Meet the Hacker Who Busts Child-Pornographers on the Dark Net
Credit to Author: Daniel Mützel| Date: Wed, 08 Nov 2017 14:00:00 +0000
A version of this article originally appeared on Motherboard Germany.
In October, the Norwegian hacker Einar Otto Stangvik unveiled the largest and most well-known dark web portal for the sexual abuse of children through a great deal of patience, creative ideas, and a simple technological trick.
But Stangvik and his colleagues at the newspaper VG could hardly believe what they discovered this past January: The forum Childs Play, which had more than a million users worldwide, was run by a task force of the Australian police.
For eleven months, the Australian investigators monitored the site for information about perpetrators, victims, and users. Just a few weeks ago, the portal was taken down.
It wasn’t the first time that Stangvik, who used to work as an IT-security expert for various Norwegian companies, had dug around the darker corners of the web to hunt down backers and perpetrators of child pornography. Back in 2015, he used a program he’d written himself to unmask 95,000 users worldwide who had downloaded photos and videos online.
We wanted to find out from Stangvik: How do you track pedophiles on the dark net? Is the dark net really that much worse than the regular internet when it comes to child pornography? Is it justifiable for the police to masquerade as child-pornography admins for eleven months—or are there technological alternatives?

MOTHERBOARD: You managed to unveil a massive child pornography platform on the dark net. How did you approach this task?
Einar Otto Stangvik: We spent a month putting our heads together to figure out how to attack the platform. We didn’t want to unmask just those behind Childs Play, but also the users: Producers of child-pornographic videos, for example, and people who sexually abuse children. I then tried to download all the text on the platform to classify it, but that ultimately led to a dead end. At the end of 2016, we had to put our research on hold for a while, because we couldn’t find an effective avenue to hack the site.
How’d things progress from there?
It happened at the beginning of January of this year. I got to the office and it became clear to me that I had to approach this in a completely different way. So I spent the whole day wading through source codes from MyBB—the software system used by Childs Play. It was only then that I stumbled across the upload function that allows you to set your profile picture on Childs Play. I was dumbfounded when I realized that the function isn’t secured through Tor.
Why did this discovery surprise you so much?
Because I was able to use the cheapest trick in the book. Because to crack the software of a website, you have to find a way to upload files or smuggle in your own code. You essentially force the server to connect to the outside world, opening up a weak spot for attacks. Most software programs don’t allow that, because attacks on a server through local files is the most obvious gateway overall. I actually expected that a dark net site—especially one that disseminates abusive material—would have blocked all external connections. Or, at the very least, that they would have used the Tor network for connections like these.
So uploading a pic was the cheapest trick in the book, but it worked?
I was skeptical at first. Somehow it seemed like the dumbest method to force a server to reveal its IP address. But I tried it anyway. Much to my surprise, I actually got back an IP.
You found the weak spot in January 2017, at which point the Australian police had been running the server for three months. Was that error connected to the police admins, or had it already existed before?
Tough to say. When I found the weak spot, I didn’t have the slightest clue that the police were behind the site. When I found it, I have to say I was a little surprised, but not exceedingly. Errors like that happen all the time.
In fact, I used the same methods to expose two other child-pornography sites on the dark net. One of them was Elysium, whose trail the Federal Criminal Police Office of Germany picked up on in June. I found their IP addresses around the same time as that of Childs Play.
Did you give them to the authorities?
No. A week later I saw on Twitter that someone else had posted the Elysium IP independently of me.
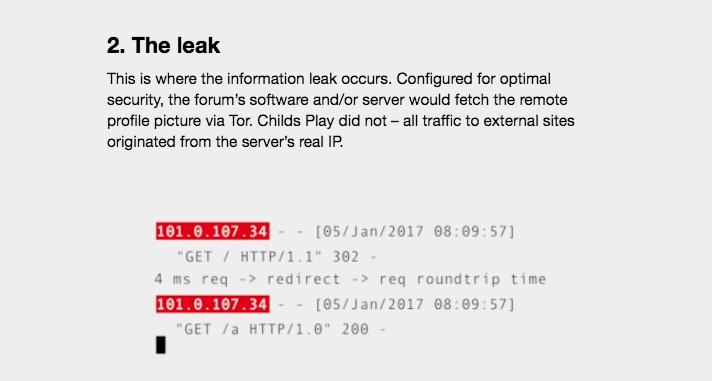
Back to Childs Play. How did you then proceed? IP addresses can be misleading on the dark net, especially since sites try to conceal their true locations.
Right. Not long after, I realized the IP address belonged to a server hosted by the Sydney-based company Digital Pacific. I tried out three different approaches to find out whether it was even a real IP address and not just a Tor exit node, a VPN or a proxy server.
You’re talking about the three common methods of concealing an IP address to surf the web anonymously: the Tor network, which directs communication across several nodes; a virtual private network (VPN), which replaces the actual IP through a virtual network; and a proxy server, which serves as an additional point of intersection between two servers.
