Patch Tuesday, November 2019 Edition
Credit to Author: BrianKrebs| Date: Tue, 12 Nov 2019 22:04:32 +0000
Microsoft today released updates to plug security holes in its software, including patches to fix at least 74 weaknesses in various flavors of Windows and programs that run on top of it. The November updates include patches for a zero-day flaw in Internet Explorer that is currently being exploited in the wild, as well as a sneaky bug in certain versions of Office for Mac that bypasses security protections and was detailed publicly prior to today’s patches.
 More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.
More than a dozen of the flaws tackled in this month’s release are rated “critical,” meaning they involve weaknesses that could be exploited to install malware without any action on the part of the user, except for perhaps browsing to a hacked or malicious Web site or opening a booby-trapped file attachment.
Perhaps the most concerning of those critical holes is a zero-day flaw in Internet Exploder Explorer (CVE-2019-1429) that has already seen active exploitation. Today’s updates also address two other critical vulnerabilities in the same Windows component that handles various scripting languages.
Microsoft also fixed a flaw in Microsoft Office for Mac (CVE-2019-1457) that could allow attackers to bypass security protections in some versions of the program that could let malicious macros through.
Macros are bits of computer code that can be embedded into Office files, and malicious macros are frequently used by malware purveyors to compromise Windows systems. Usually, this takes the form of a prompt urging the user to “enable macros” once they’ve opened a booby-trapped Office document delivered via email. Thus, Office has a feature called “disable all macros without notification.”
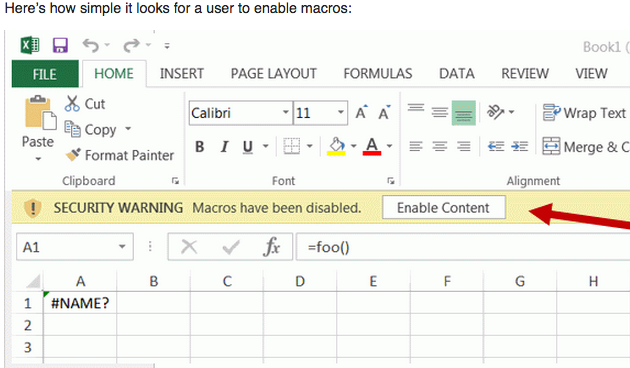
But Microsoft says all versions of Office still support an older type of macros that do not respect this setting, and can be used as a vector for pushing malware. Will Dornan of CERT/CC reports that while Office 2016 and 2019 for Mac will still prompt the user before executing these older macro types, Office for Mac 2011 fails to warn users before opening them.
Other Windows applications or components receiving patches for critical flaws today include Microsoft Exchange and Windows Media Player. In addition, Microsoft also patched nine vulnerabilities — five of them critical — in the Windows Hyper-V, an add-on to the Windows Server OS (and Windows 10 Pro) that allows users to create and run virtual machines (other “guest” operating systems) from within Windows.
Although Adobe typically issues patches for its Flash Player browser component on Patch Tuesday, this is the second month in a row that Adobe has not released any security updates for Flash. However, Adobe today did push security fixes for a variety of its creative software suites, including Animate, Illustrator, Media Encoder and Bridge. Also, I neglected to note last month that Adobe released a critical update for Acrobat/Reader that addressed at least 67 bugs, so if you’ve got either of these products installed, please be sure they’re patched and up to date.
Finally, Google recently fixed a zero-day flaw in its Chrome Web browser (CVE-2019-13720). If you use Chrome and see an upward-facing arrow to the right of the address bar, you have an update pending; fully closing and restarting the browser should install any available updates.
Now seems like a good time to remind all you Windows 7 end users that Microsoft will cease shipping security updates after January 2020 (this end-of-life also affects Windows Server 2008 and 2008 R2). While businesses and other volume-license purchasers will have the option to pay for further fixes after that point, all other Windows 7 users who want to stick with Windows will need to consider migrating to Windows 10 soon.
Standard heads-up: Windows 10 likes to install patches all in one go and reboot your computer on its own schedule. Microsoft doesn’t make it easy for Windows 10 users to change this setting, but it is possible. For all other Windows OS users, if you’d rather be alerted to new updates when they’re available so you can choose when to install them, there’s a setting for that in Windows Update. To get there, click the Windows key on your keyboard and type “windows update” into the box that pops up.
Keep in mind that while staying up-to-date on Windows patches is a good idea, it’s important to make sure you’re updating only after you’ve backed up your important data and files. A reliable backup means you’re probably not freaking out when the odd buggy patch causes problems booting the system. So do yourself a favor and backup your files before installing any patches.
As ever, if you experience glitches or problems installing any of these patches this month, please feel free to leave a comment about it below; there’s a decent chance other readers have experienced the same and may even chime in here with some helpful tips.