Email Provider VFEmail Suffers ‘Catastrophic’ Hack
Credit to Author: BrianKrebs| Date: Tue, 12 Feb 2019 13:33:31 +0000
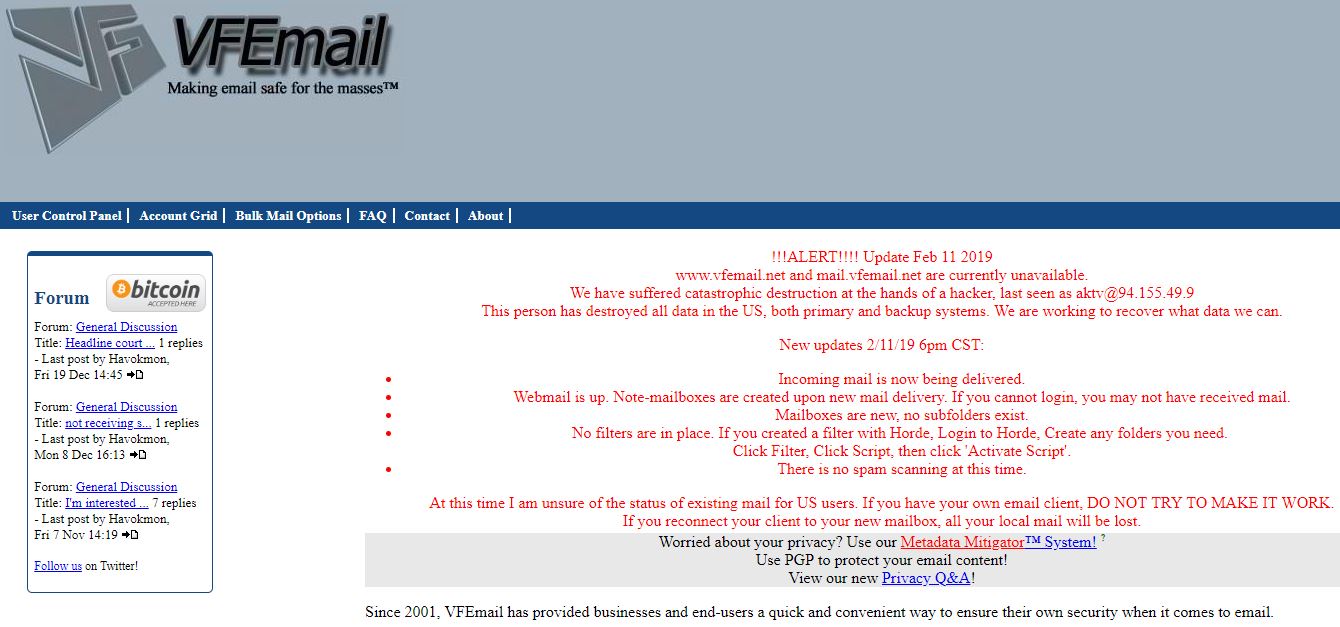
Email provider VFEmail has suffered what the company is calling “catastrophic destruction” at the hands of an as-yet unknown intruder who trashed all of the company’s primary and backup data in the United States. The firm’s founder says he now fears some 18 years’ worth of customer email may be gone forever.
Founded in 2001 and based in Milwaukee, Wisc., VFEmail provides email service to businesses and end users. The first signs of the attack came on the morning of Feb. 11, when the company’s Twitter account started fielding reports from users who said they were no longer receiving messages. VFEmail’s Twitter account responded that “external facing systems, of differing OS’s and remote authentication, in multiple data centers are down.”
Two hours later, VFEmail tweeted that it had caught a hacker in the act of formatting one of the company’s mail servers in The Netherlands.
“nl101 is up, but no incoming email,” read a tweet shortly thereafter. “I fear all US based data my be lost.”
“At this time, the attacker has formatted all the disks on every server,” wrote VFEmail. “Every VM [virtual machine] is lost. Every file server is lost, every backup server is lost. Strangely, not all VMs shared the same authentication, but all were destroyed. This was more than a multi-password via ssh exploit, and there was no ransom. Just attack and destroy.”
In an update posted to the company’s Web site, VFEmail owner Rick Romero wrote that new email was being delivered and that efforts were being made to recover what user data could be salvaged.
“At this time I am unsure of the status of existing mail for US users,” Romero wrote. “If you have your own email client, DO NOT TRY TO MAKE IT WORK. If you reconnect your client to your new mailbox, all your local mail will be lost.”
Reached by KrebsOnSecurity on Tuesday morning, Romero said he was able to recover a backup drive hosted in The Netherlands, but that he fears all of the mail for U.S. users may be irreparably lost.
“I don’t have very high expectations of getting any U.S. data back,” Romero said in an online chat.
John Senchak, a longtime VFEmail user from Florida who also has been a loyal reader and commenter at this blog, told KrebsOnSecurity that the attack completely wiped out his inbox at the company — some 60,000 emails sent and received over more than a decade.
“I have a account with that site, all the email in my account was deleted,” Senchak said.
Asked if he had any clues about the attackers or how they may have broken in, Romero said the intruder appeared to be doing his dirty work from a server based in Bulgaria (94.155.49[9], username “aktv.”)
“I haven’t done much digging yet on the actors,” he said. “It looked like the IP was a Bulgarian hosting company. So I’m assuming it was just a virtual machine they were using to launch the attack from. There definitely was something that somebody didn’t want found. Or, I really pissed someone off. That’s always possible.”
This isn’t the first time criminals have targeted VFEmail. I wrote about the company in 2015 after it suffered a debilitating distributed denial-of-service (DDoS) attack after Romero declined to pay a ransom demand from an online extortion group. Another series of DDoS attacks in 2017 forced VFEmail to find a new hosting provider.
In December 2018, Romero tweeted that service had been disrupted by a DDoS attack that he attributed to “script kiddies,” a derisive reference to low-skilled online hooligans.
“After 17 years if I was planning to shut it down, it’d be shut down by me – not script kiddies,” Romero wrote on Dec. 8.
Attacks that seek to completely destroy data and servers without any warning or extortion demand are not as common as, say, ransomware infestations, but when they do occur they can be devastating (the 2014 Sony Pictures hack and the still-unsolved 2016 assault on U.S.-based ISP Staminus come to mind).
It’s not clear how or whether VFEmail will recover from this latest attack, but such actions are an unsettling reminder that although most cybercriminals have some kind of short- or long-term profit motive in mind, an intruder with privileged access to a network can just as well virtually destroy everything within reach as they can plant malware or extortion threats like ransomware.