Exactly. I had to rule out these three different methods. For the first test, I rented my own server through Digital Pacific. Then I measured the connection duration between the Childs Play server and my own server through Digital Pacific. When loading a site through the Tor network, it takes at least 250 milliseconds before your query reaches the server of the site and displays the site contents on your browser. That’s because traffic through the Tor network travels through multiple nodes to conceal the locations of the sender and receiver. But the time I measured for establishing a connection was less. It looked like servers were sitting right next to each other, allowing me to rule out the first method: The IP wasn’t a Tor node.
And the second method?
For this I had to test whether the IP belonged to a VPN or a proxy server, or whether the server was possibly being subleased to somebody else. So I analyzed the “time to live” values, which in essence show how many intermediary stops a data packet passes through. In this case, my measurements revealed that there were a maximum of two intermediary stops and that it’s possible that my server was communicating directly with the server that I suspected was the one Childs Play was using.
The third and last step, however, was the most revealing one: I analyzed the data packet sizes. When connected through a VPN, the normal sizes on a local computer network exceed the maximum transmission unit through a VPN. On the Childs Play server, I was able to see how larger packets were split up into smaller fragments—a clear indicator of a local internet connection—ruling out a VPN or proxy server. I knew this was the child-pornography platform’s real IP.
“Child pornography isn’t a problem specific to the dark net. Even on the normal internet there are huge offerings for this kind of content—and often only a Google search away.”
Some people assume that the dark net is a safe haven for the child-pornography scene. You’ve spent years conducting research on the scene in both the dark net and the “normal” internet. What are your thoughts?
The dark net in general and Tor more specifically truly do offer an arena for these people to be ten or one hundred times more difficult to find than on the normal internet. They simply have to download the Tor browser. But child-pornographic material and perpetrators who set up meetings to sexually abuse children aren’t problems specific to the dark net. Even on the normal internet there’s a lot of this kind of material, and even there the police have difficulties. My previous work on the people who download child porno revealed that there are huge offerings for sexually abusive material on the normal Internet.
Where does such content exist on the “normal” internet?
That’s the sad thing: Everywhere. On YouTube, Pastebin, in Facebook groups, in discussions on Reddit, on Twitter. And it’s just a Google search away. While conducting my research, I found out that most child-pornography users access such content via search engines. That applies at least to those people who are “only” consumers. In other words: those who don’t produce or distribute. Sadly, these people often fall off investigators’ radars—there are just too many of them. There are tens of thousands of people who are active at any given moment and scour the web for it. It’s unlikely that they’d get caught because of a download.
Then why do these people even still go to dark net sites like Childs Play or Elysium when they’re relatively safe on the normal internet?
Because of availability. On dark net forums there’s a lot more material bundled in one place. Plus it’s more structured and easier to search through. But there’s a difference in terms of security when they dive from the clearnet to the dark net: When a user who isn’t tech-savvy or who doesn’t have any form of opsec decides to go into the dark net, he automatically enters a circle that’s most likely monitored by the police. In other words, they go from a place that’s relatively safe to one that authorities scan and that’s possibly already been infiltrated.
“One can’t forget that a lot of damage was done during this time: Material was shared, new productions were made, and perpetrators planned out the rape of children.”
So Tor can be understood as not just a tool for criminals, but also as a means for law enforcement agencies to more effectively investigate crime circles?
You could definitely say that. But like I said, that only really applies to users who have little technological skills, such as those who use their old email addresses or nicknames on the normal internet for their dark net accounts.
But those who are more tech-savvy naturally benefit more from Tor technology. But even they stand in the crosshairs of police investigations. Most people at some point make a careless mistake that leads to their exposure. That’s why the former Childs Play admins are now behind bars. Ultimately, all these sites are doomed to fail from the start. It’s only a matter of time before someone comes up with an innovative investigation technique or uses an exploit that bores through your fortified walls—and that’s it. You’re done.
What was it like for you when you found out that the Australian police was running the Childs Play forum?
It was difficult for me to accept that that could be true. Especially when I found out that the police themselves had shared abusive material so that they wouldn’t seem suspicious. But from a technical point of view, I knew that there are hardly any other methods available to effectively investigate things like this.
The police ran the child-pornography platform for a total of 11 months. They downplayed the criticism, claiming the time was necessary to investigate the perpetrators. In 2015 you used other methods to expose tens of thousands of users who procured such content online. What’s your assessment of the time spent for this investigation method?
Whether eleven months was justifiable or not really depends on how many perpetrators they were able to lock up behind bars. If it was only ten, then I’d say the operation failed. One can’t forget that a lot of damage was done during this time: Material was shared, new productions were made and perpetrators planned out the rape of children.
And if the police were to catch 100 or 200 people?
That would be a great result. But they could have an average outcome, somewhere between 10 and 100, and the police could still claim that they used the time meaningfully, because they were able to refine their investigation techniques to make their next operation even more effective. It’s incredibly difficult to paint operations with a broad brush.
We’ll never find out whether the police already had the information necessary for an arrest or criminal charge after just five months or even two weeks. We’d need an independent and, ideally, international organization that could go back and audit the process and draw the right conclusions.
I don’t say that merely with criticism of the police. Such an evaluation would also help them to independently validate and optimize their methods. But I doubt that will happen. The police just don’t often like to show their own cards.