RPC Vulnerability Stands Out in a Field of 128 in April
Credit to Author: Christopher Budd| Date: Tue, 12 Apr 2022 17:45:37 +0000
You can almost think of the April 2022 Patch Tuesday release as having a bark that’s worse than its bite.
At first blush, this is a very large month in terms of numbers of vulnerabilities (CVEs) addressed: 128.
However, even though this is a heavy month in terms of quantity, it’s actually not as bad a month as one might expect.
That said, there’s one vulnerability that does stand out: CVE-2022-26809 RPC Runtime Library Remote Code Execution Vulnerability, a Critical-severity RPC vulnerability with no mitigating factors, low attack complexity, a greater-than-average likelihood of exploitation, and impact on all versions of Windows from Windows 7 onwards. Even more unnerving for infosecurity veterans, RPC was the vulnerable component behind the crippling Blaster worm attacks in 2003.
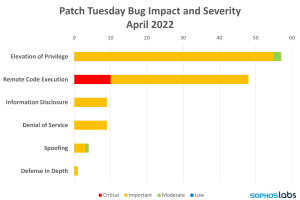
Aside from that eye-catching vulnerability, the rest of this large release is more about quantity than severity. Only nine of the remaining vulnerabilities are rated “Critical,” three are rated “Moderate,” and the remaining vulnerabilities are rated as “Important.” Though counted in the tally of 128, one CVE this month is technically a Defense-in-Depth release rather than a true vulnerability according to Microsoft’s classification scheme.
There are no Critical-class vulnerabilities that are publicly disclosed or exploited at time of release.
In fact, there is only vulnerability listed as exploited, CVE-2022-24521 Windows Common Log File System Driver Elevation of Privilege Vulnerability, and only one vulnerability, CVE-2022-26904 Windows User Profile Service Elevation of Privilege Vulnerability, publicly disclosed. Both are rated “Important.”
Even in terms of likelihood of exploitability, this month is relatively light. Only eleven of the 128 are listed as “Exploitation More Likely,” and aside from the RPC vulnerability, only two others of these are rated “Critical”: CVE-2022-24491 Windows Network File System Remote Code Execution Vulnerability and CVE-2022-24497 Windows Network File System Remote Code Execution Vulnerability.
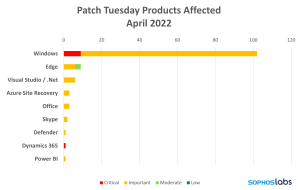
This month’s release covers a range of products. The overwhelming majority of patches are for Microsoft Windows and its components. These include the most notable vulnerabilities this month. Other products affected include Microsoft Edge, .NET and Visual Studio, Defender, Office, and a handful of lesser-known and less-deployed products.
You can find a complete breakdown of the vulnerabilities by severity and impact, product, and exploitability at the end in the Appendix.
Below we highlight some of the most notable vulnerabilities to be considered in April’s risk assessment and deployment prioritization.
Notable Vulnerabilities
RPC, SMB, and NFS
Five vulnerabilities — half of this month’s critical vulnerabilities — affect networking protocols and capabilities, specifically RPC, SMB, and NFS.
Of the four vulnerabilities affecting RPC, the vulnerability described above (CVE-2022-26809) is rated as critical, with no mitigating factors listed and “Exploitation More Likely.” These points plus RPC’s role in past attacks like Blaster mean this vulnerability should also have a high prioritization. The remaining three RPC vulnerabilities also have mitigating factors that would likely make successful attacks more difficult, rating them as “Important” in severity.
This month there are six RCE vulnerabilities affecting SMB. Two (CVE-2022-24500 and CVE-2022-24541) are rated as “Critical,” but Microsoft notes “For vulnerability to be exploited, a user would need to access a malicious SMB server to retrieve some data as part of an OS API call.” This would seem to imply some level of mitigation, but the critical rating and SMBs role in major security events like EternalBlue means these vulnerabilities should be highly prioritized. The four non-Critical SMB vulnerabilities have specific requirements that would appear to make successful attacks against these more difficult, which is why they’re rated as “Important”.
