Crazy Razy, bitcoin thief
Credit to Author: Pavel Shoshin| Date: Thu, 24 Jan 2019 16:07:51 +0000
If you use a different browser than the operating system’s default, you most likely know about extensions for it, and you might even use a couple. And if you are a regular reader of this blog, you will be aware that some of them are dangerous and should be installed from official sources only. The problem is that malicious add-ons can be installed without the knowledge of the user — or even any actions (well, almost).
How Razy installs malicious extensions
The prime suspect is the Razy Trojan, which retrofits Google Chrome, Mozilla Firefox, and the Yandex Browser (all for Windows) with its own plugins. You can get more details at Securelist.com, but, basically, the malware disables scanning of extensions being installed, blocks the browser from updating just in case, and then starts installing malicious add-ons: Firefox receives the Firefox Protection extension; Yandex Browser gets Yandex Protect.
Even if the names are deceptive, their sudden appearance should raise a flag. In this regard, the script for Google Chrome is particularly dangerous: Razy can infect the Chrome Media Router system extension, which does not appear in the general list of browser plugins, and without security software is detectable only indirectly.
What happens after infection
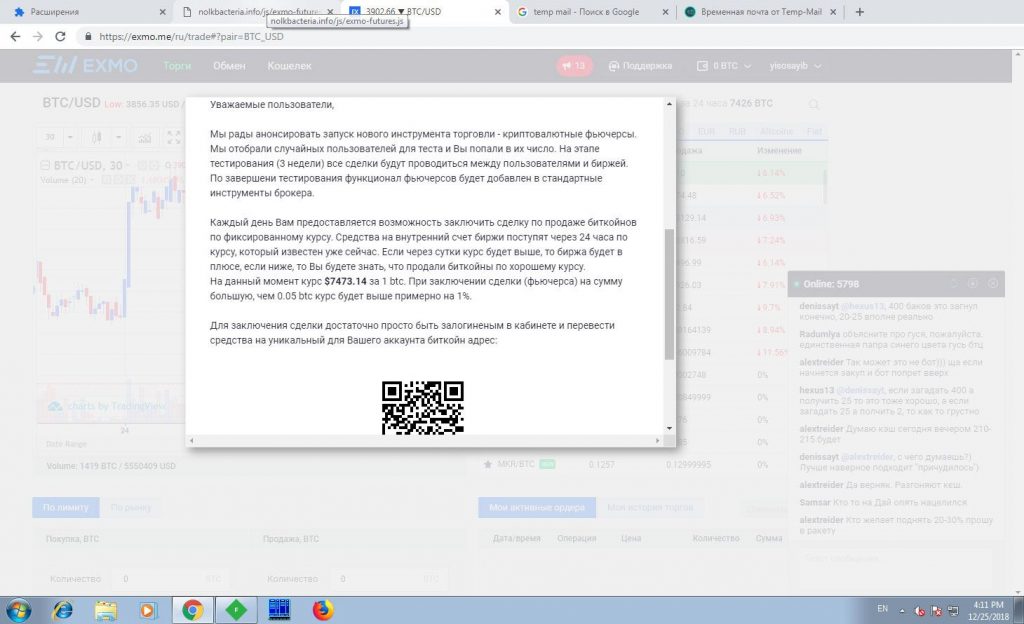
The whole scenario is a classic example of a man-in-the-browser attack. The malicious extensions alter website content as their creators desire. In the case of Razy, cryptocurrency owners have the most to fear. The extension targets cryptoexchange sites, adorning them with banners displaying “lucrative” offers to buy or sell cryptocurrency — but users who swallow the bait end up enriching the cybercriminals, not themselves.
On top of that, the add-on spies on user searches in Google or Yandex, and if a search query is about cryptocurrency, embeds links to phishing sites in the search results page.

Razy results: The top five links in the search results are added by the malicious extension and point to phishing sites
Another way to “redistribute” coins is to replace all wallet addresses (or QR codes) on a Web page with the addresses of cybercriminal-owned wallets.
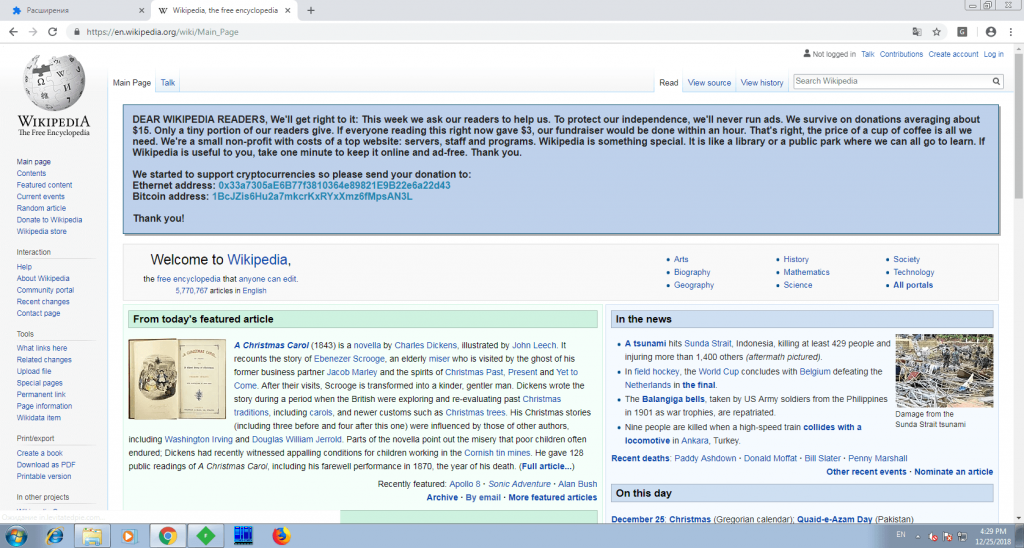
Users of infected browsers are also pursued by banners (for example, on Vkontakte or Youtube) with generous offers such as: “Invest a bit now, earn a million later,” “Get paid for an online survey,” and so on. The cherry on top is the fake banner on Wikipedia pages asking users to support the project.
How to protect against Razy
The Razy Trojan is distributed under the guise of useful software through affiliate programs, and it may be downloaded from various free file-hosting services, so the advice on how to guard against this infection is fairly standard:
- Download apps only from developer websites and sources that you trust.
- Scan your computer immediately if you notice any suspicious activity on the computer (for example, the appearance of unfamiliar optimizer tools), which could indicate you were tricked into installing malware.
- Check for browser plug-ins that seem to appear out of thin air, and disable any that seem suspicious.
- Use a reliable antivirus solution.
https://blog.kaspersky.com/feed/