A Roundtable of Hackers Dissects ‘Mr. Robot’ Season 3 Episode 4: ‘Metadata’
Credit to Author: Yael Grauer| Date: Fri, 03 Nov 2017 15:30:00 +0000
The hacks continued on the fourth episode of Mr. Robot’s third season, giving our group of technologists a chance to discuss metadata, voice protectors, bug detection, IP tracking, Tomcat, Apache Struts, and more. (The chat transcript has been edited for brevity and clarity.) This week’s team of experts include:
- Bill Budington: a long time activist, programmer, and cryptography enthusiast, and a security engineer and technologist at the Electronic Frontier Foundation.
- Jen Helsby: SecureDrop lead developer at Freedom of the Press Foundation.
- Jason Hernandez: a technologist who studies surveillance and works in IT, and is the tech editor for North Star Post.
- Zachary Julian: a Senior Security Analyst at Bishop Fox, a security consulting firm.
- Micah Lee: a technologist with a focus on operational security, source protection, privacy, and cryptography, as well as a journalist at The Intercept.
- Freddy Martinez: a technologist working on whistleblowing technologies. He serves as a Director for the Chicago-based Lucy Parsons Labs.
- Matt Mitchell: a hacker who leads cryptoharlem, which aims to teach basic cryptographic tools in the inner city. He also trains newsroom journalists (at Global Journalist Security), activists & human rights defenders in digital & operational security.
Yael: In the beginning when Elliot said he was looking at metadata, it looked like he was just poking through Darlene’s trash and mailbox.
Micah: That was a nod to dumpster diving, something that I feel like used to be way more emphasized among hackers back in the day.
Yael: I feel like it’s more useful for, say, doxing.
Micah: I read stories from the 90s about people dumpster diving comprehensive technical manuals from the phone company, which helped them learn how to remotely control phone networks. And also people used to write their passwords down way more often, and people used to print out secret documents to read instead of just reading them on their computers.
Freddy: I feel like we haven’t made a lot of progress on that front.
Yael: I don’t know what Elliot would get from Darlene’s trash/mail though. Like she would probably get rid of (as in, burn) anything important.
Zachary: Also interesting that Elliot mentions EXIF data specifically when talking about metadata.
Bill: He’s right. Even if a site strips the metadata when actually posting a photo to the service, it will still get the raw photo when you uploaded it in the first place. That’s why you should use the Metadata Anonymization Toolkit if you really don’t want your photos to have metadata when you upload them. (I know it’s deprecated but…)
Jen: Download now at https://mat.boum.org/!
Freddy: I thought you could disable it on the iPhone. I have actually tried to see metadata off my own posts and didn’t find anything.
Yael: But Facebook probably still knows the phone people signed up with.
Bill: Not if they used https://facebookcorewwwi.onion!
Micah: You can prevent photos you take on your phone from including your location, but I don’t believe there’s any other metadata you can restrict directly from iOS or Android.
Yael: At what point are people who are worried about Facebook having their location/phone data off of their pics better off just dropping Facebook?
Jen: If they strip metadata from uploaded images, use Tor, and don’t use the mobile apps, it’s fine to use Facebook.
Yael: Here’s a non-Facebook pro tip: When being surveilled by the FBI, make sure to use a voice protector!
Jen: Even Hillary knows that one.

Bill: I thought that was a nice touch. Commercial voice protectors are real.
Zachary: For those interested, Elliot is using an MNG-300.
Yael: Holy shit, that’s $365! Why not use a white noise generator?
Micah: I don’t know about voice protectors. Do they actually work, and prevent digital recording devices from picking up anything meaningful? Maybe I should get one and test it out.
Yael: I actually had seen that before when I was trying to get jury duty. They had these private conferences between lawyers/judges that we couldn’t hear unscrambled.
Matt: There are devices that emit electronic noise different frequencies and white noise crashing into brown noise, pink noise to mask sound. Only works like whispering works.
Micah: I did notice there was a different scene where Elliot and Darlene were talking about secret things without the voice protector, and Eliot’s phone buzzed because he had to go to work. His phone could have had malware without him knowing and be recording the conversation.
Yael: So moving onto the Red Wheelbarrow meetup, I don’t want to gloss over Cooking Tips With Irving. I want to try ribs with two tablespoons dry rub to one cup apple cider vinegar. Maybe beer.