The two vulnerabilities affecting NFS (CVE-2022-24491 and CVE-2022-24497) are rated “Critical” and also “Exploitation More Likely.” However, the vulnerable component is not installed and enabled on Windows by default. This means these critical vulnerabilities only affect Windows Server “when the server administrator uses the Add Roles and Features Wizard to add the Server NFS role service.” In short, if you run NFS on Windows Server, this is a high-priority patch. But if you don’t, you can skip these patches.
Hyper-V
Three of this month’s critical vulnerabilities affect Windows Hyper-V (CVE-2022-22008, CVE-2022-23257 and CVE-2022-24537). There are an additional six “Important” vulnerabilities affecting Hyper-V.
CVE-2022-23257 is notable because a successful attack would require an attacker to load and run a specially crafted application on a Hyper-V guest.
CVE-2022-24537 is notable because Microsoft notes “To exploit this vulnerability, an attacker would need to trick a user into executing a specially crafted script within a Hyper-V guest instance running on a nested Hyper-V host instance.” While this is rated Critical in severity, it would seem to require a very specific scenario for exploitation.
Microsoft Dynamics 365 (on-premises)
The remaining critical vulnerability this month affects Microsoft Dynamics 365 (on-premises). Microsoft patched a critical vulnerability in this particular product in February 2022 as well. To exploit this vulnerability, an attacker would need to be an authenticated user who could run a specially crafted trusted solution package to execute arbitrary SQL commands. Once they had accomplished that, the attacker could escalate and execute commands as db_owner within their Dynamics 356 database.
LDAP
There are two vulnerabilities affecting LDAP this month. One of these CVE-2022-26919 Windows LDAP Remote Code Execution Vulnerability is rated as critical. On the one hand, this vulnerability is remotely exploitable over the network by a standard user who has been authenticated in the domain. On the other hand, Microsoft notes that this has “high complexity” for any attack and that an attack is not possible unless the default setting for MaxReceiveBuffer has been changed. However, as we discuss below, there are a number of non-critical vulnerabilities affecting Active Directory as well, so it makes sense to prioritize this along with those.
Active Directory
This month there are two Important-rated remote code execution (RCE) vulnerabilities affecting Active Directory (CVE-2022-26814 and CVE-2022-26817). Both of these are race condition vulnerabilities and both require privileges to query the Domain Name Service (DNS) on the vulnerable system. These are important mitigating factors for the vulnerabilities. A successful attack could enable code execution in the Active Directory service. So, while there are notable mitigating factors, an attacker’s ability to potentially compromise an organization’s active directory and create privileged accounts could allow these vulnerabilities to be used as part of an attacker’s lateral movement on the network if compromised.
DNS
This month there are 16 vulnerabilities affecting DNS. All but two of these are RCEs. Of the others, one (CVE-2022-26816) is a denial of service (DoS) vulnerability and the other (CVE-2022-26829) is an elevation of privilege (EoP) vulnerability. Several, but not all, of the RCEs have a mitigating factor: An attacker would need to be a member of the DNS Admins group to carry out a successful attack. Given the number of vulnerabilities being addressed and the importance of DNS, in this month’s release it makes sense to make the bundle of DNS patches a priority for your risk assessment and deployment.
Print Spooler
With the PrintNightmare situation over the summer of 2021, this is a component that has been under scrutiny and attack and thus cause for concern. This month’s patches for Print Spooler mirror the tenor of this month’s overall release: heavy in quantity but less severe than might be expected.
In total there are 15 vulnerabilities in the Print Spooler being addressed. However, all of these are rated “Important,” all are EoPs, none are publicly disclosed, none are currently under exploit, and all are rated “Exploitability Less Likely.”
Because of the number of vulnerabilities in this component it makes sense to give some priority to these updates, but these are clearly less urgent for your prioritization for risk assessment and deployment.
Sophos protection
As you can do every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. (The exceptions this month, as noted above, are the 11 patches handled via the Microsoft Store.) Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.
Appendix
Vulnerability Severity and Impact
Below is a breakdown of the vulnerabilities by impact and severity.
