KRACK For Dummies
Credit to Author: Lucian Constantin| Date: Mon, 16 Oct 2017 17:23:37 +0000
For years security experts have advised users to only connect to password-protected wireless networks to prevent traffic snooping attempts that could expose their sensitive data. Due to new vulnerabilities announced today in WPA2, the most widely used Wi-Fi security protocol, virtually all devices are now vulnerable to such attacks.
The flaws, discovered by University of Leuven researcher Mathy Vanhoef, allow attackers in the vicinity of a legitimate WPA2-protected wireless network—like the one you have at home, at your favorite coffee shop or in your company—to intercept and decrypt traffic from connecting devices. In some cases it’s even possible to inject malicious data into the traffic.
The finding quickly became international news, but it’s worth examining how it works and whether you’re likely to be vulnerable.
How does the attack work?
Hackers would first need to set up a rogue access point that mimics a legitimate one and force nearby clients to connect to it. With this setup, they could then exploit the flaws found by Vanhoef to launch what the researcher calls a key reinstallation attack (KRACK).
The attack targets the handshake and key negotiation between connecting devices and access points and forces clients to reuse an older session key. The encryption provided by the WPA2 standard is weakened as a result.
It’s worth keeping in mind that in order to pull off such an attack, a hacker would need to be in your device’s Wi-Fi range and impersonate a network that your device already trusts and would attempt to connect to. Secondly, the attack does not compromise a Wi-Fi network’s password, so a hacker won’t be able to clandestinely join your home network.
What hackers could do through KRACK is hijack the wireless traffic from your device and decrypt it, fully or partially depending on various factors. This could expose sensitive information such as passwords, messages, emails, and files if they are transmitted in plain text without an additional layer of encryption such as HTTPS.
Who is affected?
This is a protocol-level issue, so the vulnerabilities behind KRACK are not limited to specific implementations. If a device supports Wi-Fi, it is likely to be vulnerable to one of the attack’s variants. The flaws affect both WPA2-Personal and WPA2-Enterprise, as well as older wireless security standards such as WPA that are considered insecure and shouldn’t be used anyway.
“During our initial research, we discovered ourselves that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys, and others, are all affected by some variant of the attacks,” Vanhoef said on a website that describes his findings in more detail.
That said, there are differences between KRACK’s impact on various operating systems. For some systems it’s possible to decrypt a considerable number of data packets, but not all of them.
The attack is particularly catastrophic on Linux and Android versions 6.0 and higher due to an additional implementation issue in the software package that handles WPA wireless connections. On these systems it’s trivial for attackers to both decrypt and manipulate Wi-Fi traffic.
Vanhoef estimates that over 40 percent of Android devices out there are impacted by this more severe version of the attack. And unfortunately, due to the version and vendor fragmentation in the Android ecosystem, it could be months until many of these devices receive patches. Some of them might remain vulnerable indefinitely because they’re not supported by their manufacturers anymore.
Windows and iOS are not vulnerable to the basic session key reinstallation attack—ironically thanks to non-standard Wi-Fi implementations. However, these systems can be vulnerable to a similar attack against network group keys or can be attacked through a vulnerable access point.
And this is another important aspect: Both wireless access points and clients are vulnerable, but most attacks are likely to be directed at clients. However, some devices can be both an access point and a client at the same time. For example, a wireless repeater is a device that connects to a wireless network, so it acts as a client, and then relays the signal to other clients, so it also acts as an access point.
The good news is that patches will not break compatibility, so a patched client that’s no longer vulnerable will be able to talk to an unpatched access point and the other way around.
This is bad, but don’t panic
The best thing you can do is patch your devices—laptops, smartphones, routers—as soon as patches become available. This will be harder for some devices than others. For example, router firmware updates typically require users to check their device manufacturer’s websites for updates, download the updates to their computers and then upload them to their routers via a web-based interface or an application.
“This issue can be resolved through straightforward software updates, and the Wi-Fi industry, including major platform providers, has already started deploying patches to Wi-Fi users,” the Wi-Fi Alliance, the industry organization that certifies Wi-Fi-compliant products, said in a statement. “Users can expect all their Wi-Fi devices, whether patched or unpatched, to continue working well together.”
The organization has shared information about these vulnerabilities with vendors and now checks for the flaws as part of its Wi-Fi certification process, which means future Wi-Fi-compliant products should be patched.
The CERT Coordination Center at Carnegie Mellon University, which supports the U.S. government’s Computer Emergency Readiness Team (US-CERT), published an advisory about this issue and maintains a list of affected hardware and software makers.