Zach: I thought it was cool that Angela talks about SDRs being second nature. SDR = surveillance detection route.
Yael: They talked about that in season 1, I think. So about these shipping delays, I went to http://www.e-corp-usa.com/cp/directory/shipping/1088989/ and tried to guess Elliot’s password, but it didn’t work. It was a real site, though. Oh, did anyone want to talk about him searching his house for bugs?
Bill: “I had to be sure.” Yeah, I saw a ripped up mattress, like he tore through everything apparently.
Micah: I don’t think he could actually be sure just by ripping apart his room and looking for bugs. It’s really hard to 100% confirm that a room is bug-free. The best you can do is confirm that it doesn’t have any of the types of bugs you’ve searched for.
Matt: Searching your house for bugs doesn’t work well in the real world since you can only electronically detect bugs that send data with spectrum 900mhz, 1ghz-7ghz .
Bill: He could have used a bug detector. Not sure how reliable they are, probably only for certain types of bugs, but they would probably do a better job than just ripping everything apart.
Micah: Some bugs transmit constantly, so you can look for their signals. But some just record to a disk and don’t transmit most of the time or at all. Some pull power, which you can look for, but some just use batteries.
Freddy: Yeah totally, especially with the size of some bugs. The exploit he found was a monitor exploit. Some of that stuff is very hard. I know police departments spend like 100K on doing countersurveillance on their networks to find bugs.
Matt: I have a bunch of these detectors and to cover that much band is expensive and you still won’t find devices that are designed to record to itself and be retrieved.
Micah: Doing bug searches doesn’t make you sure there aren’t bugs, it just raises your confidence that there aren’t. Sort of like scanning your computer for malware—if the malware is good, you won’t find it.
Matt: Leads to false sense of ease. And you need to keep checking to be sure.
Yael: Do you think the FBI/Darlene have bugs that Elliot doesn’t know about?
Micah: I doubt it. But it’s possible, so sometimes it’s safer to just take a walk to have a sensitive conversation.
Bill: Wait until next week to find out on the next exciting episode of MR. ROBOT.
Yael: Okay, so someone mentioned what Elliot had on Ecorp. What does he know beyond that Tyrell and Angela might be involved?
Jason: Elliot could have just tipped the FBI off to the plan for Phase 2 and that might have allowed the FBI/Ecorp to disrupt it.
Matt: He has no clue what’s going on. What he has on Ecorp is some random Tomcat research. Also, Elliot has these Apache Struts vulnerabilities, and security bulletin s2-016.
