Trump’s Dumps: ‘Making Dumps Great Again’
Credit to Author: BrianKrebs| Date: Fri, 26 May 2017 04:45:24 +0000
It’s not uncommon for crooks who peddle stolen credit cards to seize on iconic American figures of wealth and power in the digital advertisements for their shops that run incessantly on various cybercrime forums. Exhibit A: McDumpals, a hugely popular carding site that borrows the Ronald McDonald character from McDonald’s and caters to bulk buyers. Exhibit B: Uncle Sam’s dumps shop, which wants YOU! to buy American. Today, we’ll look at an up-and-coming stolen credit card shop called Trump’s-Dumps, which invokes the 45th president’s likeness and promises to make credit card fraud great again.

One reason thieves who sell stolen credit cards like to use popular American figures in their ads may be that a majority of their clients are people in the United States. Very often we’re talking about street gang members in the U.S. who use their purchased “dumps” — the data copied from the magnetic stripes of cards swiped through hacked point-of-sale systems — to make counterfeit copies of the cards. They then use the counterfeit cards in big-box stores to buy merchandise that they can easily resell for cash, such as gift cards, Apple devices and gaming systems.
When most of your clientele are street thugs based in the United States, it helps to leverage a brand strongly associated with America because you gain instant brand recognition with your customers. Also, a great many of these card shops are run by Russians and hosted at networks based in Russia, and the abuse of trademarks closely tied to the U.S. economy is a not-so-subtle “screw you” to American consumers.
In some cases, the guys running these card shops are openly hostile to the United States. Loyal readers will recall the stolen credit card shop “Rescator” — which was the main source of cards stolen in the Target, Home Depot and Sally Beauty breaches (among others) — was tied to a Ukrainian man who authored a nationalistic, pro-Russian blog which railed against the United States and called for the collapse of the American economy.
In deconstructing the 2014 breach at Sally Beauty, I interviewed a former Sally Beauty corporate network administrator who said the customer credit cards being stolen with the help of card-stealing malware installed on Sally Beauty point-of-sale devices that phoned home to a domain called “anti-us-proxy-war[dot]com.”
Trump’s Dumps currently advertises more than 133,000 stolen credit and debit card dumps for sale. The prices range from just under $10 worth of Bitcoin to more than $40 in Bitcoin, depending on which bank issued the card, the cardholder’s geographic location, and whether the cards are tied to premium, prepaid, business or executive accounts.
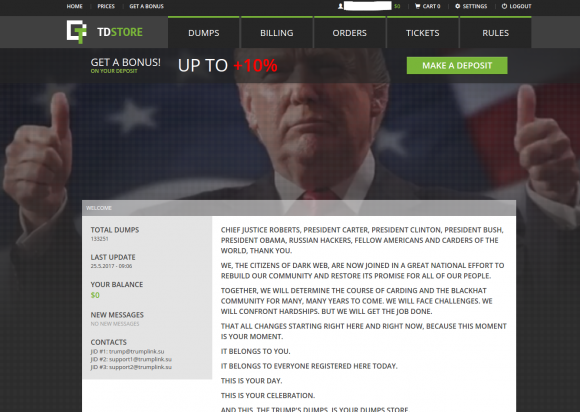
A “state of the dumps” address on Trump’s-Dumps.
Trump’s Dumps is currently hosted on a Russian server that caters to a handful of other high-profile carding shops, including the long-running “Fe-shop” and “Monopoly” dumps stores.
Sites like Trump’s Dumps can be taken offline — by forcing a domain name registrar to revoke the domain — but the people responsible for running this shop have already registered a slew of similar domains and no doubt have fresh bulletproof hosting standing by in case their primary domain is somehow seized.
Also, like many other modern carding sites this one has versions of itself running on the Dark Web — sites that are only accessible using Tor and are far more difficult to force offline.
The home page of Trump’s Dumps takes some literary license with splices of President Trump’s inaugural address (see the above screenshot for the full text):
“WE, THE CITIZENS OF DARK WEB, ARE NOW JOINED IN A GREAT NATIONAL EFFORT TO REBUILD OUR COMMUNITY AND RESTORE ITS PROMISE FOR ALL OF OUR PEOPLE.”
TOGETHER, WE WILL DETERMINE THE COURSE OF CARDING AND THE BLACKHAT COMMUNITY FOR MANY, MANY YEARS TO COME. WE WILL FACE CHALLENGES. WE WILL CONFRONT HARDSHIPS. BUT WE WILL GET THE JOB DONE.”
The U.S. Secret Service, which has the dual role of protecting the President and busting up counterfeiters (including credit card theft rings), declined to comment for this story.
WHO RUNS TRUMP’S DUMPS?
For now, I’m disinclined to believe much about a dox supposedly listing the Trump’s Dumps administrator’s various contacts that was released by one of his competitors in the cybercrime underground. However, there are some interesting clues that tie Trump’s Dumps to a series of hacking attacks on e-commerce providers over the past year. Those clues suggest the criminals behind Trump’s Dumps are massively into stealing credit card data that fuels both card-present and online fraud.
In the “contacts” section of Trump’s Dumps the proprietors list three Jabber instant messenger IDs. All of them end in @trumplink[dot]su. That site is not currently active, but Web site registration records for the domain show it is tied to the email address “rudneva-y@mail.ua.”
A reverse WHOIS website registration record search ordered from domaintools.com [full disclosure: Domaintools is an advertiser on this blog] shows that this email address is associated with at least 15 other domains. Most of those domains appear to have been registered to look like legitimate Javascript calls that many e-commerce sites routinely make to process transactions, such as “js-link[dot]su,” “js-stat[dot]su,” and “js-mod[dot]su” (the full list is in this PDF).
A Google search on those domains produces a report from security firm RiskIQ, which explains how those domains featured prominently in a series of hacking campaigns against e-commerce websites dating back to March 2016. According to RiskIQ, the attacks targeted online stores running outdated and unpatched versions of shopping cart software from Magento, Powerfront and OpenCart.
These same domains showed up in an attack last October when it was revealed that hackers had compromised the Web site for the U.S. Senate GOP Senatorial Committee, among more than 5,900 other sites that accept credit cards. The intruders tinkered with the GOP Committee site’s HTML code to insert calls to domains like “jquery-cloud[dot]net” to hide the fact that they were stealing all credit card data that donors submitted via the Web site.