Until patches become available, there are some things you can do to protect your devices and information. For one, check that your home network uses WPA2 with AES encryption, not TKIP. Both encryption options are vulnerable to traffic decryption via KRACK, but AES is not vulnerable to packet injection, which could have more serious consequences, such as injecting malware into legitimate web pages.
Email and web traffic encrypted with TLS—like that to HTTPS-enabled websites—is theoretically protected against snooping because it adds an additional layer of encryption on top of what WPA2 provides.
There are ways for man-in-the-middle attackers to strip away HTTPS from websites and redirect users to unencrypted versions, but such attempts won’t work against well-configured servers. Browsers also come with a built-in list of popular websites for which only HTTPS connections are allowed. There are also browser extensions such as HTTPS Everywhere that always force HTTPS connections for a large number of websites and even allow users to define their own rules.
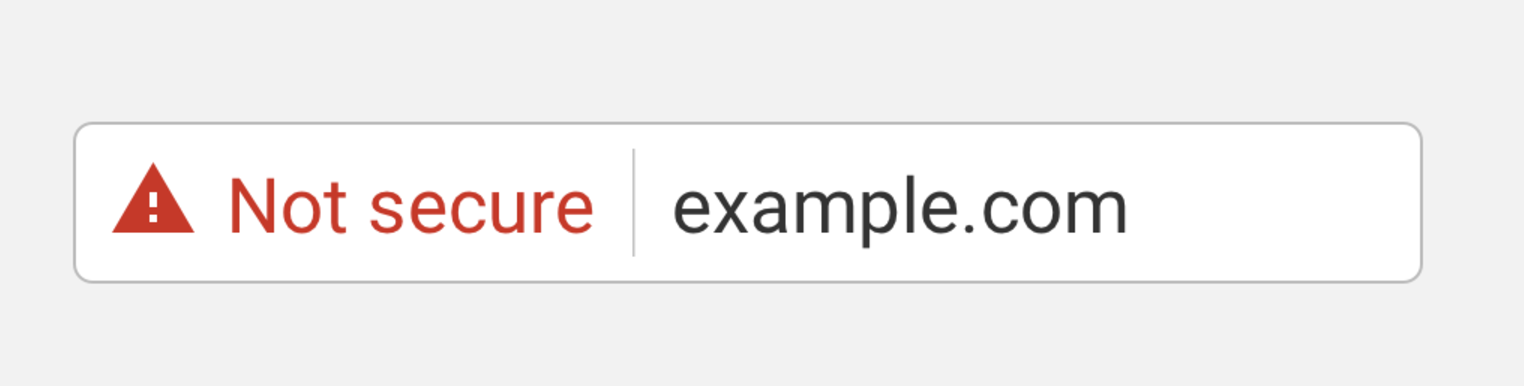
Google Chrome marks non-HTTPS web pages that contain sign in forms as “Not Secure” and Mozilla Firefox goes a step further and displays a warning when users attempt to enter information into such forms. These visual indicators could alert users about possible HTTPS stripping attempts.
Another good option for securing a computer’s entire network traffic—not just email or web—is to use a virtual private networking (VPN) solution. Companies provide such services for their employees and there are many consumer options out there too.
VPNs route all traffic through an encrypted tunnel and their use is already recommended when connected to untrusted Wi-Fi networks. Users concerned about possible KRACK attacks could turn on their VPN when using Wi-Fi at all times, regardless of whether they’re at home, at work or at their favorite restaurant.
This attack “can’t defeat SSL/TLS or VPNs,” cybersecurity expert Robert Graham, said in a blog post. “Thus, if you feel your laptop is safe surfing the public WiFi at airports, then your laptop is still safe from this attack.”
Of course, the type of devices vulnerable to KRACK extends well beyond laptops and smartphones. Many internet-of-things devices connect over Wi-Fi, transmit sensitive data in the clear on local networks and don’t support VPNs. There’s no easy solution for protecting these devices in the absence of patches, so users should put pressure on device manufacturers to provide fixes for the KRACK attacks.
“Your home network is vulnerable,” Graham said. “Many devices will be using SSL/TLS, so are fine, like your Amazon Echo, which you can continue to use without worrying about this attack. Other devices, like your Philips lightbulbs, may not be so protected.”
He recommends that users monitor how long it takes for their device manufacturers to respond to this attack with patches, then replace the devices from vendors that took too long. The idea behind this is that all software and hardware has flaws, but what differentiates vendors is the way in which they respond to security incidents.
“We cannot stress enough that home users—especially those in densely populated areas—absolutely must monitor for patches for their existing Wi-Fi equipment or migrate to new equipment that does not have this vulnerability,” said Bob Rudis, chief data scientist at vulnerability intelligence firm Rapid7.