ATM ‘Shimmers’ Target Chip-Based Cards
Several readers have called attention to warnings coming out of Canada about a supposedly new form of ATM skimming called “shimming” that targets chip-based credit and debit cards. Shimming attacks are not new (KrebsOnSecurity first wrote about them in August 2015), but they are likely to become more common as a greater number of banks in the United States shift to issuing chip-based cards. Here’s a brief primer on shimming attacks, and why they succeed.
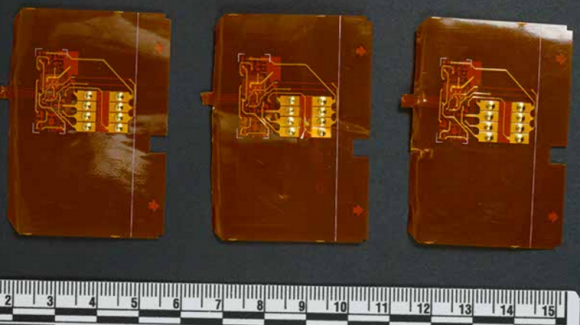
Several shimmers recently found inside Canadian ATMs. Source: RCMP.
Most skimming devices made to steal credit card data do so by recording the data stored in plain text on the magnetic stripe on the backs of cards. A shimmer, on the other hand, is so named because it acts a shim that sits between the chip on the card and the chip reader in the ATM — recording the data on the chip as it is read by the ATM.
Data collected by shimmers cannot be used to fabricate a chip-based card, but it could be used to clone a magnetic stripe card. Although the data that is typically stored on a card’s magnetic stripe is replicated inside the chip on chip-enabled cards, the chip contains an additional security components not found on a magnetic stripe.
One of those is a component known as an integrated circuit card verification value or “iCVV” for short — also known as a “dynamic CVV.” The iCVV differs from the card verification value (CVV) stored on the physical magnetic stripe, and protects against the copying of magnetic-stripe data from the chip and using that data to create counterfeit magnetic stripe cards.
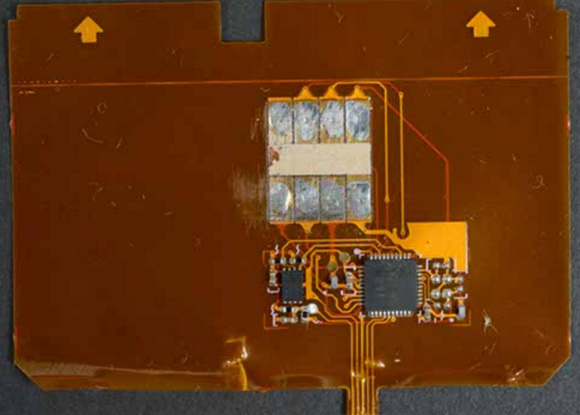
A close-up of a shimmer found on a Canadian ATM. Source: RCMP.
The reason shimmers exist at all is that some banks have apparently not correctly implemented the chip card standard, known as EMV (short for Europay, Mastercard and Visa).
“The only way for this attack to be successful is if a [bank card] issuer neglects to check the CVV when authorizing a transaction,” ATM giant NCR Corp. wrote in a 2016 alert to customers. “All issuers MUST make these basic checks to prevent this category of fraud. Card Shimming is not a vulnerability with a chip card, nor with an ATM, and therefore it is not necessary to add protection mechanisms against this form of attack to the ATM.”
Here’s a look at the shimmer I wrote about back in August 2015, which was discovered inside an ATM in Mexico.
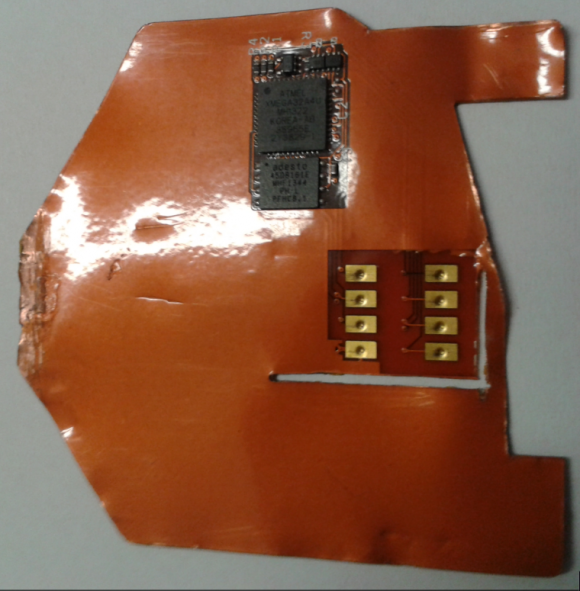
This card ‘shimming’ device is made to read chip-enabled cards and can be inserted directly into the ATM’s card acceptance slot.
This shimming device was removed from an ATM in Europe in 2015:
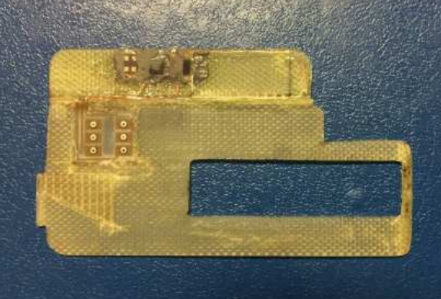
An ATM shimmer. Source: European ATM Security Team (EAST).
Once you understand how stealthy these ATM fraud devices are, it’s difficult to use a cash machine without wondering whether the thing is already hacked. The truth is most of us probably have a better chance of getting physically mugged after withdrawing cash than encountering a skimmer in real life. However, here are a few steps we can all take to minimize the success of skimmer gangs.
-Cover the PIN pad while you enter your PIN.
-Keep your wits about you when you’re at the ATM, and avoid dodgy-looking and standalone cash machines in low-lit areas, if possible.
-Stick to ATMs that are physically installed in a bank. Stand-alone ATMs are usually easier for thieves to hack into.
-Be especially vigilant when withdrawing cash on the weekends; thieves tend to install skimming devices on a weekend — when they know the bank won’t be open again for more than 24 hours.
-Keep a close eye on your bank statements, and dispute any unauthorized charges or withdrawals immediately.
If you liked this piece and want to learn more about skimming devices, check out my series All About Skimmers.