Remote code execution (RCE)
Critical:
- CVE-2022-23259 Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
- CVE-2022-26809 RPC Runtime Library Remote Code Execution Vulnerability
- CVE-2022-22008 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-23257 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-24537 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-24491 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-24497 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-24500 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24541 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-26919 Windows LDAP Remote Code Execution Vulnerability
Important:
- CVE-2022-26814 Active Directory Domain Services Remote Code Execution Vulnerability
- CVE-2022-26817 Active Directory Domain Services Remote Code Execution Vulnerability
- CVE-2022-26898 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24532 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24475 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
- CVE-2022-26901 Microsoft Excel Remote Code Execution Vulnerability
- CVE-2022-24533 Remote Desktop Protocol Remote Code Execution Vulnerability
- CVE-2022-24492 Remote Procedure Call Runtime Remote Code Execution Vulnerability
- CVE-2022-24528 Remote Procedure Call Runtime Remote Code Execution Vulnerability
- CVE-2022-24495 Windows Direct Show – Remote Code Execution Vulnerability
- CVE-2022-26829 Windows DNS Elevation of Privilege Vulnerability
- CVE-2022-24536 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26811 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26812 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26813 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26815 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26818 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26819 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26820 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26821 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26822 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26823 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26824 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26825 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26826 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26903 Windows Graphics Component Remote Code Execution Vulnerability
- CVE-2022-22009 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-24543 Windows Installer Remote Code Execution Vulnerability
- CVE-2022-24545 Windows Kerberos Remote Code Execution Vulnerability
- CVE-2022-24487 Windows Local Security Authority Subsystem Service Remote Code Execution Vulnerability
- CVE-2022-21983 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24485 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24534 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-26830 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24473 Microsoft Excel Remote Code Execution Vulnerability
- CVE-2022-26916 Windows Fax Compose Form Remote Code Execution Vulnerability
- CVE-2022-26917 Windows Fax Compose Form Remote Code Execution Vulnerability
- CVE-2022-26918 Windows Fax Compose Form Remote Code Execution Vulnerability
Elevation of privilege (EoP)
Important:
- CVE-2022-26896 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-26897 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24479 Connected User Experiences and Telemetry Elevation of Privilege Vulnerability
- CVE-2022-24496 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
- CVE-2022-26891 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26894 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26895 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26900 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26908 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26788 PowerShell Elevation of Privilege Vulnerability
- CVE-2022-24765 Uncontrolled search for the Git directory in Git for Windows
- CVE-2022-24513 Visual Studio Elevation of Privilege Vulnerability
- CVE-2022-24482 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24540 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24494 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2022-24549 Windows AppX Package Manager Elevation of Privilege Vulnerability
- CVE-2022-26828 Windows Bluetooth Driver Elevation of Privilege Vulnerability
- CVE-2022-24538 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-24489 Windows Cluster Shared Volume (CSV) Elevation of Privilege Vulnerability
- CVE-2022-24481 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24521 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24488 Windows Desktop Bridge Elevation of Privilege Vulnerability
- CVE-2022-24547 Windows Digital Media Receiver Elevation of Privilege Vulnerability
- CVE-2022-24546 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-24527 Windows Endpoint Configuration Manager Elevation of Privilege Vulnerability
- CVE-2022-26808 Windows File Explorer Elevation of Privilege Vulnerability
- CVE-2022-26810 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
- CVE-2022-26827 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
- CVE-2022-24499 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-24530 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-24486 Windows Kerberos Elevation of Privilege Vulnerability
- CVE-2022-24544 Windows Kerberos Elevation of Privilege Vulnerability
- CVE-2022-26786 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26787 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26789 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26790 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26791 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26792 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26793 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26794 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26795 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26796 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26797 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26798 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26801 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26802 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26803 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-24550 Windows Telephony Server Elevation of Privilege Vulnerability