Micah: Ha, you can sign up for an ecoin account at https://e-coin.com/. Darlene seemed to think he had enough dirt to report them to the FBI and be done with it.
Jason: Tomcat is a server used to run Java-based web applications. Very common in enterprise software.
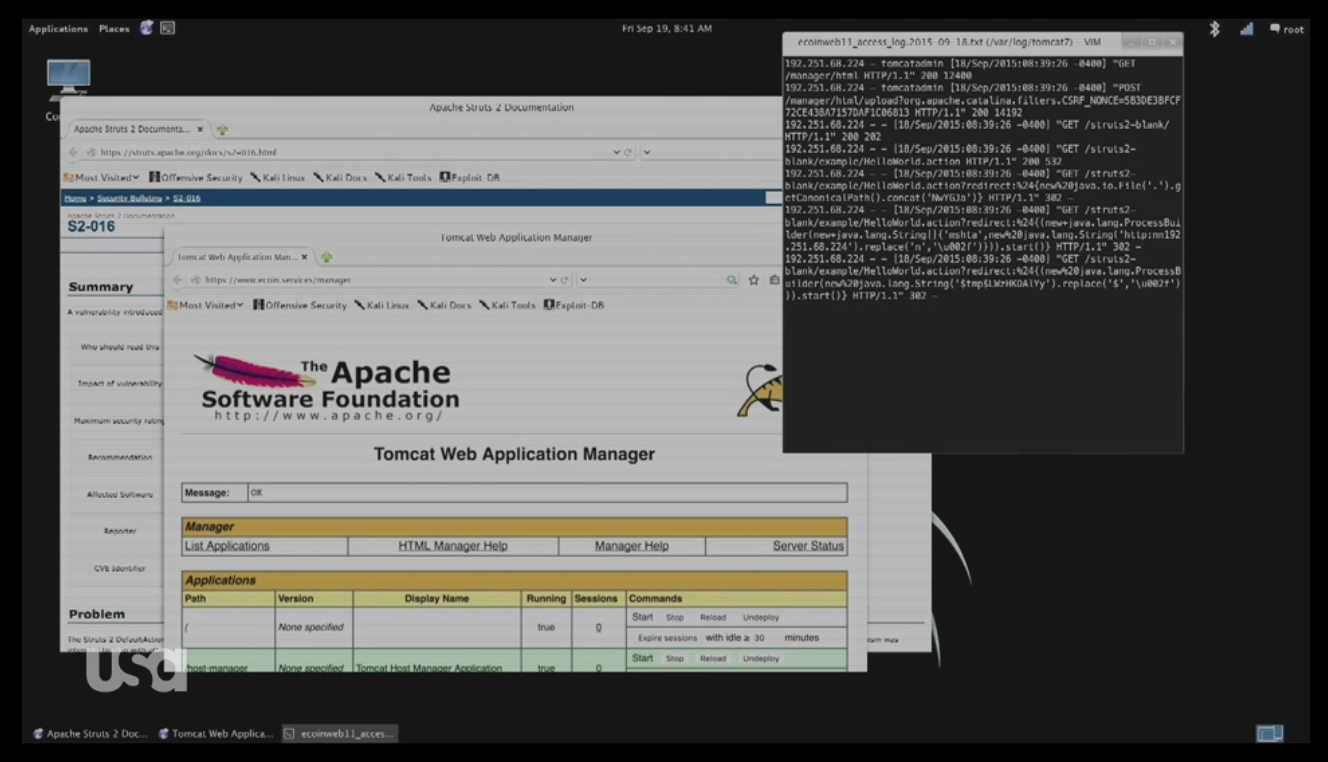
Zachary: Elliott says, “I’ve been monitoring traffic at Ecorp, and that lead me to an unpatched website,” while viewing some Apache Tomcat access logs. If you look at the Tomcat logs, there are references to Apache Struts. This is likely a reference to the recent Equifax breach which was blamed on a Struts vulnerability. Browsing to the IP address in the access logs (192.251.68.224) takes you to https://y8agrfx3.bxjyb2jvda.net, which appears to be a Dark Army member’s home directory in Ubuntu Kylin.
Jason: I also see that the IP is in the same subnet as last episode’s baby cam.
Yael: OH YEAH the baby cam! Poor Tyrell!
Matt: Yeah that’s not gonna end well.
Zachary: Yeah, he’s gonna be pissed when they fill him in.
Yael: If they fill him in. They may just kill him.
Freddy: Yeah, totally. “My wife and son and I will go to the Ukraine; they don’t extradite to the US…”
Yael: So should we talk about the FBI raid?

Matt: It’s very The Matrix, like when Trinity gets busted by the cops.
Yael: Why is he getting arrested for posting a video? Where are all of our free speech absolutists?
Jason: Conspiracy to commit cyberterrorism.
Matt: Well, last episode they said they were making F Society terrorist videos.
Yael: Sounds like a trumped-up charge 😉 We need to find a lawyer to see if it’s actually a “terrorist video” or just raucous free speech. Why didn’t he use Tor or a VPN?
Jason: I think he’s under orders from the Dark Army to take a fall as an F-Society member.
Freddy: Definitely under orders to take a fall. They didn’t use a VPN or Tor and connected to Vimeo directly to upload the video. Pretty easy to find.
Jason: The revolution will be webcast on Vimeo, apparently.
Yael: There’s actually a real F Society Vimeo account: https://vimeo.com/wearefsociety.
Micah: I think the FBI’s explanation for how he got caught was spot on. They sent a court order to Vimeo for the IP address access logs that accessed that account. One of those IP addresses was that guy’s home IP, which led to his address. But I also agree with Dom that it seems shady that he logged in using his home IP. That’s such a rookie mistake.
Freddy: I liked how the F Society member didn’t talk to the FBI. Only talk to the FBI without a lawyer if you’re George Papadopoulos. JK, don’t talk to the FBI.