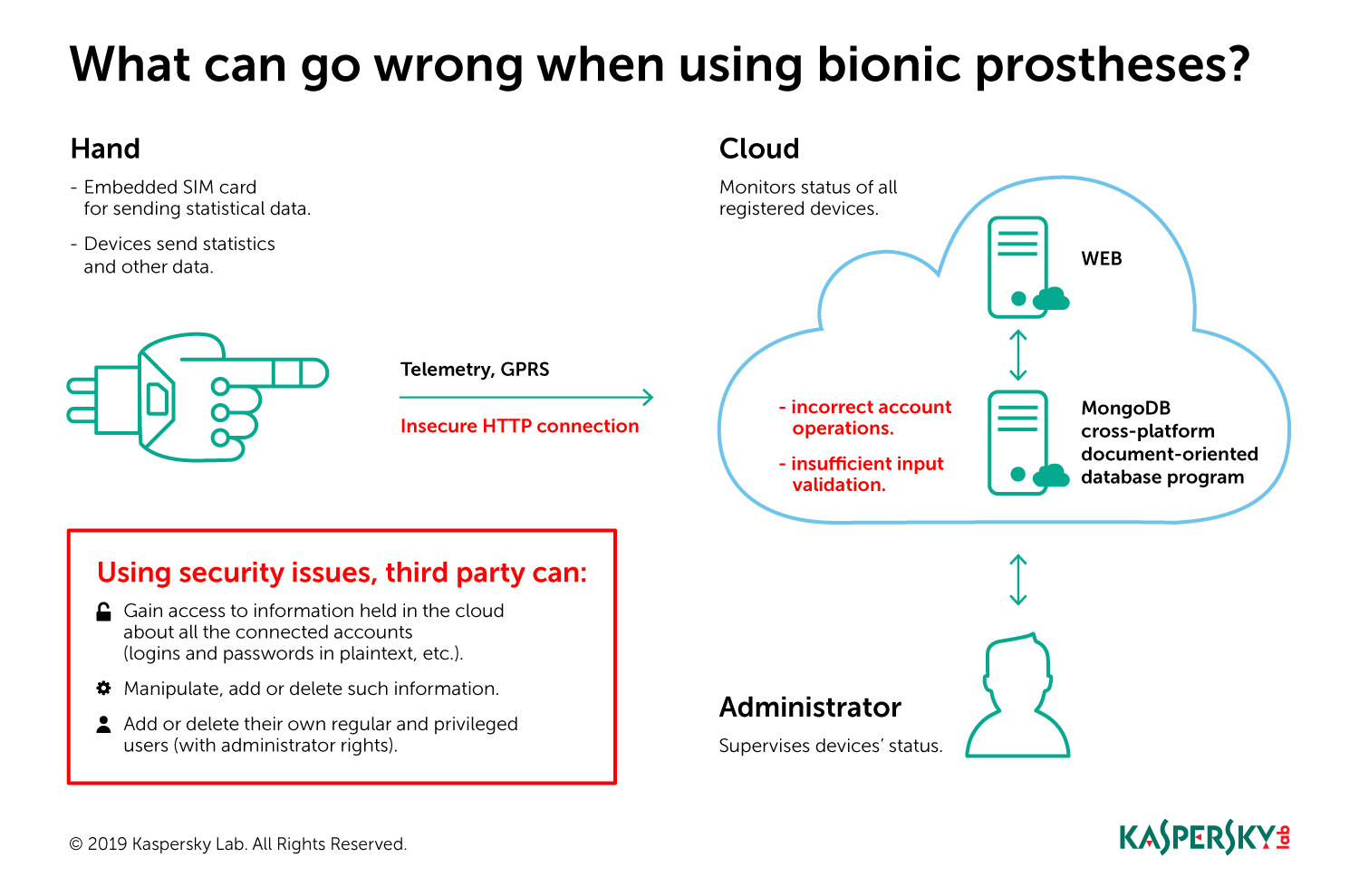
Let’s start with the good news. First, our experts did not find any vulnerabilities in the firmware of the prosthetic limbs themselves. Second, in Motorica’s system data moves in one direction only — from the limb to the cloud. This means, that it is not possible, for example, to hack into a hooked-up smart limb and take control of it remotely.
However, further study revealed some serious flaws in the development of the cloud infrastructure for collecting and storing telemetry data obtained from prosthetic limbs, allowing hackers to:
- Gain access to the data of all system accounts (both user and admin), including unencrypted logins and passwords.
- Read, delete, and modify telemetry data stored in the database, or add new entries.
- Add new accounts (including admin).
- Delete or modify existing accounts (for example, change the admin password).
- Launch a DoS attack against an administrator, blocking login to the system.
These vulnerabilities potentially allow user data leakage or damage. Moreover, the last of the above bullet points would significantly increase the time needed to respond to the hack.
Naturally, our researchers reported all detected vulnerabilities to Motorica, and to date all found problems have been fixed. Unfortunately, this victory is just one minor battle in the far wider war to make the Internet of Things safe. Here’s what needs to change:
- Developers should be aware of the most common threats and best practices for creating secure code. This is crucial at all stages of development — our research clearly illustrates that errors in the creation of one part of the system can have a catastrophic knock-on effect.
- Manufacturers of smart gadgets should introduce bug bounty programs, which are very effective for finding and fixing vulnerabilities.
- Ideally, products under development should undergo security assessments by information security experts.