- CVE-2022-26904 Windows User Profile Service Elevation of Privilege Vulnerability
- CVE-2022-24474 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-24542 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-26807 Windows Work Folder Service Elevation of Privilege Vulnerability
- CVE-2022-24767 GitHub: Git for Windows’ uninstaller vulnerable to DLL hijacking when run under the SYSTEM user account
- CVE-2022-26914 Win32k Elevation of Privilege Vulnerability
- CVE-2022-26921 Visual Studio Code Elevation of Privilege Vulnerability
Moderate:
- CVE-2022-26909 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26912 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
Denial of service (DoS) – Important
- CVE-2022-26831 LDAP Denial of Service Vulnerability
- CVE-2022-26832 Microsoft .NET Framework and ASP.NET Information Disclosure
- CVE-2022-24548 Microsoft Defender Denial of Service Vulnerability
- CVE-2022-24484 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-26784 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-26816 Windows DNS Server Denial of Service Vulnerability
- CVE-2022-23268 Windows Hyper-V Denial of Service Vulnerability
- CVE-2022-26915 Windows Secure Channel Denial of Service Vulnerability
- CVE-2022-26924 YARP Denial of Service Vulnerability
Information disclosure – Important
- CVE-2022-24493 Microsoft Local Security Authority Server (lsasrv) Information Disclosure Vulnerability
- CVE-2022-26911 Skype for Business Information Disclosure Vulnerability
- CVE-2022-24490 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-24539 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-26783 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-26785 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-24498 Windows iSCSI Target Service Information Disclosure
- CVE-2022-24483 Windows Kernel Information Disclosure Vulnerability
- CVE-2022-26920 Windows Graphics Component Information Disclosure Vulnerability
Spoofing:
Important
- CVE-2022-23292 Microsoft Power BI Spoofing Vulnerability
- CVE-2022-24472 Microsoft SharePoint Server Spoofing Vulnerability
- CVE-2022-26910 Skype for Business and Lync Spoofing Vulnerability
Moderate
- CVE-2022-24523 Microsoft Edge (Chromium-based) Spoofing Vulnerability
Defense in Depth – Important:
- CVE-2022-26907 Azure SDK for .NET Information Disclosure Vulnerability
Exploitability Indexes
Below are the vulnerabilities marked as “Exploitation more likely”. This month the Exploitability Indexes are identical for both latest and older software.
- CVE-2022-26809 RPC Runtime Library Remote Code Execution Vulnerability
- CVE-2022-24481 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24521 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24547 Windows Digital Media Receiver Elevation of Privilege Vulnerability
- CVE-2022-24546 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-24491 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-24497 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-26904 Windows User Profile Service Elevation of Privilege Vulnerability
- CVE-2022-24474 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-24542 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-26914 Win32k Elevation of Privilege Vulnerability
Products Affected
.NET and Visual Studio
- CVE-2022-26832 Microsoft .NET Framework and ASP.NET Information Disclosure
- CVE-2022-24765 Uncontrolled search for the Git directory in Git for Windows
- CVE-2022-24513 Visual Studio Elevation of Privilege Vulnerability
- CVE-2022-26907 Azure SDK for .NET Information Disclosure Vulnerability
- CVE-2022-24767 GitHub: Git for Windows’ uninstaller vulnerable to DLL hijacking when run under the SYSTEM user account
- CVE-2022-26921 Visual Studio Code Elevation of Privilege Vulnerability
- CVE-2022-26924 YARP Denial of Service Vulnerability
Azure Site Recovery
- CVE-2022-26896 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-26897 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-26898 Azure Site Recovery Remote Code Execution Vulnerability
Microsoft Defender
- CVE-2022-24548 Microsoft Defender Denial of Service Vulnerability
Microsoft Dynamics
- CVE-2022-23259 Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
Microsoft Edge
- CVE-2022-26891 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26894 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26895 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26900 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26908 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-26909 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
- CVE-2022-24475 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
- CVE-2022-24523 Microsoft Edge (Chromium-based) Spoofing Vulnerability
- CVE-2022-26912 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
Microsoft Office
- CVE-2022-26901 Microsoft Excel Remote Code Execution Vulnerability
- CVE-2022-24472 Microsoft SharePoint Server Spoofing Vulnerability
- CVE-2022-24473 Microsoft Excel Remote Code Execution Vulnerability
Microsoft Power BI
- CVE-2022-23292 Microsoft Power BI Spoofing Vulnerability
Microsoft Skype for Business
- CVE-2022-26910 Skype for Business and Lync Spoofing Vulnerability
- CVE-2022-26911 Skype for Business Information Disclosure Vulnerability
Microsoft Windows
- CVE-2022-26814 Active Directory Domain Services Remote Code Execution Vulnerability
- CVE-2022-26817 Active Directory Domain Services Remote Code Execution Vulnerability
- CVE-2022-24479 Connected User Experiences and Telemetry Elevation of Privilege Vulnerability
- CVE-2022-24532 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-26831 LDAP Denial of Service Vulnerability
- CVE-2022-24496 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
- CVE-2022-24493 Microsoft Local Security Authority Server (lsasrv) Information Disclosure Vulnerability
- CVE-2022-26788 PowerShell Elevation of Privilege Vulnerability
- CVE-2022-24533 Remote Desktop Protocol Remote Code Execution Vulnerability
- CVE-2022-24492 Remote Procedure Call Runtime Remote Code Execution Vulnerability
- CVE-2022-24528 Remote Procedure Call Runtime Remote Code Execution Vulnerability
- CVE-2022-26809 RPC Runtime Library Remote Code Execution Vulnerability
- CVE-2022-24482 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24540 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24494 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2022-24549 Windows AppX Package Manager Elevation of Privilege Vulnerability
- CVE-2022-26828 Windows Bluetooth Driver Elevation of Privilege Vulnerability
- CVE-2022-24484 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-24538 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-26784 Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability
- CVE-2022-24489 Windows Cluster Shared Volume (CSV) Elevation of Privilege Vulnerability
- CVE-2022-24481 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24521 Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24488 Windows Desktop Bridge Elevation of Privilege Vulnerability
- CVE-2022-24547 Windows Digital Media Receiver Elevation of Privilege Vulnerability
- CVE-2022-24495 Windows Direct Show – Remote Code Execution Vulnerability
- CVE-2022-26829 Windows DNS Elevation of Privilege Vulnerability
- CVE-2022-26816 Windows DNS Server Denial of Service Vulnerability
- CVE-2022-24536 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26811 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26812 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26813 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26815 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26818 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26819 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26820 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26821 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26822 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26823 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26824 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26825 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-26826 Windows DNS Server Remote Code Execution Vulnerability
- CVE-2022-24546 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-24527 Windows Endpoint Configuration Manager Elevation of Privilege Vulnerability
- CVE-2022-26808 Windows File Explorer Elevation of Privilege Vulnerability
- CVE-2022-26810 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
- CVE-2022-26827 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
- CVE-2022-26903 Windows Graphics Component Remote Code Execution Vulnerability
- CVE-2022-23268 Windows Hyper-V Denial of Service Vulnerability
- CVE-2022-22008 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-22009 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-23257 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-24537 Windows Hyper-V Remote Code Execution Vulnerability
- CVE-2022-24490 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-24539 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-26783 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-26785 Windows Hyper-V Shared Virtual Hard Disks Information Disclosure Vulnerability
- CVE-2022-24499 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-24530 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-24543 Windows Installer Remote Code Execution Vulnerability
- CVE-2022-24498 Windows iSCSI Target Service Information Disclosure
- CVE-2022-24486 Windows Kerberos Elevation of Privilege Vulnerability
- CVE-2022-24544 Windows Kerberos Elevation of Privilege Vulnerability
- CVE-2022-24545 Windows Kerberos Remote Code Execution Vulnerability
- CVE-2022-24483 Windows Kernel Information Disclosure Vulnerability
- CVE-2022-24487 Windows Local Security Authority Subsystem Service Remote Code Execution Vulnerability
- CVE-2022-24491 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-24497 Windows Network File System Remote Code Execution Vulnerability
- CVE-2022-26786 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26787 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26789 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26790 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26791 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26792 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26793 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26794 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26795 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26796 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26797 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26798 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26801 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26802 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-26803 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-21983 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24485 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24500 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24534 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24541 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-26830 Windows SMB Remote Code Execution Vulnerability
- CVE-2022-24550 Windows Telephony Server Elevation of Privilege Vulnerability
- CVE-2022-26904 Windows User Profile Service Elevation of Privilege Vulnerability
- CVE-2022-24474 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-24542 Windows Win32k Elevation of Privilege Vulnerability
- CVE-2022-26807 Windows Work Folder Service Elevation of Privilege Vulnerability
- CVE-2022-26914 Win32k Elevation of Privilege Vulnerability
- CVE-2022-26916 Windows Fax Compose Form Remote Code Execution Vulnerability
- CVE-2022-26917 Windows Fax Compose Form Remote Code Execution Vulnerability
- CVE-2022-26918 Windows Fax Compose Form Remote Code Execution Vulnerability
- CVE-2022-26920 Windows Graphics Component Information Disclosure Vulnerability
- CVE-2022-26919 Windows LDAP Remote Code Execution Vulnerability
- CVE-2022-26915 Windows Secure Channel Denial of Service Vulnerability